Abstract
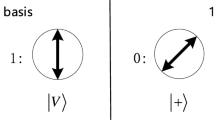
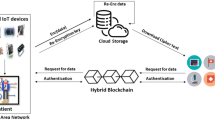
Due to the exponential growth of cloud data and network services, computational resources and cloud data security have one of the most attractive research issues in the real-time cloud environment. Numerous types of cloud services are combined into various domain applications, including, e-health, defence, clinical databases, and so on, for data storage and resource computing. However, a traditional challenge to consider is that the Data Owner (DO) no longer has the ability to modify the access control policy or key policy, resulting in data sharing inflexibility, inefficiency, and key abusers. To address these concerns, we propose an enhanced d level cut-off point-Quantum Secret Sharing (EdLCp-QSS) scheme based on an efficient Monitoring Key Ciphertext-ABE (MKCABE) –access control with Blockchain and Key Controller (EQMBK) mechanism for security. The proposed EQMBK mechanism provides security for monitoring the data from getting accessed by un-authorized users as well as offers updating security when a new user joins the cloud environment. The proposed EQMBK system ensures that data is not accessible by unauthorised users and that security is updated when a new user joins the cloud environment. Finally, experimental simulation reveals that the suggested technique is very efficient in preserving the privacy of the user’s data against unauthorised parties in terms of computation time encryption time, system initialization time, key generation time, and decryption time. Furthermore, when compared to state-of-the-art techniques, the proposed methods are more resilient and provide greater performance.






Similar content being viewed by others
Data Availability
Authors not interested to disclose the availability of data.
References
Kandukuri, B. R., & Rakshit, A. (2009). Cloud security issues. In 2009 IEEE international conference on services computing (pp. 517–520). IEEE.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security problem. ar**v preprint ar**v:1609.01107.
Fatima, S., & Ahmad, S. (2019). An exhaustive review on security issues in cloud computing. KSII Transactions on Internet and Information Systems (TIIS), 13(6), 3219–3237.
An, Y. Z., Zaaba, Z. F., & Samsudin, N. F. (2016). Reviews on security issues and challenges in cloud computing. In: IOP Conference Series: Materials Science and Engineering, (Vol. 160, No. 1, p. 012106). Bristol; IOP Publishing.
Zhang, L., Cui, Y., & Mu, Y. (2019). Improving security and privacy attribute based data sharing in cloud computing. IEEE Systems Journal, 14(1), 387–397.
Pachala, S., Rupa, C., & Sumalatha, L. (2021). An improved security and privacy management system for data in multi-cloud environments using a hybrid approach. Evolutionary Intelligence, 14(2), 1117–1133.
Yang, W., Huang, L., Shi, R., & He, L. (2013). Secret sharing based on quantum fourier transform. Quantum information processing, 12(7), 2465–2474.
Qin, H., Zhu, X., & Dai, Y. (2015). (t, n) Threshold quantum secret sharing using the phase shift operation. Quantum Information Processing, 14(8), 2997–3004.
Song, X. L., Liu, Y. B., Deng, H. Y., & **ao, Y. G. (2017). (t, n) threshold d-level quantum secret sharing. Scientific reports, 7(1), 1–9.
Mashhadi, S. (2020). Improvement of a (t, n) Threshold d− level quantum secret sharing scheme. Journal of Applied Security Research, 1–12.
Kumar, P., & Alphonse, P. J. A. (2018). Attribute based encryption in cloud computing: A survey, gap analysis, and future directions. Journal of Network and Computer Applications, 108, 37–52.
Namasudra, S., Devi, D., Kadry, S., Sundarasekar, R., & Shanthini, A. (2020). Towards DNA based data security in the cloud computing environment. Computer Communications, 151, 539–547.
Kamara, S., & Lauter, K. (2010). Cryptographic cloud storage. In International Conference on Financial Cryptography and Data Security, pp. 136–149. Berlin: Springer
Sun, P. (2020). Security and privacy protection in cloud computing: Discussions and challenges. Journal of Network and Computer Applications, 160, 102642.
