Abstract
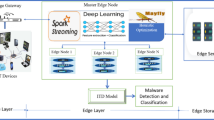
The Internet of Things is a disruptive technology that has changed the face of many industries. On the contrary, the unpresidential growth of IoT has also introduced many cybersecurity challenges. An adversary can exploit a zero-day vulnerability in an IoT to create a botnet of things. An IoT botnet is a group of compromised Internet of Things weaponized to launch cyber attacks. Machine learning and other artificial intelligence techniques are being used to combat the wide range of cyberattacks on the Internet of Things. However, in order to overcome challenges such as early diagnosis, real-time monitoring, and adaptability to different threats, these Machine Learning approaches still require significant feature engineering. In order to identify IoT botnet assaults early on, this paper suggests using a customized convolutional neural network (CCNN) model. The four phases of the model are feature extraction, attack detection, mitigation, and pre-processing. The class imbalance has been improved and the input data pre-processed using the Enhanced Synthetic minority oversampling approach. Furthermore, flow-based features, raw attributes, mean, median, standard deviation, improved entropy, mutual information, and other statistical features are retrieved and regarded as part of the feature set. The CCNN model provides the detection or classification output during the attack detection phase, which operates depending on the features derived from the input data. Additionally, a mitigation process based on entropy has been suggested to locate the attacker node, aiding in the removal of the susceptible attacker IoT node from the network. The compromised IoT node is removed through the entropy-based mitigation method, which establishes the entropy formulation based on the node's activity. The suggested model's specificity is 97.09%, compared to the minimal specificity reached by conventional techniques, including CNN (83.58%), RNN (86.17%), RF (60.46%), SVM (78.50%), and DNN (84.12%) and SMIE (88.42%), respectively.










Similar content being viewed by others
References
Nguyen, H.-T., Ngo, Q.-D., Le, V.-H.: A novel graph-based approach for IoT botnet detection. Int. J. Inf. Secur. (2019). https://doi.org/10.1007/s10207-019-00475-6
Al Shorman, A., Faris, H., Aljarah, I.: Unsupervised intelligent system based on one class support vector machine and Grey Wolf optimization for IoT botnet detection. J. Ambient. Intell. Human. Comput. (2019). https://doi.org/10.1007/s12652-019-01387-y
Lee, S., Abdullah, A., Jhanjhi, N., Kok, S.: Classification of botnet attacks in IoT smart factory using honeypot combined with machine learning. PeerJ Comput. Sci. 7, e350 (2021)
Lee, S., Abdullah, A., Jhanjhi, N.Z.: A review on honeypot-based botnet detection models for smart factory. Int. J. Adv. Comput. Sci. Appl. 11(6), 418–435 (2020)
Zago, M., Gil Pérez, M., Martínez Pérez, G.: Early DGA-based botnet identification: pushing detection to the edges. Clust. Comput. 24(3), 1695–1710 (2021). https://doi.org/10.1007/s10586-020-03213-z
Gelenbe, E., Nakıp, M.: Traffic based sequential learning during botnet attacks to identify compromised IoT devices. IEEE Access 10, 126536–126549 (2022). https://doi.org/10.1109/ACCESS.2022.3226700
Sattari, F., Farooqi, A.H., Qadir, Z., Raza, B., Nazari, H., Almutiry, M.: A hybrid deep learning approach for bottleneck detection in IoT. IEEE Access 10, 77039–77053 (2022). https://doi.org/10.1109/ACCESS.2022.3188635
Hatzivasilis, G., Soultatos, O., Chatziadam, P., Fysarakis, K., Askoxylakis, I., Ioannidis, S., Spanoudakis, G.: WARDOG: awareness detection watchbog for Botnet infection on the host device. IEEE Trans. Sustain. Comput. (2019). https://doi.org/10.1109/tsusc.2019.2914917
Hussain, F., et al.: A two-fold machine learning approach to prevent and detect IoT botnet attacks. IEEE Access 9, 163412–163430 (2021). https://doi.org/10.1109/ACCESS.2021.3131014
Kalakoti, R., Nõmm, S., Bahsi, H.: In-depth feature selection for the statistical machine learning-based botnet detection in IoT networks. IEEE Access 10, 94518–94535 (2022). https://doi.org/10.1109/ACCESS.2022.3204001
Panda, M., Mousa, A.A.A., Hassanien, A.E.: Develo** an efficient feature engineering and machine learning model for detecting IoT-Botnet cyber attacks. IEEE Access 9, 91038–91052 (2021). https://doi.org/10.1109/ACCESS.2021.3092054
