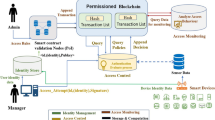
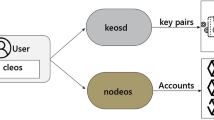
Abstract
Internet-of-Things (IoT) has become much more ubiquitous in the present era as numerous novel applications employing it with technical units are being adapted to interact with it. The minimal computing power of devices, the security concerns about their data, and the flexibility for on-demand scaling are the major constraints in preventing the effective application and evolution of IoT networks. To address these problems, a hybridized conceptual framework called ModChain is proposed that mutates blockchain structure to scale with IoT networking. The throughput of a typical blockchain network cannot handle the volume of data generated by scaling IoT networks. ModChain includes a customized deterministic consensus named, MoD-PoW that transforms the way the blockchain operates so that multiple data fragments can be mined. Throughput is increased by implementing a node committee which is responsible for appending blocks to the framework. A custom-built consensus algorithm is used to ensure the fairness property of mining, and the incentivization module has been defined to ensure that the leader of the committee does not compromise on a fake transaction. The advent of a Private Auction process has boosted network scalability. ModChain has an average transaction throughput of 883 Transactions Per Second (TPS).









Similar content being viewed by others
Data availability
Data sharing not applicable to this article as no datasets were generated or analysed during the current study.
References
Praveen R, Pabitha P (2023) A secure lightweight fuzzy embedder based user authentication scheme for internet of medical things applications. J Intell Fuzzy Syst 1–20. https://doi.org/10.3233/JIFS-223617
Jayabal CP, Sathia Bhama PR (2021) Performance analysis on diversity mining-based proof of work in bifolded consortium blockchain for Internet of Things consensus. Concurr Computat Pract Exp 33(16):e6285. https://doi.org/10.1002/cpe.6285
Li J, et al. (2020) Blockchain-based public auditing for big data in cloud storage. Inform Process Manag 57.6: 102382
Shah R, Rajagopal S (2022) M-DPS: a blockchain-based efficient and cost-effective architecture for medical applications. Int J Inf Technol 14(4):1909–1921
Batchu S, Henry OS, Hakim AA (2021) A novel decentralized model for storing and sharing neuroimaging data using ethereum blockchain and the interplanetary file system. Int J Inf Technol 13(6):2145–2151
Ramalingam P, Parameswaran P (2023) Improved Gentry–Halevi's fully homomorphic encryption‐based lightweight privacy preserving scheme for securing medical Internet of Things. Trans Emerg Telecommun Technol. https://doi.org/10.1002/ett.4732
Quamara S, Singh AK (2022) SChain: towards the quest for redesigning supply-chain by augmenting Blockchain for end-to-end management. Int J Inf Technol 14:2343–2354
Ray S, Mishra KN, Dutta S (2022) Detection and prevention of DDoS attacks on M-healthcare sensitive data: a novel approach. Int J Inf Technol 14(3):1333–1341
Du Kai Lei M, Huang J, ** T (2020) Groupchain: towards a scalable public blockchain in fog computing of IoT services computing. IEEE Transactions on Services Computing 13(2):252–262. https://doi.org/10.1109/TSC.2019.2949801
Wang T, Zhou J, Liu A, Bhuiyan MZA, Wang G, Jia W (2019) Fog-based computing and storage offloading for data synchronization in IoT. IEEE Internet of Things J 6(3):4272–4282. https://doi.org/10.1109/JIOT.2018.2875915
Wu D, Ansari N (2020) A cooperative computing strategy for blockchain-secured fog computing. IEEE Internet Things J 7(7):6603–6609. https://doi.org/10.1109/JIOT.2020.2974231
Kaladevi P, Sengathir J, Praveen R, Muthusankar D (2023) An improved ensemble classification-based secure two stage bagging pruning technique for guaranteeing privacy preservation of DNA sequences in electronic health records. J Intell Fuzzy Syst 44(1):149–166. https://doi.org/10.3233/JIFS-221615
Debe M, Salah K, Ur Rehman MH, Svetinovic D (2020) Monetization of services provided by public fog nodes using blockchain and smart contracts. IEEE Access 8:20118–20128. https://doi.org/10.1109/ACCESS.2020.2968573
