Abstract
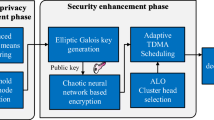
Design of effective algorithm for reliable and energy optimized secure routing protocol (SRP) for wireless sensor networks (WSNs) is a demanding design issue now. To handle this problem, we propose a trust and encryption-based SRP based on trust modelling with intrusion detection, elliptic curve cryptography (ECC), clustering, fuzzy rules and ant colony optimization (ACO)-oriented SRP for WSN routing. In this paper, an extended convolutional neural networks with Schrodinger equation and particle swarm optimization is proposed for develo** and intrusion detection-based trust modelling. Moreover, a new node authentication scheme and an encryption-based secure routing protocol are also proposed in this work for increasing the security. This proposed secure protocol known as trust and ECC encryption-based ACO-SRP (TECC-ACO-SRP) performs authentication and trust analysis on the nodes using intrusion detection, and then, the data are communicated after data encryption using ECC encryption technique. This proposed system combines dominant set clustering with fuzzy rules to make clusters with similar type of nodes as members and then selects cluster heads (CHs) for every cluster. This SRP ensures improved security, reduced delay and energy usage with higher packet delivery ratio than other existing SRPs.










Similar content being viewed by others
References
Elhoseny M, Elminir H, Riad A, Yuan X (2016) A secure data routing schema for WSN using elliptic curve cryptography and homomorphic encryption. J King Saud Univ-Comput Inf Sci 28(3):262–275. https://doi.org/10.1016/j.jksuci.2015.11.001
Mehta K, Pal R (2017) Biogeography based optimization protocol for energy efficient evolutionary algorithm:(BBO: EEEA), In 2017 International Conference on Computing and Communication Technologies for Smart Nation (IC3TSN), IEEE, pp.281–286. https://doi.org/10.1109/IC3TSN.2017.8284492
Al Marshoud MS, Al-Bayatti AH, Kiraz MS (2024) Security, privacy, and decentralized trust management in VANETs: a review of current research and future directions. ACM Comput Surv. https://doi.org/10.1145/3656166
Alqahtani M, Gumaei A, Mathkour H, Maher Ben Ismail M (2019) A genetic-based extreme gradient boosting model for detecting intrusions in wireless sensor networks. Sensors 19(20):1–20. https://doi.org/10.3390/s19204383
Zhang X, Deng H, **ong Z, Liu Y, Rao Y, Lyu Y, Li Y, Hou D, Li Y (2024) Secure routing strategy based on attribute-based trust access control in social-aware networks. J Signal Process Syst. https://doi.org/10.1007/s11265-023-01908-1
Kaur S, Singh M (2020) Hybrid intrusion detection and signature generation using deep recurrent neural networks. Neural Comput Appl 32(12):7859–7877. https://doi.org/10.1007/s00521-019-04187-9
Gautam AK, Kumar R (2021) A comprehensive study on key management, authentication and trust management techniques in wireless sensor networks. SN Appl Sci 3(1):1–27. https://doi.org/10.1007/s42452-020-04089-9
Vinayakumar R, Alazab M, Soman KP, Poornachandran P, Al-Nemrat A, Venkatraman S (2019) Deep learning approach for intelligent intrusion detection system. IEEE Access 7:41525–41550
Goodfellow I, Bengio Y, Courville A (2016) Deep learning. MIT Press
Soni S, Chouhan SS, Rathore SS (2023) TextConvoNet: a convolutional neural network based architecture for text classification. Appl Intell 53:14249–14268. https://doi.org/10.1007/s10489-022-04221-9
Schrödinger E (1926) An undulatory theory of the mechanics of atoms and molecules. Phys Rev 28(6):1049–1070. https://doi.org/10.1103/PhysRev.28.1049
Shalini S, Selvi M (2023) Intelligent IDS in wireless sensor networks using deep fuzzy convolutional neural network. Neural Comput Appl 35:15201–15220. https://doi.org/10.1007/s00521-023-08511-2
Karam R (2020) Schrödinger”s original struggles with a complex wave function. Am J Phys 88(6):433–438. https://doi.org/10.1119/10.0000852
