Abstract
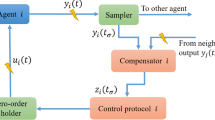
This paper is concerned with the resilient consensus control problem of the linear multi-agent system under the false data injection attacks, where each agent may receive the injected false data by attackers from its neighbours through communication links. Due to the existence of the false data, the desired consensus of multi-agent can not be reached by the general distributed consensus algorithms. By constructing an extended state observer to estimate the state and the injected false data towards each agent, a distributed resilient consensus control algorithm is designed to offset the negative effect of the attacks. Firstly, a sufficient condition is derived for the undirected multi-agent system under a bounded and decaying false data injection. Secondly, a sufficient and necessary condition is provided for the directed multi-agent system under the false data injection with decaying rate. Finally, the simulation results illustrate the effectiveness of the proposed consensus algorithms against the false data attacks.
Similar content being viewed by others
References
R. Olfati-Saber and R. M. Murray, “Consensus problems in networks of agents with switching topology and time-delays,” IEEE Transactions on Automatic Control, vol. 49, no. 9, pp. 1520–1533, 2004.
R. Olfati-Saber. “Flocking for multi-agent dynamic systems: Algorithms and theory,” IEEE Transactions on Automatic Control, vol. 51, no. 3, pp. 401–420, 2006.
M. Sharf, A. Koch, D. Zelazo, and F. Allgower, “Modelfree practical cooperative control for diffusively coupled systems,” IEEE Transactions on Automatic Control, vol. 67, no. 2, pp. 754–766, 2021.
R. Kavikumar, R. Sakthivel, and Y. Liu, “Design of H∞-based sampled-data control for fuzzy Markov jump systems with stochastic sampling,” Nonlinear Analysis: Hybrid Systems, vol. 41, 101041, 2021.
G. Zhao and C. Hua, “Sampled-Data leaderless and leader-following consensus of multiagent systems under nonidentical packet losses,” IEEE Transactions on Network Science and Engineering, vol. 9, no. 2, pp. 795–806, 2021.
K. Griparic, M. Polic, M. Krizmancic, and S. Bogdan, “Consensus-based distributed connectivity control in multi-agent systems,” IEEE Transactions on Network Science and Engineering, vol. 9, no. 3, pp. 1264–1281, 2022.
W. Qi, G. Zong, J. Park, and C. K. Ahn, “Input-output finite-time ssynchronous SMC for nonlinear semi-Markov switching systems with application,” IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 52, no. 8, pp. 5344–5353, 2022.
A. Parivallal, R. Sakthivel, R. Amsaveni, F. Alzahrani, and A. S. Alshomrani, “Observer-based memory consensus for nonlinear multi-agent systems with output quantization and Markov switching topologies,” Physica A: Statistical Mechanics and Its Applications, vol. 551, 123949, 2020.
W. He, Z. Mo, Q. Han, and F. Qian, “Secure impulsive synchronization in lipschitz-type multi-agent systems subject to deception attacks,” IEEE/CAA Journal of Automatica Sinica, vol. 7, no. 5, pp. 1326–1334, 2020.
J. Cheng, Y. Wang, J. H. Park, J. Cao, and K. Shi, “Static output feedback quantized control for fuzzy Markovian switching singularly perturbed systems with deception attacks,” IEEE Transactions on Fuzzy Systems, vol. 30, no. 4, pp. 1036–1047, 2021.
Z. Fei, X. Wang, and Z. Wang, “Event-based fault detection for unmanned surface vehicles subject to denial-of-service attacks,” IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 52, no. 5, pp. 3326–3336, 2022.
J. Qin, M. Li, L. Shi, and X. Yu, “Optimal denial-of-service attack scheduling with energy constraint over packet-drop** networks,” IEEE Transactions on Automatic Control, vol. 63, no. 6, pp. 1648–1663, 2017.
Y. Liu and G. H. Yang, “Resilient event-triggered distributed state estimation for nonlinear systems against DoS attacks,” IEEE Transactions on Cybernetics, vol. 52, no. 9, pp. 9076–9089, 2022.
