Abstract
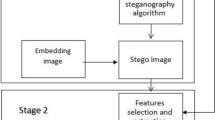
Steganalysis is a known practice to detect hidden secrecy within covered e-media. Researches claimed obscured detection attainability via features extraction, as for perceiving concealed data within images. This paper verifies practicality of the claim by testing investigation of a steganalysis system that depicts the existence of hidden data focused on statistical features of color images using artificial neural network techniques. The proposed system is built to work for blind image steganalysis representing common security as looked for the most. The work experimentations adopted common steganography techniques to create the stego images for our intended steganalysis challenging practicality evaluation. The study involved machine learning radial basis function and naïve bayes classifiers to sort the remarks improving discovery accuracy. From the investigational results, the proposed system exemplified reliability and enhancements in the recognition rate for most steganographic methods showing attractive annotations. Further, the correlation features displayed increased correctness showing reliable convalescing practicality overcoming many previous steganalysis defects.






Similar content being viewed by others
Data availability
Data sharing not applicable—no new data generated.
References
Abu-Hashem M et al (2022) Efficient computation of Hash Hirschberg protein alignment utilizing hyper threading multi-core sharing technology. CAAI Transact Intell Technol 7(2):278–291
Abu-Hashem M et al. (2023) Discrepancies of remote techno-tolerance due to COVID-19 pandemic within Arab middle-east countries. J Umm Al-Qura Univ Eng Archit. Springer. in press. https://doi.org/10.1007/s43995-023-00026-0
Aljarf A (2016) Development of a detection system for colour steganographic images based on extraction of colour gradient co-occurrence matrix features and histogram of difference image, PhD Thesis from Computer Sciences at Coventry University, UK.
Aljarf A et al. (2023). Is blind image steganalysis practical using feature-based classification?. Multimedia tools and applications (MTAP), in press. https://doi.org/10.1007/s11042-023-15682-6
Al-Taie Z (2017) Statistical steganalysis detector model for 8-bit depth images. Unpublished master thesis, Middle East University, Amman, Jordan.
Anderson R, Petitcolas F (1989) On the limits of steganography. IEEE J Sel Areas Commun 16(4):474–481
Dong J, and Tan T 2008 Blind image steganalysis based on run-length histogram analysis. IEEE International conference on image processing, pp. 2064–2067, San Diego, CA, USA. https://doi.org/10.1109/ICIP.2008.4712192
Duric Z, Jacobs M and Jajodia S (2004). Information hiding: steganography and steganalysis. Preprint Submitted to Elsevier Science.
Eichkitz C et al. (2015). Grey level co-occurrence matrix and its application to seismic data. First break. 33(3).
Fawcett T (2004) ROC graphs: notes and practical considerations for researchers. Mach Learn 31(1):1–38
Fridrich J, Goljan M and Du R (2001). Reliable detection of LSB steganography in grayscale and color images. Proceeding of ACM, special session on multimedia security and watermarking, Ottawa, Canada, pp. 27–30.
Gutub A, Al-Qurashi A (2020) Secure shares generation via M-blocks partitioning for counting-based secret sharing. J Eng Res (JER) 8(3):91–117
Gutub A, Al-Roithy B (2021) Varying PRNG to improve image cryptography implementation. J Eng Res 9(3A):153–183
Gutub A, Almehmadi E (2022) Arabic text watermarking tuned for medical e-record semi-authentication. J Eng Res. https://doi.org/10.36909/jer.18943
Gutub A, Shambour M, Abu-Hashem M (2022) Coronavirus impact on human feelings during 2021 hajj season via deep learning critical twitter analysis. J Eng Res (JER). https://doi.org/10.3690/jer.19493
Gutub A (2022) Dynamic smart random preference for higher medical image confidentiality. J Eng Res. https://doi.org/10.3690/jer.17853
Hammad B, Ahmed I, Jamil N (2022) A steganalysis classification algorithm based on distinctive texture features. Symmetry 14(2):236. https://doi.org/10.3390/sym14020236
Hemalatha J et al (2023) Towards improving the performance of blind image steganalyzer using third-order SPAM features and ensemble classifier. J Inf Secur Appl 76:103541. https://doi.org/10.1016/j.jisa.2023.103541
Hossain K and Parekh R (2010) Extending GLCM to include color information for texture recognition. Am Inst Phys (AIP) Conf Proc. 1298(1).
Huayong G, Mingshenge H and Qiana W (2011) Steganography and steganalysis based on digital image. International congress on image and signal processing, Shanghai, China.
Hussain M, Abdul-Wahab A, Idris Y, Ho A, Ki-Hyun J (2018) Image steganography in spatial domain: a survey. Signal Process Image Commun 65:46–66
** Z, Feng G, Ren Y, Zhang X (2020) Feature extraction optimization of JPEG steganalysis based on residual images. Signal Process 170:107455
Johnson N, Jajodia S (1998) Exploring steganography: seeing the unseen. Computer 31(2):26–34
Jyothy T, Sreelatha G, Pradeep R and Sajith V (2019). Texture-based multiresolution steganalytic features for spatial image steganography. International conference on smart systems and inventive technology (ICSSIT), Tirunelveli, India, pp. 966–971.
