Abstract
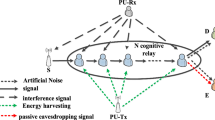
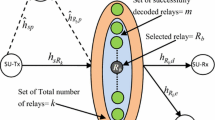
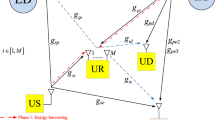
An unlicensed relay is located between an unlicensed sender and an unlicensed recipient for securing the sender’s message against a wire-tapper in underlay cognitive networks when the sender–recipient channel is inaccessible. The energy in the sender’s signals is harvested by the relay which utilizes that harvested energy for its signal transmission. To assess expeditiously the security capability, a precise formula of secrecy outage probability is suggested. This formula is then substantiated by computer simulations. Notably, the appropriate selection of system specifications including the time percentage, the relay’s location, the power percentage can drastically enhance the security capability of underlay cognitive relaying networks with energy harvesting. Also, the security capability is constant when one of two power curtailments of unlicensed senders (interference power curtailment and peak transmit power curtailment) is relaxed.







Similar content being viewed by others
Notes
In this paper, “transmitter”, “receiver”, “sender”, “recipient” are the short forms of “licensed transmitter”, “licensed receiver”, “unlicensed sender”, “unlicensed recipient”, respectively.
The possibility which the signal-to-noise ratio (SNR) is lower than a preset level is called the COP.
The PSCP is the likelihood which the secrecy capacity is positive [10].
The SOP is the likelihood which the secrecy capacity is lower than a predetermined security level [10].
In this paper, “direct transmission” or “direct communication” refers to the communication paradigm in which no relay is employed to connect the sender with the recipient.
In underlay cognitive networks, licensed transmitters beget interferences on unlicensed recipients. These interferences are ignorable because either they are assumed to follow the Gaussian distribution or the transmitter–recipient distance is sufficiently distant. The assumption on ignoring these interferences is quite common in researching the cognitive radio technology (e.g., [18,19,20] and references therein).
References
Ali, Z., Sidhu, G. A. S., et al. (2019). A joint optimization framework for energy harvesting based cooperative CR networks. IEEE Transactions on Cognitive Communications and Networking, 5(2), 452–462.
Miridakis, N. I., Tsiftsis, T. A., et al. (2017). Simultaneous spectrum sensing and data reception for cognitive spatial multiplexing distributed systems. IEEE Transactions on Wireless Communications, 16(5), 3313–3327.
Lei, H., Xu, M., et al. (2017). On secure underlay MIMO cognitive radio networks with energy harvesting and transmit antenna selection. IEEE Transactions on Green Communications and Networking, 1(2), 192–203.
Shi, H., Cai, Y., et al. (2019). Physical layer security in an untrusted energy harvesting relay network. IEEE Access, 7, 24819–24828.
Miridakis, N. I., Tsiftsis, T. A., et al. (2018). MIMO underlay cognitive radio: Optimized power allocation, effective number of transmit antennas and harvest-transmit tradeoff. IEEE Transactions on Green Communications and Networking, 2(4), 1101–1114.
Mishra, D., & Alexandropoulos, G. C. (2018). Transmit precoding and receive power splitting for harvested power maximization in MIMO SWIPT systems. IEEE Transactions on Green Communications and Networking, 2(3), 774–786.
Wyner, A. D. (1975). The wire-tap channel. Bell System Technical Journal, 54(8), 1355–1387.
Quang, P. M., Duy, T. T., et al. (October, 2016). Performance evaluation of underlay cognitive radio networks over Nakagami-m fading channels with energy harvesting. In Proceedings of the IEEE international conference on advanced technologies for communications, HaNoi, Vietnam, 10–12 (pp. 108–113).
Zhang, J., Pan, G., et al. (2016). On physical-layer security in underlay cognitive radio networks with full-duplex wireless-powered secondary system. IEEE Access, 4, 3887–3893.
Alexandropoulos, G. C., & Peppas, K. P. (2018). Secrecy outage analysis over correlated composite Nakagami-\(m\)/Gamma fading channels. IEEE Communications Letters, 22(1), 77–80.
Mou, W., Yang, W., et al. (October, 2016). Secure transmission in spectrum-sharing cognitive networks with wireless power transfer. In Proceedings of the IEEE international conference on wireless communications and signal processing, JiangSu, China, 13–15, pp. 1–5.
Lei, H., Xu, M., et al. (December, 2016). Secrecy outage performance for underlay MIMO CRNs with energy harvesting and transmit antenna selection. In Proceedings of the IEEE global communications conference, Washington DC, USA, 4–8, pp. 1–6.
Singh, A., Bhatnagar, M. R., et al. (2016). Secrecy outage of a simultaneous wireless information and power transfer cognitive radio system. IEEE Wireless Communications Letters, 5(3), 288–291.
Liu, Y., Wang, L., et al. (2016). Secure D2D communication in large-scale cognitive cellular networks: a wireless power transfer model. IEEE Transactions on Communications, 64(1), 329–342.
Raghuwanshi, S., Maji, P., et al. (September, 2016). Secrecy performance of a dual hop cognitive relay network with an energy harvesting relay. In Proceedings of the IEEE international conference on advances in computing, communications and informatics, Jaipur, India, 21–24, pp. 1622–1627.
Zhou, X., Zhang, R., et al. (2013). Wireless information and power transfer: Architecture design and rate-energy trade-off. IEEE Transactions on Communications, 61(11), 4754–4767.
Nasir, A. A., Zhou, X., et al. (2013). Relaying protocols for wireless energy harvesting and information processing. IEEE Transactions on Wireless Communications, 12(7), 3622–3636.
Zhang, X., **ng, J., et al. (2013). Outage performance study of cognitive relay networks with imperfect channel knowledge. IEEE Communications Letters, 17(1), 27–30.
Seyfi, M., Muhaidat, S., et al. (2013). Relay selection in cognitive radio networks with interference constraints. IET Communications, 7(10), 922–930.
Nguyen, M., Nguyen, N., et al. (2017). Secure cooperative half-duplex cognitive radio networks with \(K\)-th best relay selection. IEEE Access, 5, 6678–6687.
Zhao, R., Yuan, Y., et al. (2017). Secrecy performance analysis of cognitive decode-and-forward relay networks in Nakagami-\(m\) fading channels. IEEE Transactions on Communications, 65(2), 549–563.
Biglieri, E., Proakis, J., et al. (1998). Fading channels: information-theoretic and communications aspects. IEEE Transactions on Information Theory, 44(6), 2619–2692.
Zou, Y., Wang, X., et al. (2013). Physical-layer security with multiuser scheduling in cognitive radio networks. IEEE Transactions on Communications, 61(12), 5103–5113.
Acknowledgments
This research is funded by Vietnam National University HoChiMinh City (VNU-HCM) under grant number B2019-20-01.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ho-Van, K., Do-Dac, T. Security Performance of Underlay Cognitive Relaying Networks with Energy Harvesting. Wireless Pers Commun 110, 829–846 (2020). https://doi.org/10.1007/s11277-019-06758-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06758-4