Abstract
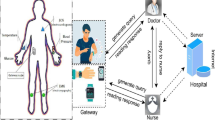
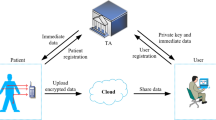
The Internet of Things (IoT) is becoming an essential aspect of digital healthcare information; the goal is to monitor various health parameters regularly to make healthcare management more efficient and convenient. Gateway devices can broadcast/multicast messages securely to sensors or intended recipients to guarantee the confidentiality of medical readings in the healthcare environment utilizing IoT sensors. In this context, designing and executing a key management framework is critical for the healthcare environment, and working with limited computing and processing capacities is also challenging. The literature on IoT key management is inclined toward centralized solutions, provides solutions with heavy computation and communication costs, and partially addresses resource-constrained devices that guarantee forward and backward secrecy in the healthcare domain. This paper constructs a group key management scheme with node joining and leaving scenarios to provide forward and backward secrecy focusing on lightweight computation. We use the concept of one-way accumulation for secret message exchange by combining elliptic curve cryptography. We designed a scheme that refreshed the established group key as the group’s size grows or shrinks, and the approach also applies to classical ciphers conveniently for the number of message exchanges for healthcare nodes. To demonstrate innovation in our method, we mathematically proved the soundness of our session key management scheme for the network model, and simulation findings show that the method is feasible as the processing and communication costs are reduced compared to related schemes.









Similar content being viewed by others
Data availability
Not applicable.
References
Rouhani S, Butterworth L, Simmons AD, Humphery DG, Deters R (2018) MediChainTM: a secure decentralized medical data asset management system. In: 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada. IEEE, pp 1533–1538
Darshan K, Anandakumar K (2015) A comprehensive review on usage of internet of things (IoT) in healthcare system. In: 2015 International Conference on Emerging Research in Electronics, Computer Science and Technology (ICERECT), Mandya, India. IEEE, pp 132–136
Yue X, Wang H, ** D, Li M, Jiang W (2016) Healthcare data gateways: found healthcare intelligence on blockchain with novel privacy risk control. J Med Syst 40(10):218
Kandi MA, Lakhlef H, Bouabdallah A, Challal Y (2019) An efficient multi-group key management protocol for heterogeneous IoT devices. In: 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, pp 1–6. https://doi.org/10.1109/WCNC.2019.8885613
Porambage P, Braeken A, Schmitt C, Gurtov A, Ylianttila M, Stiller B (2015) Group key establishment for enabling secure multicast communication in wireless sensor networks deployed for IoT applications. IEEE Access 3:1503–1511. https://doi.org/10.1109/ACCESS.2015.2474705
Sengupta J, Ruj S, Bit SD (2020) A comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J Netw Comput Appl 149:102481
Trnka M, Cerny T, Stickney N (2018) Survey of authentication and authorization for the internet of things. Secur Commun Netw 2018
Feroz Khan AB, Anandharaj G (2021) AHKM: an improved class of hash based key management mechanism with combined solution for single hop and multi hop nodes in IoT. Egypt Inf J 22(2):119–124. https://doi.org/10.1016/j.eij.2020.05.004
Gautam A, Kumar R (2021) A comprehensive study on key management, authentication and trust management techniques in wireless sensor networks. SN Appl Sci. https://doi.org/10.1007/s42452-020-04089-9
Lara E, Aguilar L, Sanchez MA, García JA (2020) Lightweight authentication protocol for M2M communications of resource-constrained devices in industrial internet of things. Sensors. https://doi.org/10.3390/s20020501
Álvarez-Bermejo JA, Lodroman A, López-Ramos JA (2017) Distributed key agreement for group communications based on elliptic curves. An application to sensor networks. Math Methods Appl Sci 39(16):4797–4809
