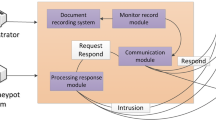
Abstract
A DDoS attack or distributed denial of service attack is an attempt to make servers unavailable by concentrating the target server with a flood of network traffic. DDoS attacks can cause huge financial loss to businesses. There are different types of DDoS attacks such as SYN flood, Smurf attack, ** of Death, and Buffer Overflow. Implementing the firewall and honeypot in the network can help us mitigate the effect of the attacks and analyze the attacker’s identity and signature. Our paper proposes an architecture which uses a packet generator, a firewall, and a honeypot to mitigate the DDoS attacks when it is happening at the target’s endpoint. We demonstrate and discuss these attacks as well as the methods used to block malicious packets. We have simulated multiple attack scenarios and mitigated them with the help of various firewall rules. These blocked packets are later used for analysis in the honeypot.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Campbell RM, Padayachee K, Masombuka T (2015) A survey of honeypot research: trends and opportunities. In: 2015 10th international conference for internet technology and secured transactions (ICITST). https://doi.org/10.1109/icitst.2015.7412090
Weiler N (n.d) Honeypots for distributed denial-of-service attacks. In: Proceedings of eleventh IEEE international workshops on enabling technologies: infrastructure for collaborative enterprises (n.d.). https://doi.org/10.1109/enabl.2002.1029997
Bailey M, Cooke E, Jahanian F, Provos N, Rosaen K, Watson D (2005) Data reduction for the scalable automated analysis of distributed darknet traffic. In: Proceedings of the 5th ACM SIGCOMM conference on internet measurement—IMC ’05. https://doi.org/10.1145/1330107.1330135
Templeton SJ, Levitt KE (n.d.) Detecting spoofed packets. In: Proceedings DARPA information survivability conference and exposition. https://doi.org/10.1109/discex.2003.1194882
Bringer ML, Chelmecki CA, Fu**oki H (2012) A survey: recent advances and future trends in honeypot research. Int J Comput Netw Inf Secur 4(10):63–75. https://doi.org/10.5815/ijcnis.2012.10.07
Yu A, Oyama Y (2009) Malware analysis system using process-level virtualization. In: 2009 IEEE symposium on computers and communications. https://doi.org/10.1109/iscc.2009.5202313
Alberdi I, Philippe É, Vincent O, Kaâniche NM (2012) Shark: spy honeypot with advanced redirection kit. In: Proceedings of the IEEE workshop on monitoring, attack detection and mitigation. Available http://spiderman-2.laas.fr/METROSEC/monam.pdf. Last accessed 17 Aug 2012
Anagnostakis KG, Sidiroglou S, Akritidis P, **nidis K, Markatos E, Keromytis AD (2005) Detecting targeted attacks using shadow honeypots. In: Proceedings of the conference on USENIX security symposium, pp 9-23
Dandamudi S, Eltaeib T (2015) Firewalls implementation in computer networks and their role in network security. J Multi Eng Sci Technol (JMEST) ISSN: 3159-0040, 2(3), March - 2015
Douligeris C, Mitrokotsa A (2004) DDoS attacks and defense mechanisms: classification and state-of-the-art. Comput Netw 44(5):643–666. https://doi.org/10.1016/j.comnet.2003.10.003
Biondi Philippe (2005) Scapy: explore the net with new eyes. Technical report, EADS Corporate Research Center
pfSense Project (2004). https://docs.netgate.com/pfsense/en/latest
McKinney W (2011) pandas: a foundational Python library for data analysis and statistics. Python High Perform Sci Comput 14(9):1–9
Van der Walt S, Colbert SC, Varoquaux G (2011) The NumPy array: a structure for efficient numerical computation. Comput Sci Eng 13(2):22–30. https://doi.org/10.1109/mcse.2011.37
Giacobbi G (2014) The GNU Netcat project. http://netcat.sourceforge.net
Orebaugh Angela, Ramirez Gilbert, Beale Jay (2006) Wireshark and ethereal network protocol analyzer toolkit. Elsevier. https://doi.org/10.1016/b978-159749073-3/50015-4
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Harikrishnan, V., Sanket, H.S., Sahazeer, K.S., Vinay, S., Honnavalli, P.B. (2022). Mitigation of DDoS Attacks Using Honeypot and Firewall. In: Gupta, D., Polkowski, Z., Khanna, A., Bhattacharyya, S., Castillo, O. (eds) Proceedings of Data Analytics and Management . Lecture Notes on Data Engineering and Communications Technologies, vol 91. Springer, Singapore. https://doi.org/10.1007/978-981-16-6285-0_50
Download citation
DOI: https://doi.org/10.1007/978-981-16-6285-0_50
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-16-6284-3
Online ISBN: 978-981-16-6285-0
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)