H. Ni, Z. Xu, J. Cheng, and D. Zhang, “Robust stochastic sampled-data-based output consensus of heterogeneous multi-agent systems subject to random DoS attack: A Markovian jum** system approach,” International Journal of Control, Automation, and Systems, vol. 17, pp. 1687–1698, 2019.
H. Zhang, C. Peng, S. Ling, and J. Chen, “Optimal DoS attack scheduling in wireless networked control system,” IEEE Transactions on Control Systems Technology, vol. 24, no. 3, pp. 843–852, 2015.
L. Sun, Y. Zhang, and C. Sun, “Stochastic denial-of-service attack allocation in leader-following multiagent systems,” IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol.52, no. 5, pp. 2848–2857, 2022.
C. Persis and P. Tesi, “Input-to-state stabilizing control under denial-of-service,” IEEE Transactions on Automatic Control, vol. 60, no. 11, pp. 2930–2944, 2015.
M. Wakaiki, A. Cetinkaya, and H. Ishii, “Stabilization of networked control systems under DoS attacks and output quantization,” IEEE Transactions on Automatic Control, vol. 65, no. 8, pp. 3560–3575, 2019.
G. K. Befekadu, V. Gupta, and P. J. Antsaklis, “Risk-sensitive control under markov modulated denial-of-service (DoS) attack strategies,” IEEE Transactions on Automatic Control, vol. 60, no. 12, pp. 3299–3304, 2015.
T. Li, B. Chen, L. Yu, and W. Zhang, “Active security control approach against DoS attacks in cyber-physical systems,” IEEE Transactions on Automatic Control, vol. 66, no. 9, pp. 4303–4310, 2021.
P. Zeng, F. Deng, X. Liu, and X. Gao, “Event-triggered resilient L∞ control for Markov jump systems subject to denial-of-service jamming attacks,” IEEE Transactions on Cybernetics, vol. 52, no. 10, pp. 10240–10252, 2022.
H. He, Y. Chen, W. Qi, M. Wang, and X. Chen, “Observer-based resilient control of positive systems with heterogeneous DoS attacks: A Markov model approach,” Journal of the Franklin Institute, vol. 359, no. 1, pp. 272–293, 2022.
R. Deng, G. **ao, R. Lu, H. Liang, and A. Vasilakos, “False data injection on state estimation in power systems-attacks, impacts, and defense: A survey,” IEEE Transactions on Industrial Informatics, vol. 13, no. 2, pp. 411–423, 2016.
Y. Wang, M. Amin, J. Fu, and H. Moussa, “A novel data analytical approach for false data injection cyber-physical attack mitigation in smart grids,” IEEE Access, vol. 5, pp. 26022–26033, 2017.
C. Konstantinou and M. Maniatakos, “A data-based detection method against false data injection attacks,” IEEE Design and Test, vol. 37, no. 5, pp. 67–74, 2019.
A. S. Musleh, C. Guo, and Y. D. Zhao, “A survey on the detection algorithms for false data injection attacks in smart grids,” IEEE Transactions on Smart Grid, vol. 11, no. 3, pp. 2218–2234, 2020.
J. Hao, E. Kang, J. Sun, Z. Wang, Z. Meng, X. Li, and Z. Ming, “An adaptive markov strategy for defending smart grid false data injection from malicious attackers,” IEEE Transactions on Smart Grid, vol. 9, no. 4, pp. 2398–2408, 2016.
J. Bae, “Cost-effective placement of phasor measurement units to defend against false data injection attacks on power grid,” Energies, vol. 13, no. 15, pp. 3862–3876, 2020.
W. He, X. Gao, W. Zhong, and F. Qian, “Secure impulsive synchronization control of multi-agent systems under deception attacks,” Information Sciences, vol. 459, pp. 354–368, 2018.
X. Li, Q. Zhou, P. Li, H. Li, and R. Lu, “Event-triggered consensus control for multi-agent systems against false data-injection attacks,” IEEE Transactions on Cybernetics, vol. 50, no. 5, pp. 1856–1866, 2019.