Kennedy J, Eberhart R (1995) Particle swarm optimization. Proceedings of IEEE International Conference on Neural Networks. Vol. IV. pp. 1942–1948. https://ieeexplore.ieee.org/abstract/document/488968
Maheshwari P, Sharma AK, Verma K (2021) Energy efficient cluster-based routing protocol for WSN using butterfly optimization algorithm and ant colony optimization. Ad Hoc Netw 110:1–15. https://doi.org/10.1016/j.adhoc.2020.102317
Dinesh K, Santhosh Kumar SVN (2024) Energy-efficient trust-aware secured neuro-fuzzy clustering with sparrow search optimization in wireless sensor network. Int J Inf Secur 23(1):199–223. https://doi.org/10.1007/s10207-023-00737-4
Yesodha K, Krishnamurthy M, Selvi M, Kannan A (2024) Intrusion detection system extended CNN and artificial bee colony optimization in wireless sensor networks. Peer-to-Peer Netw Appl. https://doi.org/10.1007/s12083-024-01650-w
Verma V, Jha VK (2024) Secure and energy-aware data transmission for IoT-WSNs with the help of cluster-based secure optimal routing. Wirel Pers Commun. https://doi.org/10.1007/s11277-024-10983-x
Batra PK, Kant K (2016) LEACH-MAC: a new cluster head selection algorithm for wireless sensor networks. Wireless Netw 22(1):49–60. https://doi.org/10.1007/s11276-015-0951-y
Hande JY, Sadiwala R (2024) Data security-based routing in MANETs using key management mechanism. SN Comput Sci 5(1):155. https://doi.org/10.1007/s42979-023-02409-5
Colorni.A, Dogrio.M, Maneizzo.V, (1991) Distributed Optimization by Ant Colonies, Proceedings of the First European Conference on Artificial Life, Elsevier Publishing, pp. 134–142.https://www-public.imtbs-tsp.eu/~gibson/Teaching/Teaching-ReadingMaterial/ColorniDorigoManiezzo91.pdf
Russell S, Peter Norvig P (1994) Artificial intelligence: a modern approach. Prentice Hall, New Jersey
Rich E, Knight K, Nair SB (2009) Artificial intelligence, 3rd edn. McGraw Hill, New York
Shalini S, Selvi M (2023) Multi-objective PSO based feature selection for intrusion detection in IoT based wireless sensor networks. Optik 273:1–15. https://doi.org/10.1016/j.ijleo.2022.170419
Dorgio M, Maniezzo V, Colorni A (1996) The ant system: optimization by a colony of cooperating agents. IEEE Trans Syst, Man Cybern—Part B 26(1):29–41
Sim KM, Sun WH (2003) Ant colony optimization for routing and load-balancing: survey and new directions. IEEE Trans Syst Man Cybern—Part A: Syst Humans 33(5):560–572
Stallings W (2017) Cryptography and network security: principles and practices, 7th edn. Pearson Education, London
Tropea M, Spina MG, De Rango F, Gentile AF (2022) Security in wireless sensor networks: a cryptography performance analysis at MAC layer. Future Internet 14(5):1–20. https://doi.org/10.3390/fi14050145
Wang Y, Li Z (2021) Inverse problem of nonlinear Schrodinger equation as learning of convolutional neural network, ar**v preprint ar**v:2107.08593, pp 1–25. https://arxiv.org/abs/2107.08593
Szegedy C, Ioffe S, Vanhoucke V, Alemi A (2016) Inception-v4, inception-ResNet and the impact of residual connections on learning. ar**v:1602.07261. https://ojs.aaai.org/index.php/aaai/article/view/11231
Sharma B, Sharma L, Lal C, Roy S (2024) Explainable artificial intelligence for intrusion detection in IoT networks: a deep learning-based approach. Expert Syst Appl 238:121751. https://doi.org/10.1016/j.eswa.2023.121751
Yasotha B, Sasikala T, Krishnamurthy M (2023) Wrapper based linear discriminant analysis (LDA) for intrusion detection in IIoT. Comput Syst Sci Eng 45(2):1625–1640
Nagendra Babu G, Mehata KM, Krishnamurthy M (2019) A multi-level lightweight method to find malfunctioning nodes in WSN. J Adv Res Dyn Control Syst 11(01):818–823
Misbha DS (2023) Lightweight key distribution for secured and energy efficient communication in wireless sensor network: an optimization assisted model. High-Confid Comput 3(2):100126