Islam SH, Obaidat MS, Vijayakumar P, Abdulhay E, Li F, Reddy MKC (2018) A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for vanets. Future Gener Comput Syst 84:216–227
Benaloh J, De Mare M (1993) One-way accumulators: a decentralized alternative to digital signatures. In: Workshop on the Theory and Application of of Cryptographic Techniques. Springer, pp 274–285
Koblitz N (1987) Elliptic curve cryptosystems. Math Comput 48(177):203–209
Wang Q, Chen H, **e L, Wang K (2017) One-way hash chain-based self-healing group key distribution scheme with collusion resistance capability in wireless sensor networks. Ad Hoc Netw 11(8):2500–2511
Hankerson D, Menezes AJ, Vanstone S (2006) Guide to elliptic curve cryptography. Springer, New York
Jamil F, Ahmad S, Iqbal N, Kim D-H (2020) Towards a remote monitoring of patient vital signs based on IoT-based blockchain integrity management platforms in smart hospitals. Sensors 20(8):2195
Hassan WH et al (2019) Current research on internet of things (IoT) security: a survey. Comput Netw 148:283–294
Frustaci M, Pace P, Aloi G, Fortino G (2017) Evaluating critical security issues of the IoT world: present and future challenges. Internet Things J 5(4):2483–2495
Neshenko N, Bou-Harb E, Crichigno J, Kaddoum G, Ghani N (2019) Demystifying IoT security: an exhaustive survey on IoT vulnerabilities and a first empirical look on internet-scale IoT exploitations. IEEE Commun Surv Tutor
Dagher GG, Mohler J, Milojkovic M, Marella PB (2018) Ancile: privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology. Sustain Cities Soc 39:283–297
Forouzan BA (2007) Cryptography & network security. McGraw-Hill, Cambridge
Kabra A, Kumar S, Kasbekar GS (2020) Efficient, flexible and secure group key management protocol for dynamic IoT settings. ar**v preprint ar**v:2008.06890
Ahanger TA, Aljumah A (2018) Internet of things: a comprehensive study of security issues and defense mechanisms. IEEE Access 7:11020–11028
Karunarathne SM, Saxena N, Khan MK (2021) Security and privacy in IoT smart healthcare. IEEE Internet Comput 25(4):37–48. https://doi.org/10.1109/MIC.2021.3051675
Alhirabi N, Rana O, Perera C (2021) Security and privacy requirements for the internet of things: a survey. ACM Trans Internet Things. https://doi.org/10.1145/3437537
Ketu S, Mishra PK (2021) Internet of healthcare things: a contemporary survey. J Netw Comput Appl 192:103179. https://doi.org/10.1016/j.jnca.2021.103179
Qin Z, Zhang X, Feng K, Zhang Q, Huang J (2015) An efficient key management scheme based on ECC and AVL tree for large scale wireless sensor networks. Int J Distrib Sens Netw 11(9):691498
Wang Q, Chen H, **e L, Wang K (2016) One-way hash chain-based self-healing group key distribution scheme with collusion resistance capability in wireless sensor networks. Ad Hoc Netw 11(8):2500–2511
Eschenauer L, Gligor VD (2012) A key-management scheme for distributed sensor networks. In: Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC USA, pp 41–47
Shamir A (1979) How to share a secret. Commun ACM 22(11):612–613
Lu K, Qian Y, Guizani M, Chen H-H (2008) A framework for a distributed key management scheme in heterogeneous wireless sensor networks. IEEE Trans Wirel Commun 7(2):639–647
Nafi M, Bouzefrane S, Omar M (2020) Matrix-based key management scheme for IoT networks. Ad Hoc Netw 97:102003. https://doi.org/10.1016/j.adhoc.2019.102003
Zhan F, Yao N, Gao Z, Tan G (2017) A novel key generation method for wireless sensor networks based on system of equations. J Netw Comput Appl 82:114–127
Du W, Deng J, Han YS, Varshney PK, Katz J, Khalili A (2005) A pairwise key predistribution scheme for wireless sensor networks. ACM Trans Inf Syst Secur TISSEC 8(2):228–258
Gu H, Potkonjak M (2018) Efficient and secure group key management in IoT using multistage interconnected PUF. In: Proceedings of the International Symposium on Low Power Electronics and Design, pp 1–6
