Search
Search Results
-
A Systematic Review of Identity and Access Management Requirements in Enterprises and Potential Contributions of Self-Sovereign Identity
Digital identity and access management (IAM) poses significant challenges for companies. Cyberattacks and resulting data breaches frequently have...

-
Stop me if you’ve heard this one before: Identity-based consumer responses to music in marketing contexts
The use of music in marketing campaigns is ubiquitous. Frequently, brands choose music that they think will be personally meaningful to consumers so...

-
Online User Reviews and Goal-Directed Consumer Behavior: A Qualitative Study
With the rapid growth of the Internet and the increasing ability of its users to generate and publish content, active online communities have...
-
Online Users’ Identity Theft and Co** Strategies, Attribution and Sense of Urgency: A Non-Linear Quadratic Effect Assessment
Defined as someone using other’s personally identifiable information to make profit or commit crimes, identity theft has become a critical problem...

-
A Two-Stage Authorship Attribution Method Using Text and Structured Data for De-Anonymizing User-Generated Content
User-generated content (UGC) is an important source of information on products and services for consumers and firms. Although incentivizing...

-
Brand user imagery clarity (BUIC): conceptualization, measurement, and consequences
Brand user imagery is an important aspect of brand association and, consequently, brand equity. Extant conceptualizations emphasize content features...

-
Leading With Clarity (Part 1—Understanding the Basics of Bias and Identity Bias)
Having developed a deep conviction in DEI, the authors explore what leading with clarity entails. Being aware of and clear about bias is particularly...
-
What impacts learning effectiveness of a mobile learning app focused on first-year students?
In recent years, the application of digital technologies for learning purposes is increasingly discussed as smartphones have become an integral part...

-
A Review of Anonymization Algorithms and Methods in Big Data
In the era of big data, with the increase in volume and complexity of data, the main challenge is how to use big data while preserving the privacy of...
-
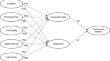
Sequential customer experiences leading to continuance intention in the mobile telecom industry: from contract to call center
In today's digital age, most individuals own smartphones and routinely use telecom services. As a result, understanding users' intentions to continue...
-
Toward Seamless Mobility-as-a-Service
With growing awareness of sustainability and convenience expectations, customers are increasingly demanding integrated and seamless mobility in the...

-
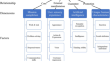
Service robots’ anthropomorphism: dimensions, factors and internal relationships
Robots have been widely used in social production, especially in the service industry. As their use continues to spread, their anthropomorphic...
-
Representing a Model for the Anonymization of Big Data Stream Using In-Memory Processing
In light of the escalating privacy risks in the big data era, this paper introduces an innovative model for the anonymization of big data streams,...

-
Importance of IT and Role Identities in Information Systems Infusion
Information systems (IS) should be infused into individuals’ work activities for organizations to extract value from these systems. Studies have...

-
Design Implementation and Academic Correlation for Harmonizing Contemporary Usage and Heritage of Bodo Traditional Attire
Dokhona, a traditional women’s attire of the Bodo Community of the northeast India, marks the community’s cultural and traditional identity besides...
-
Understanding the determinants of reviewer credibility: an interpretive structural modeling and artificial neural network approach
With the digitization of the tourism and hospitality sector, all hotel and travel bookings can be done online. Since the quality of experience is...

-
Privacy in the Digital Age: Navigating the Risks and Benefits of Cybersecurity Measures
This chapter provides an overview of privacy and cybersecurity, classifies, and describes various attack vectors, presents best practices to mitigate...
-
Blockchain adoption in food supply chain for new business opportunities: an integrated approach
Blockchain technology identifies and categorises product waste in supply chains, helps identify food contamination risks, and improves transit...

-
Digital Identity: A Case Study of the ProCIDA Project
The role of cloud computing in today’s world of globalization has seen as a major contribution for application development and deployment. Many...
-
Critical Success Factors for Emerging Technology Adoption, Strategic Flexibility, and Competitiveness: An Evidence-Based Total Interpretive Structural Modeling Approach (TISM-E)
In the dynamic business environment, firms can adopt emerging technologies to remain relevant and effectively meet changing customer demands. The...