Chenthara, S., Ahmed, K., Wang, H., & Whittaker, F. (2019). Security and privacy-preserving challenges of e-health solutions in cloud computing. IEEE access, 7, 74361–74382.
Sharma, Y., Gupta, H., & Khatri, S. K. (2019, February). A security model for the enhancement of data privacy in cloud computing. In 2019 Amity International Conference on Artificial Intelligence (AICAI) (pp. 898–902). IEEE.
Sajay, K. R., Babu, S. S., & Vijayalakshmi, Y. (2019). Enhancing the security of cloud data using hybrid encryption algorithm. Journal of Ambient Intelligence and Humanized Computing, 1–10.
Liu, P. (2020). Public-key encryption secure against related randomness attacks for improved end-to-end security of cloud/edge computing. IEEE Access, 8, 16750–16759.
Tahir, M., Sardaraz, M., Mehmood, Z., & Muhammad, S. (2021). CryptoGA: A cryptosystem based on genetic algorithm for cloud data security. Cluster Computing, 24(2), 739–752.
Zhang, L., Hu, G., Mu, Y., & Rezaeibagha, F. (2019). Hidden ciphertext policy attribute-based encryption with fast decryption for personal health record system. IEEE Access, 7, 33202–33213.
Liu, Z., Xu, J., Liu, Y., & Wang, B. (2019). Updatable ciphertext-policy attribute-based encryption scheme with traceability and revocability. IEEE Access, 7, 66832–66844.
Li, J., Wang, S., Li, Y., Wang, H., Wang, H., Wang, H., & You, Z. (2019). An efficient attribute-based encryption scheme with policy update and file update in cloud computing. IEEE Transactions on Industrial Informatics, 15(12), 6500–6509.
Zhang, Y., Li, J., & Yan, H. (2019). Constant size ciphertext distributed CP-ABE scheme with privacy protection and fully hiding access structure. IEEE Access, 7, 47982–47990.
Guo, L., Yang, X., & Yau, W. C. (2021). TABE-DAC: Efficient traceable attribute-based encryption scheme with dynamic access control based on blockchain. IEEE Access, 9, 8479–8490.
Morales-Sandoval, M., Cabello, M. H., Marin-Castro, H. M., & Compean, J. L. G. (2020). Attribute-based encryption approach for storage, sharing and retrieval of encrypted data in the cloud. IEEE Access, 8, 170101–170116.
Guo, R., Li, X., Zheng, D., & Zhang, Y. (2020). An attribute-based encryption scheme with multiple authorities on hierarchical personal health record in cloud. The Journal of Supercomputing, 76(7), 4884–4903.
Liu, S., Yu, J., **ao, Y., Wan, Z., Wang, S., & Yan, B. (2020). Bc-sabe: Blockchain-aided searchable attribute-based encryption for cloud-iot. IEEE Internet of Things Journal, 7(9), 7851–7867.
Eltayieb, N., Elhabob, R., Hassan, A., & Li, F. (2020). A blockchain-based attribute-based signcryption scheme to secure data sharing in the cloud. Journal of Systems Architecture, 102, 101653.
Beimel, A. (1996). Secure schemes for secret sharing and key distribution.
Funding
There is no funding for this study.
Author information
Authors and Affiliations
Contributions
All the authors have participated in writing the manuscript and have revised the final version. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
Authors declares that they have no conflict of interest.
Ethical Approval
This article does not contain any studies with human participants and/or animals performed by any of the authors.
Informed Consent
There is no informed consent for this study.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Srivastava, A.K., Pandey, D. & Agarwal, A. An Enhanced D Level Cut-Off Point-Quantum Secret Sharing Access Structure Scheme Based Efficient Monitoring Key Ciphertext Attributes with Encryption Access Control with Blockchain and Key Mechanism for Security in Cloud Computing. Wireless Pers Commun 135, 367–387 (2024). https://doi.org/10.1007/s11277-024-11021-6
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-024-11021-6