Search
Search Results
-

-
Smart contract vulnerabilities detection with bidirectional encoder representations from transformers and control flow graph
Up to now, the smart contract vulnerabilities detection methods based on sequence modal data and sequence models have been the most commonly used....

-
Survey-based analysis of cybersecurity awareness of Turkish seafarers
In recent years, vessels have become increasingly digitized, reflecting broader societal trends. As a result, maritime operations have become an...

-
Adaptive context-aware access control for IoT environments leveraging fog computing
The increasing use of the Internet of Things (IoT) has driven the demand for enhanced and robust access control methods to protect resources from...

-
Using the ACE framework to enforce access and usage control with notifications of revoked access rights
The standard ACE framework provides authentication and authorization mechanisms similar to those of the standard OAuth 2.0 framework, but it is...

-
A three-stage quality evaluation method for experience products: taking animation as an example
The diversity and dynamics of quality index information bring challenges to quality assessment of experience products. This paper proposes a...

-
Automating shareable cyber threat intelligence production for closed source software vulnerabilities: a deep learning based detection system
Software can be vulnerable to various types of interference. The production of cyber threat intelligence for closed source software requires...

-
Accurate entropy modeling in learned image compression with joint enchanced SwinT and CNN
Recently, learned image compression (LIC) has shown significant research potential. Most existing LIC methods are CNN-based or transformer-based or...

-
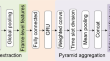
A multi-scale no-reference video quality assessment method based on transformer
Video quality assessment is essential for optimizing user experience, enhancing network efficiency, supporting video production and editing,...
-
ViCLEVR: a visual reasoning dataset and hybrid multimodal fusion model for visual question answering in Vietnamese
In recent years, visual question answering (VQA) has gained significant attention for its diverse applications, including intelligent car assistance,...

-
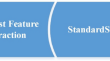
Deep learning based features extraction for facial gender classification using ensemble of machine learning technique
Accurate and efficient gender recognition is an essential for many applications such as surveillance, security, and biometrics. Recently, deep...
-
Vectorial negabent concepts: similarities, differences, and generalizations
In Pasalic et al. (IEEE Trans Inf Theory 69:2702–2712, 2023), and in Anbar and Meidl (Cryptogr Commun 10:235–249, 2018), two different vectorial...
-
Trust management in the internet of vehicles: a systematic literature review of blockchain integration
The Internet of Vehicles (IoV) promises to revolutionize transportation in smart cities, but its interconnectedness raises critical security and...

-
Blind quality evaluator for multi-exposure fusion image via joint sparse features and complex-wavelet statistical characteristics
Multi-Exposure Fusion (MEF) technique aims to fuse multiple images taken from the same scene at different exposure levels into an image with more...

-
Context-aware adaptive network for UDA semantic segmentation
Unsupervised Domain Adaptation (UDA) plays a pivotal role in enhancing the segmentation performance of models in the target domain by mitigating the...

-
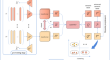
Deep contrastive multi-view clustering with doubly enhanced commonality
Recently, deep multi-view clustering leveraging autoencoders has garnered significant attention due to its ability to simultaneously enhance feature...
-
Expediting the design and development of secure cloud-based mobile apps
The adoption and popularity of mobile devices by end-users is partially driven by the increasing development and availability of mobile applications...

-
Quality evaluation methods of handwritten Chinese characters: a comprehensive survey
Quality evaluation of handwritten Chinese characters aims to automatically quantify and assess handwritten Chinese characters through computer vision...