Lopez J, Dahab R (2000) An overview of elliptic curve cryptography, Technical report, Technical report IC-00-10, Institute of Computing – UNICAMP
Nancy P, Muthurajkumar S, Ganapathy S, Santhosh Kumar SVN, Selvi M, Arputharaj K (2020) Intrusion detection using dynamic feature selection and fuzzy temporal decision tree classification for wireless sensor networks. IET Commun 14(5):888–895. https://doi.org/10.1049/iet-com.2019.0172
Duan Y, Chen N, Chang L, Ni Y, Santhosh Kumar SVN, Zhang P (2022) CAPSO: chaos adaptive particle swarm optimization algorithm. IEEE Access 10:29393–29405
Sun Q, Huang X, Kibalya G, Kumar N, Kumar SS, Zhang P, **e D (2021) Security enhanced sentence similarity computing model based on convolutional neural network. IEEE access 9:104183–104196
Patil AR, Borkar GM (2023) Node authentication and encrypted data transmission in mobile ad hoc network using the swarm intelligence-based secure ad-hoc on-demand distance vector algorithm. IET Wirel Sens Syst 13(6):201–215. https://doi.org/10.1049/wss2.12068
Luo Y (2021) Research on network security intrusion detection system based on machine learning. Int J Netw Secur 23(3):490–495. https://doi.org/10.6633/IJNS.202105
Mahmoud MM, Lin X, Shen X (2013) Secure and reliable routing protocols for heterogeneous multihop wireless networks. IEEE Trans Parallel Distrib Syst 26(4):1140–1153. https://doi.org/10.1109/TPDS.2013.138
Thakkar A, Lohiya R (2020) Role of swarm and evolutionary algorithms for intrusion detection system: a survey. Swarm Evol Comput 53:1–34. https://doi.org/10.1016/j.swevo.2019.100631
Mezrag F, Bitam S, Mellouk A (2022) An efficient and lightweight identity-based scheme for secure communication in clustered wireless sensor networks. J Netw Comput Appl 200:1–13. https://doi.org/10.1016/j.jnca.2021.103282
Fotohi R, Firoozi Bari S, Yusefi M (2020) Securing wireless sensor networks against denial-of-sleep attacks using ECC cryptography algorithm and interlock protocol. Int J Commun Syst 33(4):1–30. https://doi.org/10.1002/dac.4234
Ren J, Guo J, Qian W, Yuan H, Hao X, **g**g H (2019) Building an effective intrusion detection system by using hybrid data optimization based on machine learning algorithms. Secur Commun Netw. https://doi.org/10.1155/2019/7130868
Raman MG, Somu N, Kirthivasan K, Liscano R, Sriram VS (2017) An efficient intrusion detection system based on hypergraph-Genetic algorithm for parameter optimization and feature selection in support vector machine. Knowl-Based Syst 134:1–12. https://doi.org/10.1016/j.knosys.2017.07.005
Chan L, Gomez Chavez K, RudolphH HA (2020) Hierarchical routing protocols for wireless sensor network: a compressive survey. Wireless Netw 26(5):3291–3314. https://doi.org/10.1007/s11276-020-02260-z
Wang F, Wang Q, Nie F, Li Z, Yu W, Ren F (2020) A linear multivariate binary decision tree classifier based on K-means splitting. Pattern Recogn 107:1–13. https://doi.org/10.1016/j.patcog.2020.107521
Khoshkangini R, Zaboli S, Conti M, (2014) Efficient routing protocol via ant colony optimization (ACO) and breadth first search (BFS),In Proceedings of the IEEE international Conference on Cyber, Physical and Social Computing, September, pp.374–380. https://doi.org/10.1109/iThings.2014.69
Vaiyapuri T, Parvathy VS, Manikandan V, Krishnaraj N, Gupta D, Shankar K (2021) A novel hybrid optimization for cluster-based routing protocol in information-centric wireless sensor networks for IoT based mobile edge computing. Wirel Pers Commun. https://doi.org/10.1007/s11277-021-08088-w
Selvi M, Thangaramya K, Ganapathy S, Kulothungan K, Khannah Nehemiah H, Kannan A (2019) An energy aware trust based secure routing algorithm for effective communication in wireless sensor networks. Wireless Pers Commun 105(4):1475–1490. https://doi.org/10.1007/s11277-019-06155-x