W. He, F. Qian, Q. Han, and G. Chen, “Almost sure stability of nonlinear systems under random and impulsive sequential attacks,” IEEE Transactions on Automatic Control, vol. 65, no. 9, pp. 3879–3886, 2020.
A. Kazemy, J. Lam, and X. M. Zhang, “Event-triggered output feedback synchronization of master-slave neural networks under deception attacks,” IEEE Transactions on Neural Networks and Learning Systems, vol. 33, no. 3, pp. 952–961, 2022.
W. Qi, Y. Hou, G. Zong, and C. K. Ahn, “Finite-time event-triggered control for semi-Markovian switching cyber-physical systems with FDI attacks and applications,” IEEE Transactions on Circuits and Systems I, vol. 68, no. 6, pp. 2665–2674, 2021.
J. Cheng, Y. Wu, Z. Wu, and H. Yan, “Nonstationary filtering for fuzzy Markov switching affine systems with quantization effects and deception attacks,” IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 52, no. 10, pp. 6545–6554, 2022.
W. Qi, C. Lv, G. Zong, and C. K. Ahn, “Sliding mode control for fuzzy networked semi-Markov switching models under cyber attacks. IEEE Transactions on Circuits and Systems II, vol. 69, no. 12, pp. 5034–5038, 2022.
X. Huang and J. Dong, “Reliable leader-to-follower formation control of multiagent systems under communication quantization and attacks,” IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 50, no. 1, pp. 89–99, 2019.
Y. Yang, Y. Qian, and W. Yue, “A secure dynamic event-triggered mechanism for resilient control of multi-Agent systems under sensor and actuator attacks,” IEEE Transactions on Circuits and Systems I, vol. 69, no. 3, pp. 1360–1371, 2021.
A. Mustafa and H. Modares, “Attack analysis and resilient control design for discrete-time distributed multiagent systems,” IEEE Robotics and Automation Letters, vol. 5, no. 2, pp. 369–376, 2019.
J. Cheng, J. Park, Z. Wu, and H. Yan, “Ultimate bound-edness control for networked singularly perturbed systems with deception attacks: A Markovian communication protocol approach,” IEEE Transactions on Network Science and Engineering, vol. 9, no. 2, pp. 445–456, 2022.
L. Cao and B. **ao, “Exponential and resilient control for attitude tracking maneuvering of spacecraft with actuator uncertainties,” IEEE/ASME Transactions on Mechatronics, vol. 24, no. 6, pp. 2531–2540, 2019.
Y. Xu, Z. Wu, Y. Pan, and J. Sun, “Resilient asynchronous state estimation for Markovian jump neural networks subject to stochastic nonlinearities and sensor saturations,” IEEE Transactions on Cybernetics, vol. 52, no. 7, pp. 5809–5818, 2022.
T. Saravanakumar, N. Muoi, and Q. Zhu, “Finite-time sampled-data control of switched stochastic model with non-deterministic actuator faults and saturation nonlinearity,” Journal of the Franklin Institute, vol. 357, no. 18, pp. 13637–13665, 2020.
W. Qi, X. Yang, J. Park, J. Cao, and J. Chen, “Fuzzy SMC for quantized nonlinear stochastic switching systems with semi-Markovian process and application,” IEEE Transactions on Cybernetics, vol. 52, no. 9, pp. 9316–9325, 2022.
T. Saravanakumar, S. M. Anthoni, and Q. Zhu, “Resilient extended dissipative control for Markovian jump systems with partially known transition probabilities under actuator saturation,” Journal of the Franklin Institute, vol. 357, no. 10, pp. 6197–6227, 2020.
R. Sakthivel, A. Parivallal, B. Kaviarasan, H. Lee, and Y. Lim, “Finite-time consensus of Markov jum** multiagent systems with time-varying actuator faults and input saturation,” ISA Transactions, vol. 83, pp. 89–99, 2018.