Pan J, Wang J, Hester A, Alqerm I, Liu Y, Zhao Y (2019) EdgeChain: an edge-IoT framework and prototype based on blockchain and smart contracts. IEEE Internet Things J 6(3):4719–4732. https://doi.org/10.1109/JIOT.2018.2878154
Algarni SA, Eassa F, Almarhabi K, Almalaise A, Albassam E, Alsubhi K, Yamin M (2021) Blockchain-based secured access control in an IoT system. Appl Sci 11:1772
Le-Dang Q, Le-Ngoc T (2019) Scalable blockchain-based architecture for massive IoT reconfiguration. IEEE Can Conf Elect Comput Eng (CCECE) 2019:1–4. https://doi.org/10.1109/CCECE.2019.8861858
Sudhakar T, Ramalingam P, Jagatheswari S (2022) An improved proxy-vehicle-based authentication scheme for vehicular ad-hoc networks. Int J Inf Technol 14:2441–2449. https://doi.org/10.1007/s41870-022-00938-5
Lu J, Sun J, **ao R, ** S (2022) DIFCS: a secure cloud data sharing approach based on decentralized information flow control. Comput Secur 117:102678
Xu Y, Huang Y (2020) Segment blockchain: a size reduced storage mechanism for blockchain. IEEE Access 8:17434–17441. https://doi.org/10.1109/ACCESS.2020.2966464
Tahir M, Sardaraz M, Muhammad S, Saud Khan M (2020) a lightweight authentication and authorization framework for blockchain-enabled IoT network in health-informatics. Sustainability 12:6960
Zhou Q, Zheng K, Zhang K, Hou L, Wang X (2022) Vulnerability analysis of smart contract for blockchain-based iot applications: a machine learning approach. IEEE Internet Things J. https://doi.org/10.1109/JIOT.2022.3196269.
Zhao Y, Chang J (2022) Certificateless public auditing scheme with designated verifier and privacy-preserving property in cloud storage. Comput Netw 216:109270
Ma X, Ma J, Li H, Jiang Q, Gao S (2018) ARMOR: a trust-based privacy-preserving framework for decentralized friend recommendation in online social networks. Fut Gen Comput Syst 79:82–94
Priya JC, Choudhury T, Khanna A, Preethi R (2022) Blockchain-based transfer learning for health screening with digital anthropometry from body images. Netw Model Anal Health Inform Bioinform 11(1):1–18
Jiao Y, Wang P, Niyato D, Suankaewmanee K (2019) Auction mechanisms in cloud/fog computing resource allocation for public blockchain networks. IEEE Trans Parallel Distrib Syst 30(9): 1975–1989. https://doi.org/10.1109/TPDS.2019.2900238.
Sathia Bhama PR, Jayabal CP (2021) MetaInfoChain: Bi-layered blockchain consensus for metadata aggregation in IoT and cloud environments. Trans Emerg Telecommun Technol 32(12):e4362. https://doi.org/10.1002/ett.4362
Wu D, Ansari N (2021) A trust-evaluation-enhanced blockchain-secured industrial IoT system. IEEE Internet Things J 8(7):5510–5517. https://doi.org/10.1109/JIOT.2020.3030689
Khezr S, Yassine A, Benlamri R (2022) Towards a secure and dependable IoT data monetization using blockchain and fog computing. Cluster Comput. https://doi.org/10.1007/s10586-022-03669-1
Khan AA, Uddin M, Shaikh AA, Laghari AA, Rajput AE (2021) MF-ledger: blockchain hyperledger sawtooth-enabled novel and secure multimedia chain of custody forensic investigation architecture. IEEE Access 9:103637–103650. https://doi.org/10.1109/ACCESS.2021.3099037
Boo E, Kim J, Ko J (2022) LiteZKP: lightening zero-knowledge proof-based blockchains for IoT and edge platforms. IEEE Syst J 16(1):112–123. https://doi.org/10.1109/JSYST.2020.3048363
Dewangan NK, Chandrakar P (2022) Patient-centric token-based healthcare blockchain implementation using secure internet of medical things. In: IEEE Transactions on Computational Social Systems. https://doi.org/10.1109/TCSS.2022.3194872.
Cai L, Li Q, Liang X (2022) Application development: fundamentals of hyperledger fabric. In: Advanced Blockchain Technology (pp. 191–226). Springer, Singapore.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Pabitha, P., Priya, J.C., Praveen, R. et al. ModChain: a hybridized secure and scaling blockchain framework for IoT environment. Int. j. inf. tecnol. 15, 1741–1754 (2023). https://doi.org/10.1007/s41870-023-01218-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41870-023-01218-6