Search
Search Results
-
Bounds on data limits for all-to-all comparison from combinatorial designs
In situations where every item in a data set must be compared with every other item in the set, it may be desirable to store the data across a number...
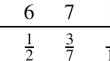
-
Model-Agnostic Utility-Preserving Biometric Information Anonymization
The recent rapid advancements in both sensing and machine learning technologies have given rise to the universal collection and utilization of...

-

-
Efficient quantum algorithms for some instances of the semidirect discrete logarithm problem
The semidirect discrete logarithm problem (SDLP) is the following analogue of the standard discrete logarithm problem in the semidirect product...
-
On duplication-free codes for disjoint or equal-length errors
Motivated by applications in DNA storage, we study a setting in which strings are affected by tandem-duplication errors. In particular, we look at...

-
Improved Approximation Algorithms by Generalizing the Primal-Dual Method Beyond Uncrossable Functions
We address long-standing open questions raised by Williamson, Goemans, Vazirani and Mihail pertaining to the design of approximation algorithms for...

-
Securesdp: a novel software-defined perimeter implementation for enhanced network security and scalability
Software-defined perimeters (SDP) revolutionize network security by offering dynamic and adaptive access controls, focusing on user and device...

-
BA-flag: a self-prevention mechanism of selfish mining attacks in blockchain technology
Selfish mining is when a group of miners in a blockchain system work together to cheat and get more rewards by hiding their work from others. This...

-

-
LCD codes and almost optimally extendable codes from self-orthogonal codes
LCD codes and (almost) optimally extendable codes can be used to safeguard against fault injection attacks (FIA) and side-channel attacks (SCA) in...
-
On Generalized Nega-Hadamard Transform and Nega-crosscorrelation
In the construction of cryptosystems, we need functions with some cryptographically significant properties. It is known that the Global Avalanche...
-
Decentralised identity federations using blockchain
Federated Identity Management offers numerous economic benefits and convenience to Service Providers and users alike. In such federations, the...

-
On optimal constant weight codes derived from \(\omega \)-circulant balanced generalized weighing matrices
Balanced generalized weight matrices are used to construct optimal constant weight codes that are monomially inequivalent to codes derived from the...
-
Multi-key and Multi-input Predicate Encryption (for Conjunctions) from Learning with Errors
We put forward two natural generalizations of predicate encryption (PE), dubbed multi-key and multi-input PE. More in details, our contributions are...

-
Two-stage advanced persistent threat (APT) attack on an IEC 61850 power grid substation
Advanced Persistent Threats (APTs) are stealthy, multi-step attacks tailored to a specific target. Often described as ’low and slow’, APTs remain...

-
Construction of DNA codes with multiple constrained properties
DNA sequences are prone to creating secondary structures by folding back on themselves by non-specific hybridization of its nucleotides. The...

-

-
Parameterized Approximation Algorithms and Lower Bounds for k-Center Clustering and Variants
k -center is one of the most popular clustering models. While it admits a simple 2-approximation in polynomial time in general metrics, the Euclidean...