T. Poongodi, T. Saravanakumar, P. P. Mishra, and Q. Zhu, “Extended dissipative control for Markovian jump time-delayed systems with bounded disturbances,” Mathematical Problems in Engineering, vol. 2020, 5685324, 2020.
H. He, W. Qi, Z. Liu, and M. Wang, “Adaptive attack-resilient control for Markov jump system with additive attacks,” Nonlinear Dynamics, vol. 103, no. 2, pp. 1585–1598, 2021.
Z. Lin, B. Francis, and M. Maggiore, “Necessary and sufficient graphical conditions for formation control of unicycles,” IEEE Transactions on Automatic Control, vol. 50, no. 1, pp. 121–127, 2005.
X. Wu and J. Wang, “Distributed active disturbance rejection control for linear multi-agent systems over directed graph,” Proc. of Chinese Automation Congress (CAC), 18398851, **’an, China, December 2018.
Z. Li, Z. Duan, G. Chen, and L. Huang, “Consensus of multiagent systems and synchronization of complex networks: A unified viewpoint,” IEEE Transactions on Circuits and Systems I, vol. 57, no. 1, pp. 213–224, 2010.
Author information
Authors and Affiliations
Corresponding author
Additional information
Conflict of Interest
The authors declare that there is no conflict of interest with respect to the research, authorship, and/or publication of this paper.
Meirong Wang received her B.S. degree in mathematics and applied mathematics from Fujian Normal University, Fuzhou, China, in 2020. She is currently working toward an M.S. degree with the School of Mathematics, Southeast University, Nan**g, China. Her research interests include false data injection attack and defense methods, and distributed security control of multi-agent systems.
Jianqiang Hu received his B.S. degree in mathematics and applied mathematics from the North China University of Water Resources and Electric Power, Zhengzhou, China, in 2010, and an M.S. degree in applied mathematics from Southeast University, Nan**g, China, in 2013, and his Ph.D. degree in control theory and control engineering, Southeast University, Nan**g, China, in 2016. Currently, he is an associate professor with Jiangsu Provincial Key Laboratory of Networked Collective Intelligence and Department of System Science of School of Mathematics, Southeast University, China. His current research interests include distributed optimization and control of multiagent systems, and demand-side control in smart grids.
**de Cao received his B.S. degree from Anhui Normal University, Wuhu, China, an M.S. degree from Yunnan University, Kunming, China, and a Ph.D. degree from Sichuan University, Chengdu, China, all in mathematics/applied mathematics, in 1986, 1989, and 1998, respectively. He was a Postdoctoral Research Fellow at the Department of Automation and Computer-Aided Engineering, Chinese University of Hong Kong, Hong Kong, from 2001 to 2002. Professor Cao an Endowed Chair Professor, the Dean of the School of Mathematics and the Director of the Research Center for Complex Systems and Network Sciences at Southeast University (SEU). He is also the Director of the National Center for Applied Mathematics at SEU-Jiangsu of China and the Director of the Jiangsu Provincial Key Laboratory of Networked Collective Intelligence of China. Prof. Cao was a recipient of the National Innovation Award of China, Obada Prize and the Highly Cited Researcher Award in Engineering, Computer Science, and Mathematics by Clarivate Analytics. He is elected as a member of Russian Academy of Sciences, a member of the Academy of Europe, a member of Russian Academy of Engineering, a member of the European Academy of Sciences and Arts, a member of the Lithuanian Academy of Sciences, a fellow of African Academy of Sciences, and a fellow of Pakistan Academy of Sciences.
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This work was supported in part by the National Nature Science Foundation of China under Grants 61703095, 61833005, 51807181, 51977032; in part by the Natural Science Foundation of Jiangsu Province of China under Grant BK20170697; in part by the ZhiShan Youth Scholar Program (2242022R40042) from Southeast University.
Rights and permissions
About this article
Cite this article
Wang, M., Hu, J. & Cao, J. Resilient Consensus Control for Linear Multi-agent System Against the False Data Injection Attacks. Int. J. Control Autom. Syst. 21, 2112–2123 (2023). https://doi.org/10.1007/s12555-022-0261-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12555-022-0261-y