Asaad MS, Croock MS (2021) Adaptive security approach for wireless sensor network using ECC algorithm. Indones J Electr Eng Comput Sci 22(1):361–368. https://doi.org/10.11591/ijeecs.v22.i1
Chang L, Li F, Niu X, Zhu J (2022) On an improved clustering algorithm based on node density for WSN routing protocol. Cluster Comput. https://doi.org/10.1007/s10586-022-03544-z
Hasan NA, Farhan AK (2019) Security improve in ZigBee protocol based on ECC public algorithm in WSN. Eng Technol J 37(3):67–73. https://doi.org/10.30684/etj.37.3B.1
Moraboena S, Ketepalli G, Ragam P (2020) A deep learning approach to network intrusion detection using deep autoencoder. Revis Intell Artif 34(4):457–463. https://doi.org/10.18280/ria.340410
Salman T, Bhamare D, Erbad A, Jain R, Samaka M, (2017) June. Machine learning for anomaly detection and categorization in multi-cloud environments, In 2017 IEEE 4th International Conference on Cyber Security and Cloud Computing (CSCloud) pp. 97–103. IEEE. https://doi.org/10.1109/CSCloud.2017.15
Selvi M, Santhosh Kumar SVN, Ganapathy S, Ayyanar A, Khanna Nehemiah H, Kannan A (2021) An energy efficient clustered gravitational and fuzzy based routing algorithm in WSNs. Wireless Pers Commun 116(1):61–90. https://doi.org/10.1007/s11277-020-07705-4
Shalini S, Selvi M, Santhosh Kumar SVN, Kannan A (2021) Energy efficient clustering routing protocol and ACO algorithm in WSN, In International Conference on Advances in Computing and Data Sciences, Springer, pp.68–80. https://doi.org/10.1007/978-3-030-81462-5_7
Rakesh R, Santhosh Kumar SVN, Yogesh P, Kannan A (2019) Detection of DoS attacks in cloud networks using intelligent rule-based classification system. Cluster Comput 22(Suppl 1):423–434. https://doi.org/10.1007/s10586-018-2181-4
Selvi M, Nandhini C, Thangaramya K, Kulothungan K, Kannan A (2017) HBO based clustering and energy optimized routing algorithm for WSN, Eighth International Conference on Advanced Computing (ICoAC), Chennai, pp. 89–92. https://ieeexplore.ieee.org/abstract/document/7951751
Munuswamy S, Saravanakumar MJ, Sannasi G, Harichandran KN, Arputharaj K (2018) Virtual force-based intelligent clustering for energy-efficient routing in mobile wireless sensor networks. Turk J Electr Eng Comput Sci 26(3):1444–1452
Selvi M, Logambigai R, Ganapathy S, Sai Ramesh L, Khanna Nehemiah H, Kannan A, (2016) fuzzy temporal approach for energy efficient routing in WSN, Proceedings of International Conference on Informatics and Analytics, ACM, pp. 117:1–117:5. https://doi.org/10.1145/2980258.2982109
Logambigai R, Kannan A (2018) Energy conservation routing algorithm for wireless sensor networks using hybrid optimisation approach. Int J Commun Netw Distr Syst 20(3):352–371. https://doi.org/10.1504/IJCNDS.2018.091059
Biswas K, Muthukkumarasamy V, Chowdhury MJM, Wu XW, Singh K (2023) A multipath routing protocol for secure energy efficient communication in wireless sensor networks. Comput Netw 232:109842. https://doi.org/10.1016/j.comnet.2023.109842
Thangaramya K, Logambigai R, Kulothungan K, Ganapathy S, Kannan A (2020) QoS aware trust based routing algorithm for wireless sensor networks. Wirel Pers Commun 110(4):1637–1658. https://doi.org/10.1007/s11277-019-06788-y
Pedditi RB, Debasis K (2023) Energy efficient routing protocol for an IoT-based WSN system to detect forest fires. Appl Sci 13(5):3026. https://doi.org/10.3390/app13053026
Mohajerani A, Gharavian D (2016) An ant colony optimization-based routing algorithm for extending network lifetime in wireless sensor networks. Wirel Netw 22(8):2637–2647. https://doi.org/10.1007/s11276-015-1061-6
Rathee M, Kumar S, Gandomi AH, Dilip K, Balusamy B, Patan R (2019) Ant colony optimization-based quality of service aware energy balancing secure routing algorithm for wireless sensor networks. IEEE Trans Eng Manag 68(1):170–182