Kekre H, Athawale A, Patki S (2011) Steganalysis of LSB embedded images using gray level co-occurrence matrix. Int J Image Process (IJIP) 5(1):36
Kheshaifaty N, Gutub A (2021) Engineering graphical captcha and AES crypto hash functions for secure online authentication. J Eng Res. https://doi.org/10.36909/jer.13761
Kumar P, Vs D (2016) Extraction of texture features using GLCM and shape features using connected regions. Int J Eng Technol 8(6):2926–2930
Kunal H, Parekh R (2010) Extending GLCM to include color information for texture recognition. AIP Conf Proc 1298:583. https://doi.org/10.1063/1.3516370
Lin Q, Liu J and Guo Z (2016). Local ternary pattern based on path integral for steganalysis. IEEE international conference on image processing (ICIP), Phoenix, AZ, USA, pp. 2737–2741.
Ming C and Ru Z (2006). Analysis of current steganography tools: Classifications and features. Int Conf Intell Inform Hiding Multimed Signal Process.
Morkel T, Eloff J and Olivier M (2005). An overview of image steganography. ISSA. 1(2).
Provos N, Honeyman P (2003) Hide and seek: an introduction to steganography. IEEE Secur Priv 1(3):32–44
Qin J, **ang X, Deng Y, Li Y, Pan L (2014) Steganalysis of highly undetectable steganography using convolution filtering. Inf Technol J 13:2588
Raja K, Chowdary C, Venugopal K and Patnaik L (2005). A secure image steganography using LSB, DCT and compression techniques on raw images. IEEE Int Conf Intell Sens Inform Process, pp. 170–176.
Rasool Z, Al-Jarrah M, Amin S (2018) Steganalysis of RGB images using merged statistical features of color channels. Int Conf Dev eSyst Eng (DeSE). https://doi.org/10.1109/DeSE.2018.00048
Roslan NA et al (2022) Systematic literature review and analysis for Arabic text steganography method practically. Egypt Inform J 23(4):177–191
Roy PK et al (2023) Analysis of community question-answering issues via machine learning and deep learning: state-of-the-art review. CAAI Transact Intell Technol 8(1):95–117
Saritas M, Yasar A (2019) Performance analysis of ANN and Naive Bayes classification algorithm for data classification. Int J Intell Syst Appl Eng 7(2):88–91
Shambour MK, Gutub A (2021) Personal privacy evaluation of smart devices applications serving Hajj and Umrah rituals. J Eng Res. https://doi.org/10.36909/jer.13199
Shankar D, Azhakath A (2021) Minor blind feature based Steganalysis for calibrated JPEG images with cross validation and classification using SVM and SVM-PSO. Multimed Tools Appl 80(3):4073–4092
Shniperov A and Prokofieva A (2019) Steganalysis method of static JPEG images based on artificial immune system. Int Conf Secur Inform Netw. pp. 1–7.
Singh A et al (2022) AI-based mobile edge computing for IoT: applications, challenges, and future scope. Arab J Sci Eng (AJSE) 47(8):9801–9831
Singh A et al. (2023) Redefining food safety traceability system through blockchain: findings, challenges and open issues. Multimedia Tools Appl (MTAP), in press. https://doi.org/10.1007/s11042-022-14006-4
Sufi F et al (2023) Automating global threat-maps generation via advancements of news sensors and AI. Arab J Sci Eng (AJSE) 48(2):2455–2472
Sun Z, Hui M and Guan C (2008) Steganalysis based on co-occurrence matrix of differential image. IEEE Int Conf Intell Inform Hiding Multimed Signal Process.
Sun Z, Kai L and Zhongyi L (2019) Prediction of concrete compressive strength based on principal component analysis and radial basis function neural network. IOP Conf Series Mater Sci Eng. 677 (2).
Thabit R et al (2022) CSNTSteg: color spacing normalization text steganography model to improve capacity and invisibility of hidden data. IEEE Access 10:65439–65458
Thangadurai K and Devi G (2014) An analysis of LSB based image steganography techniques. IEEE Int Conf Comput Commun Inform.
Umamaheswari M, Sivasubramanian S, Pandiarajan S (2010) Analysis of different steganographic algorithms for secured data hiding. Int J Comput Sci Netw Secur 10(8):154–160
Verma A (2014) A non-blind steganalysis through neural network approach. Int J Multidiscip Consort 1(1):1–13
Zebari R (2020) A comprehensive review of dimensionality reduction techniques for feature selection and feature extraction. J Appl Sci Technol Trends 1(2):56–70
Zhang T and **jian P (2003) Reliable detection of LSB steganography based on the difference image histogram. IEEE Int Conf Acoust, Speech, Signal Process. 3.
Zielińska E, Mazurczyk W, Szczypiorski K (2014) Trends in steganography. Commun ACM 57(3):86–95
Acknowledgements
The authors would like to express their gratitude toward Umm Al-Qura University (UQU), Saudi Arabia, for the support of this study. The authors declare that this work is original and is not considered to be published in any other publication media.
Funding
Authors herby that this work received no external funding.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Ethical approval
The authors declare that the article does not contain any studies involve human participants or/and animals.
Informed consent
Authors herby that informed consent was obtained from all individual participants involved in the study.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Aljarf, A., Zamzami, H. & Gutub, A. Integrating machine learning and features extraction for practical reliable color images steganalysis classification. Soft Comput 27, 13877–13888 (2023). https://doi.org/10.1007/s00500-023-09042-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-023-09042-7