Abstract
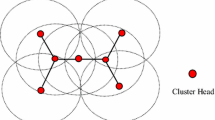
This paper presents a mechanism to maintain node integrity of decentralised systems consisted of nodes or microservices. The mechanism addresses total counts of nodes or micro-services in a decentralised systems. The proposed mechanism is a further development of a decentralised security model named Ki-Ngā-Kōpuku. Decentralised systems where the total number of active nodes matters to maintain the integrity of the system, it is important for the nodes to form a closed group among the valid nodes; as well as be aware of any node that becomes inactive or of any foreign node that may want to join the closed group of nodes. The nodes of a decentralised system need to be aware of the members of other nodes in the same group of nodes, and need to be able to raise alarm in the event of any changes in total number of nodes for whatever is the reason. The mechanism presented in this paper is a proposed solution to maintain integrity of a decentralised system in terms of number of nodes. The mechanism relies on beacon transmission to achieve its goal. The concept of the proposed mechanism applies to other contexts, for example, where a system consists of multiple micro-services.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Lasi H, Fettke P, Kemper H, Feld T, Hoffmann M (2014) Industry 4.0. Bus Inf Syst Eng 6(4):239–242. https://doi.org/10.1007/s12599-014-0334-4
Haseeb M, Hussain H, Ślusarczyk B, Jermsittiparsert K (2019) Industry 4.0: a solution towards technology challenges of sustainable business performance. Soc Scie 8(5):154. https://doi.org/10.3390/socsci8050154
Farwell J, Rohozinski R (2011) Stuxnet and the future of cyber war. Survival 53(1):23–40. https://doi.org/10.1080/00396338.2011.555586
Trautman LJ, Ormerod PC (2017) Industrial cyber vulnerabilities: lessons from Stuxnet and the Internet of Things. U Miami L Rev 72:761
Falliere N, Murchu LO, Chien E (2011) W32. stuxnet dossier. In: White paper, symantec corp., security response, vol 5, no 6, p 29
Ahmed M (2018) Ki-Ngā-Kōpuku: a decentralised, distributed security model for cloud computing. Auckland University of Technology
Fanaeepour M, Kangavari M (2010) Malicious node detection system in wireless sensor networks: a decentralised approach. Int J Internet Technol Secured Trans 2(12):88. https://doi.org/10.1504/ijitst.2010.031473
Dong P et al (2020) Edge computing based healthcare systems: enabling decentralized health monitoring in internet of medical things. IEEE Netw 34(5):254–261. https://doi.org/10.1109/MNET.011.1900636
Bengio Y et al (2021) Inherent privacy limitations of decentralized contact tracing apps. J Am Med Inf Assoc 28(1):193–195. https://doi.org/10.1093/jamia/ocaa153
Hao Y, Duan Z, Chen G (2018) Decentralised fixed modes of networked MIMO systems. Int J Control 91(4):859–873. https://doi.org/10.1080/00207179.2017.1295318
Melekhova O, Malenfant J, Mescheriakov R, Chueshev A (2018) A decentralised solution for coordinating decisions in large-scale autonomic systems. In: MATEC web of conferences, vol 161, p 03024. https://doi.org/10.1051/matecconf/201816103024
Chen Y, Zhao G, Li A, Deng B, Li X (2009) Handling node churn in decentralised network coordinate system. IET Commun 3(10):1578. https://doi.org/10.1049/iet-com.2008.0671
Hurst W, Shone N, El Rhalibi A, Happe A, Kotze B, Duncan B (2017) Advancing the micro-CI testbed for IoT cyber-security research and education. Cloud Comput 2017:139
Waller A, Craddock R (2011) Managing runtime re-engineering of a System-of-Systems for cyber security. In: 2011 6th International conference on system of systems engineering, pp 13–18. https://doi.org/10.1109/SYSOSE.2011.5966566
Raje S, Vaderia S, Wilson N, Panigrahi R (2017) Decentralised firewall for malware detection. In: 2017 International conference on advances in computing, communication and control (ICAC3), pp 1–5. https://doi.org/10.1109/ICAC3.2017.8318755
Li H, Venugopal S (2013) Efficient node bootstrap** for decentralised shared-nothing key-value stores. Middleware 2013:348–367. https://doi.org/10.1007/978-3-642-45065-5_18
Wood G (2014) Ethereum: a secure decentralised generalised transaction ledger. In: Ethereum Project yellow paper, vol 151, no 2014, pp 1–32
Khan M, Lawal I (2020) Sec-IoT: a framework for secured decentralised IoT using blockchain-based technology. In: Proceedings of fifth international congress on information and communication technology, pp 269-277. https://doi.org/10.1007/978-981-15-5856-6_27
Tejaswini B, Ashwini S, Shilpashree S (2018) Protected Data Reclamation for decentralised disruption-forbearing In wireless sensor network. Int J Eng Res Technol (IJERT)
Manfredi S, Di Tucci E A decentralised topology control to regulate global properties of complex networks. Eur Phys J B 90(4):https://doi.org/10.1140/epjb/e2017-70586-9
Xu Y, Huang Y (2020) An n/2 byzantine node tolerate blockchain sharding approach. In: Proceedings of the 35th annual ACM symposium on applied computing. https://doi.org/10.1145/3341105.3374069
Lin C, Shen Z, Chen Q, Sheldon F (2017) A data integrity verification scheme in mobile cloud computing. J Netw Comput Appl 77:146–151. https://doi.org/10.1016/j.jnca.2016.08.017
Spathoulas G et al (2018) Towards reliable integrity in blacklisting: facing malicious IPs in GHOST smart contracts. Innov Intell Syst Appl (INISTA) 2018:1–8. https://doi.org/10.1109/INISTA.2018.8466327
Schiffman J, Moyer T, Shal C, Jaeger T, McDaniel P (2009) Justifying integrity using a virtual machine verifier. In: Annual computer security applications conference, pp 83–92. https://doi.org/10.1109/ACSAC.2009.18
Altulyan M, Yao L, Kanhere S, Wang X, Huang C (2020) A unified framework for data integrity protection in people-centric smart cities. Multimedia Tools Appl 79(7–8):4989–5002. https://doi.org/10.1007/s11042-019-7182-7
Ezéchiel K, Ojha S, Agarwal R (2020) A new eager replication approach using a non-blocking protocol over a decentralized P2P architecture. Int J Distrib Syst Technol 11(2):69–100. https://doi.org/10.4018/ijdst.2020040106
Ghanati G, Azadi S (2020) Decentralized robust control of a vehicle’s interior sound field. J Vibr Control 26(19–20):1815–1823. https://doi.org/10.1177/1077546320907760
Sumathi M, Sangeetha S (2020) Blockchain based sensitive attribute storage and access monitoring in banking system. Int J Cloud Appl Comput 10(2):77–92. https://doi.org/10.4018/ijcac.2020040105
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 Springer Nature Switzerland AG
About this chapter
Cite this chapter
Ahmed, M., Bhuiyan, M.M.A. (2022). A Mechanism to Maintain Node Integrity in Decentralised Systems. In: Jiang, R., et al. Big Data Privacy and Security in Smart Cities. Advanced Sciences and Technologies for Security Applications. Springer, Cham. https://doi.org/10.1007/978-3-031-04424-3_4
Download citation
DOI: https://doi.org/10.1007/978-3-031-04424-3_4
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-04423-6
Online ISBN: 978-3-031-04424-3
eBook Packages: Physics and AstronomyPhysics and Astronomy (R0)