Sajjad, S.M., Yousaf, M., Afzal, H., Mufti, M.R.: eMUD: enhanced manufacturer usage description for IoT botnets prevention on home WiFi routers. IEEE Access 8, 164200–164213 (2020). https://doi.org/10.1109/ACCESS.2020.3022272
Yin, L., Luo, X., Zhu, C., Wang, L., Xu, Z., Lu, H.: ConnSpoiler: disrupting C&C communication of IoT-based botnet through fast detection of anomalous domain queries. IEEE Trans. Ind. Inform. 16(2), 1373–1384 (2020). https://doi.org/10.1109/TII.2019.2940742
Popoola, S.I., Adebisi, B., Hammoudeh, M., Gui, G., Gacanin, H.: Hybrid deep learning for botnet attack detection in the Internet-of-Things networks. IEEE Internet Things J. 8(6), 4944–4956 (2021). https://doi.org/10.1109/JIOT.2020.3034156
Beraha, M., Metelliy, A.M., Papiniy, M., Tirinzoniy, A., Restelli, M.: Feature selection via mutual information: new theoretical insights. ar**v:1907.07384v1 [cs.LG] (2019)
Nguyen, H.-T., Ngo, Q.-D., Nguyen, D.-H., Le, V.-H.: PSI-rooted subgraph: a novel feature for IoT botnet detection using classifier algorithms. ICT Express (2020). https://doi.org/10.1016/j.icte.2019.12.001
Motylinski, M., Dermott, Á.M., Iqbal, F., Shah, B.: A GPU-based machine learning approach for detection of botnet attacks. Comput. Secur. 123, 102918 (2022)
Joshi, C., Ranjan, R.K., Bharti, V.: A fuzzy logic based feature engineering approach for Botnet detection using ANN. J. King Saud Univ. Comput. Inf. Sci. (2021). https://doi.org/10.1016/j.jksuci.2021.06.018
Asadi, M., Jamali, M.A.J., Parsa, S., Majidnezhad, V.: Detecting botnet by using particle swarm optimization algorithm based on voting system. Future Gener. Comput. Syst. (2020). https://doi.org/10.1016/j.future.2020.01.055
Shareena, J., Ramdas, A., AP, H.: Intrusion detection system for IOT botnet attacks using deep learning. SN Comput. Sci. (2021). https://doi.org/10.1007/s42979-021-00516-9
Rezaei, A.: Using ensemble learning technique for detecting botnet on IoT. SN Comput. Sci. (2021). https://doi.org/10.1007/s42979-021-00585-w
Ahmed, A.A., Jabbar, W.A., Sadiq, A.S., Patel, H.: Deep learning-based classification model for botnet attack detection. J. Ambient. Intell. Human. Comput. (2020). https://doi.org/10.1007/s12652-020-01848-9
Asadi, M.: Detecting IoT botnets based on the combination of cooperative game theory with deep and machine learning approaches. J. Ambient. Intell. Human. Comput. (2021). https://doi.org/10.1007/s12652-021-03185-x
Alzahrani, M.Y., Bamhdi, A.M.: Hybrid deep-learning model to detect botnet attacks over internet of things environments. Soft. Comput. 26(16), 7721–7735 (2022)
Hezam, A.A., Mostafa, S.A., Baharum, Z., Alanda, A., Salikon, M.Z.: Combining deep learning models for enhancing the detection of botnet attacks in multiple sensors internet of things networks. Int. J. Inform. Visual. 5(4), 380–387 (2021)
Mukherjee, M., Khushi, M.: SMOTE-ENC: a novel SMOTE-based method to generate synthetic data for nominal and continuous features. Appl. Syst. Innov. 4, 18 (2021). https://doi.org/10.3390/asi4010018
Yong Deng, Y.: Deng entropy. Chaos Solitons Fractals 91, 549–553 (2016). https://doi.org/10.1016/j.chaos.2016.07.014
Sowmya, S., Jose, D.: Contemplate on ECG signals and classification of arrhythmia signals using CNN-LSTM deep learning model. Meas. Sens. 24, 100558 (2022)
https://www.impactcybertrust.org/dataset_view?idDataset=1296
Sriram, S., Vinayakumar, R., Alazab, M., Soman, K.P.: Network flow based IoT botnet attack detection using deep learning. In: IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS) (2020)
Alissa, K., Alyas, T., Zafar, K., Abbas, Q., Tabassum, N., Sakib, S.: Botnet attack detection in IoT using machine learning. Comput. Intell. Neurosci. 2022(1), 4515642 (2022)
Funding
This research did not receive any specific funding.
Author information
Authors and Affiliations
Contributions
BB conceived the presented idea and designed the analysis. Also, he carried out the experiment and wrote the manuscript with support from ST. All authors discussed the results and contributed to the final manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Ethical approval
Not applicable.
Informed consent
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Bojarajulu, B., Tanwar, S. Customized convolutional neural network model for IoT botnet attack detection. SIViP (2024). https://doi.org/10.1007/s11760-024-03248-4
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11760-024-03248-4