Abstract
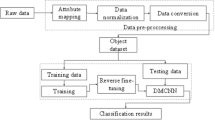
Active and passive intrusion are the two types of intrusion. The active intrusion attempts to modify the data and the passive intrusion observes the data and replica. This intrusion creates big damage and congestion in the network. Deep learning techniques have been extensively used to advance intrusion detection systems, which can rapidly and effectively identify and classify intrusions at various levels of networks. These technologies are capable of properly and swiftly identifying threats. Networks, however, require a sophisticated security solution due to the frequent emergence and evolution of hostile threats. Publicly accessible intrusion databases must be updated often due to the intricacy of attacks and constantly varying detection. To solve these issues, Deep Convolutional Neural Network for Active intrusion detection and Protect data from Passive Intrusion by Pascal triangle is introduced. This work proposes a convolutional neural network (CNN) based network intrusion detection model with five convolutional layers. Furthermore, this approach uses the Pascal Triangle method, making the dummy route for protecting the data from passive intrusion. This model is evaluated for binary and multiclass classification using the CICIDS2018 dataset, a publicly available dataset comprising 80 statistical features. The dataset is preprocessed by data transformation and numerical standardization techniques. To evaluate the performance of the suggested system, experiments are carried out. The research findings show that the proposed CNN performs better at detecting multiclass categorization than existing intrusion detection methods, with average accuracy, precision, recall, and F1-score values of 99.16, 99.20, 99.63, and 98.76%, respectively.






Similar content being viewed by others
Data Availability
The data that support the findings of this study are available on request from the corresponding author.
Code Availability
Not applicable.
References
Ahmad, Z., Shahid Khan, A., Nisar, K., Haider, I., Hassan, R., Haque, M. R., Tarmizi, S., & Rodrigues, J. J. P. C. (2021). Anomaly detection using deep neural network for IoT architecture. Applied Sciences, 11, 7050.
Acronis Cyberthreats Report 2022: 20 Billion USD in Damage from Ransomware and other Cyber Attacks. Available online: https://www.acronis.com/en-eu/pr/2021/12/09-13-43.html (accessed on 10 May 2023).
Sun, N., Zhang, J., Rimba, P., Gao, S., Zhang, L. Y., & **ang, Y. (2018). Data-driven cybersecurity incident prediction: A survey. IEEE Commun. Surv. Tutor., 21, 1744–1772.
Kim, T., & Pak, W. (2023). Deep learning-based network intrusion detection using multiple image transformers. Applied Sciences, 13, 2754. https://doi.org/10.3390/app13052754
Ferrag, M. A., Maglaras, L., Moschoyiannis, S., & Janicke, H. (2020). deep learning for cyber security intrusion detection: Approaches datasets and comparative study. Journal of Information Security and Application, 50, 102419.
Moustafa, N., Slay, J. (2015). UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set), In: Proc. Military Commun. Inf. Syst. Conf., pp. 1–6
Sharafaldin, I., Habibi Lashkari, A., Ghorbani, A. A. (2018). Toward generating a newintrusion detection dataset and intrusion trafc characterization. In: Proc. 4th Int. Conf. Inf. Syst. Secur. Privacy, pp. 108–116
Wu, Y., Wei, D., & Feng, J. (2020). Network attacks detection methods based on deep learning techniques: A survey. Security and Communication Networks. https://doi.org/10.1155/2020/8872923
Khraisat, et al. (2019). Survey of intrusion detection systems: techniques, datasets and challenges. Cybersecurity, 2(20), 1–22.
Lin, P., Ye, K., Xu, C.Z. (2019). Dynamic Network Anomaly Detection System by Using Deep Learning Techniques. In: Proceedings of the Cloud Computing–CLOUD 2019: 12th International Conference, Held as Part of the Services Conference Federation,SCFF 2019, San Diego, CA,USAA, 25–30; pp. 161–176
Karatas, G., Demir, O., & Sahingoz, O. K. (2020). Increasing the performance of machine learning-based IDSs on an imbalanced and up-to-date dataset. IEEE Access, 8, 32150–32162.
**ao, Y., **ng, C., Zhang, T., & Ahao, Z. (2019). An intrusion detection model based on feature reduction and convolutional neural networks. IEEE Access, 7, 42210–42219.