Sahoo BM, Pandey HM, Amgoth T (2021) GAPSO-H: a hybrid approach towards optimizing the cluster-based routing in wireless sensor network. Swarm Evol Comput 60:1–42. https://doi.org/10.1016/j.swevo.2020.100772
Zheng A, Zhang Z, Liu W, Liu J, **ao Y, Li C (2023) Dual cluster head optimization of wireless sensor networks based on multi-objective particle swarm optimization. Sensors 23(1):1–19. https://doi.org/10.3390/s23010231
Younis O, Fahmy S (2004) HEED: a hybrid, energy-efficient, distributed clustering approach for ad hoc sensor networks. IEEE Trans Mobile Comput 3(4):366–379
Wei D, ** Y, Vural S, Moessner K, Tafazolli R (2011) An energy-efficient clustering solution for wireless sensor networks. IEEE Trans Wirel Commun 10(11):3973–3983
Wu W, **ong N, Wu C (2017) Improved clustering algorithm based on energy consumption in wireless sensor networks. IET Networks 6(3):47–53. https://doi.org/10.1049/iet-net.2016.0115
Thangaramya K, Kulothungan K, Logambigai R, Selvi M, Ganapathy S, Kannan A (2019) Energy aware cluster and neuro-fuzzy based routing algorithm for wireless sensor networks in IoT. Comput Netw 151:211–223. https://doi.org/10.1016/j.comnet.2019.01.024
Santhosh Kumar SVN, Selvi M, Kannan A (2023) A comprehensive survey on machine learning-based intrusion detection systems for secure communication in internet of things. Comput Intell Neurosci 2023:8981988
Heinzelman W, Chandrakasan A, Balakrishnan H (2000) Energy-efficient communication protocols for wireless microsensor networks, Proceedings in Hawaaian international Conference on Systems Science, pp. 1–10. https://ieeexplore.ieee.org/abstract/document/926982
Heinzelman WB, Chandrakasan AP, Balakrishnan H (2002) An application-specific protocol architecture for wireless micro-sensor networks. IEEE Trans Wirel Commun 1(4):660–670
Haider W, Hu J, Slay J, Turnbull BP, **e Y (2017) Generating realistic intrusion detection system dataset based on fuzzy qualitative modelling. J Netw Comput Appl 87:185–192
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2009) A detailed analysis of the KDD CUP 99 data set, Proceedings of the IEEE Symposium on Computational Intelligence in Security and Defense Applications, pp 1–6. https://ieeexplore.ieee.org/abstract/document/5356528
Mishra P, Varadharajan V, Tupakula U, Pilli ES (2018) A detailed investigation and analysis of using machine learning techniques for Intrusion Detection. IEEE Commun Surv Tutor 21(1):686–728. https://doi.org/10.1109/COMST.2018.2847722
Elmasry W, Akbulut A, Zaim AH (2020) Evolving deep learning architectures for network intrusion detection using a double PSO metaheuristic. Comput Netw 168:1–21. https://doi.org/10.1016/j.comnet.2019.107042
Hibraj F, Vascon S, Stadelmann T, Pelillo M (2018) Speaker clustering using dominant sets. In 2018 24th International Conference on Pattern Recognition (ICPR), pp. 3549–3554. IEEE. https://ieeexplore.ieee.org/abstract/document/8546067
Pavan M, Pelillo M (2006) Dominant sets and pairwise clustering. IEEE Trans Pattern Analys Machine Intell 29(1):167–172
Author information
Authors and Affiliations
Contributions
K. Yesodha designed clustering algorithm and carried out the full system implementation, produced results and tested the system. She also prepared the manuscript. Dr. M. Krishnamurthy carried out literature survey, developed the ACO-based routing algorithm and also worked with clustering. Dr. K. Thangaramya developed the authentication model and trust modelling, and Dr. A. Kannan developed the ECC encryption, designed the overall system architecture and the integration of all the components.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Yesodha, K., Krishnamurthy, M., Thangaramya, K. et al. Elliptic curve encryption-based energy-efficient secured ACO routing protocol for wireless sensor networks. J Supercomput (2024). https://doi.org/10.1007/s11227-024-06235-1
Accepted:
Published:
DOI: https://doi.org/10.1007/s11227-024-06235-1