Girdler, T., & Vassilakis, V. G. (2021). Implementing an intrusion detection and prevention system using software-defined networking: Defending againstARPP spoofing attacks and BlacklistedMACC addresses. Computers & Electrical Engineering, 90, 106990.
Zhang, Y., Chen, X., **, L., Wang, X., & Guo, D. (2019). Network intrusion detection: based on deep hierarchical network and original flow data. IEEE Access, 7, 37004–37016.
Imran, R., Jamil, F., & Kim, D. (2021). An ensemble of prediction and learning mechanism for improving accuracy of anomaly detection in network intrusion environments. Sustainability, 13, 10057.
Kim, J., Kim, H., Shim, M., & Choi, E. (2020). CNN-based network intrusion detection against denial-of-service attacks. Electronics, 9, 916.
He, H., Sun, X., He, H., Zhao, G., He, L., & Ren, J. (2019). A novel multimodal-sequential approach based on multi-view features for network intrusion detection. IEEE Access, 7, 183207–183221.
Mezina, A., Burget, R., & Travieso-González, C. M. (2021). Network anomaly detection with temporal convolutional network and U-net model. IEEE Access, 9, 143608–143622.
Tang, Y., Gu, L., & Wang, L. (2022). Deep stacking network for intrusion detection. Sensors, 22, 25.
Balakrishnan, N., Rajendran, A., Pelusi, D., & Ponnusamy, V. (2021). Deep Belief Network enhanced intrusion detection system to prevent security breach in the Internet of Things. Internet of things, 14, 100112.
Diro, A. A., & Chilamkurti, N. (2017). Distributed attack detection scheme using deep learning approach for internet of things. Future Generation Computer Systems. https://doi.org/10.1016/j.future.2017.08.043
Vijayakumar, K. P., Pradeep, K., Balasundaram, A., & Prusty, M. R. (2023). Enhanced cyber attack detection process for internet of health things (IoHT) devices using deep neural network. Processes, 11, 1072. https://doi.org/10.3390/pr11041072
Vinayakumar, R., Alazab, M., Soman, K. P., Poornachandran, P., Al-Nemrat, A., & Venkatraman, S. (2019). Deep learning approach for intelligent intrusion detection system. IEEE Access, 7, 41525–41550. https://doi.org/10.1109/ACCESS.2019.2895334.[21]
Manimurugan, S., Al-Mutairi, S., Aborokbah, M. M., Chilamkurti, N., Ganesan, S., & Patan, R. (2020). Effective attack detection in internet of medical things smart environment using a deep belief neural network. IEEE Access, 8, 77396–77404. https://doi.org/10.1109/ACCESS.2020.2986013
Qazi, E. U. H., Faheem, M. H., & Zia, T. (2023). HDLNIDSS: hybrid deep-learning-based network intrusion detection system. Applied Science, 13, 4921. https://doi.org/10.3390/app13084921
Lakshmana Kumar, R., Jayanthi, S., BalaAnand, M., Sivaparthipan, C.B. (2023). An automatic anomaly application detection system in mobile devices using FL-HTR-DBN and SKLD-SED K means algorithms, Journal of Intelligent & Fuzzy Systems, Pre-press, pp. 1–14
Bala Anand, M., Sivaparthipan, C. B. (2013). Security Privilege by generating Random Selective Index in Session Based Password Validation, Journal of Science and Innovative Engineering & Technology
Santhoshkumar, M. S., Sivaparthipan, M. C., Prabakar, D. D., & Karthik, D. S. (2013). Secure encryption technique with keying based virtual energy for wireless sensor networks. International Journal of Advance Research in Computer Science and Management Studies, 1(5), 139–144.
Acknowledgements
The authors extend their appreciation to the Deanship of Scientific Research at University of Bisha for funding this research through the general research project under grant number (UB-GRP- 65 -1444).
Author information
Authors and Affiliations
Contributions
All Author is contributed to the design and methodology of this study, the assessment of the outcomes and the writing of the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Alqahtani, A.S. Deep Convolutional Neural Network for Active Intrusion Detection and Protect data from Passive Intrusion by Pascal Triangle. Wireless Pers Commun (2024). https://doi.org/10.1007/s11277-023-10846-x
Accepted:
Published:
DOI: https://doi.org/10.1007/s11277-023-10846-x