Kausar F, Aman W, Al-Abri D (2019) Mutually authenticated group key management protocol for healthcare IoT networks. In: Proceedings of the Future Technologies Conference, San Francisco, USA. Springer, pp 1–12
Azaria A, Ekblaw A, Vieira T, Lippman A (2016) MedRec: using blockchain for medical data access and permission management. In: 2016 2nd International Conference on Open and Big Data (OBD), Vienna, Austria. IEEE, pp 25–30
Liang X, Zhao J, Shetty S, Liu J, Li D (2017) Integrating blockchain for data sharing and collaboration in mobile healthcare applications. In: 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada. IEEE, pp 1–5
Steiner M, Tsudik G, Waidner M (1996) Diffie-Hellman key distribution extended to group communication. In: Proceedings of the 3rd ACM Conference on Computer and Communications Security, pp 31–37
**g Z, Chen M, Hongbo F (2017) WSN key management scheme based on fully bomomorphic encryption. In: 2017 29th Chinese Control and Decision Conference (CCDC), Chongqing, China. IEEE, pp 7304–7309
Ramkumar K, Singh R (2017) Key management using Chebyshev polynomials for mobile ad hoc networks. China Commun 14(11):237–246
Younis MF, Ghumman K, Eltoweissy M (2016) Location-aware combinatorial key management scheme for clustered sensor networks. IEEE Trans Parallel Distrib Syst 17(8):865–882
Raza S, Seitz L, Sitenkov D, Selander G (2016) S3K: scalable security with symmetric keys—DTLs key establishment for the internet of things. IEEE Trans Autom Sci Eng 13(3):1270–1280
Kothmayr T, Schmitt C, Hu W, Brünig M, Carle G (2018) DTLS based security and two-way authentication for the internet of things. Ad Hoc Netw 11(8):2710–2723
Yao W, Han S, Li X (2015) Lkh++ based group key management scheme for wireless sensor network. Wirel Pers Commun 83(4):3057–3073
Sun X, Wu X, Huang C, Xu Z, Zhong J (2016) Modified access polynomial based self-healing key management schemes with broadcast authentication and enhanced collusion resistance in wireless sensor networks. Ad Hoc Netw 37:324–336
Gandino F, Ferrero R, Montrucchio B, Rebaudengo M (2016) Fast hierarchical key management scheme with transitory master key for wireless sensor networks. IEEE Internet Things J 3(6):1334–1345. https://doi.org/10.1109/JIOT.2016.2599641
Swaminathan A, Vivekanandan P (2017) An effective lightweight key management (ELWKM) model for wireless sensor networks using distributed spanning tree structure. Asian J Res Soc Sci Hum 7(2):749–770
Mahmood Z, Ning H, Ghafoor A (2017) A polynomial subset-based efficient multi-party key management system for lightweight device networks. Sensors. https://doi.org/10.3390/s17040670
Tan H, Chung I (2018) A secure and efficient group key management protocol with cooperative sensor association in WBANS. Sensors. https://doi.org/10.3390/s18113930
Chi PW, Wang M-H (2018) Dynamic key management scheme in IoT. In: International Computer Symposium. Springer, pp 559–566
Dinker AG, Sharma V (2019) Polynomial and matrix based key management security scheme in wireless sensor networks. J Discrete Math Sci Cryptogr 22(8):1563–1575
Harbi Y, Aliouat Z, Refoufi A, Harous S, Bentaleb A (2019) Enhanced authentication and key management scheme for securing data transmission in the internet of things. Ad Hoc Netw 94:101948. https://doi.org/10.1016/j.adhoc.2019.101948
Esposito C, Ficco M, Castiglione A, Palmieri F, De Santis A (2020) Distributed group key management for event notification confidentiality among sensors. IEEE Trans Depend Secure Comput 17(3):566–580. https://doi.org/10.1109/TDSC.2018.2799227
Kumar V, Malik N, Dhiman G, Lohani TK (2021) Scalable and storage efficient dynamic key management scheme for wireless sensor network. Wirel Commun Mob Comput 2021 (2021)
De Ree M, Vizár D, Mantas G, Bastos J, Kassapoglou-Faist C, Rodriguez J (2021) A key management framework to secure IoMT-enabled healthcare systems. In: 2021 IEEE 26th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Porto, Portugal, pp 1–6. https://doi.org/10.1109/CAMAD52502.2021.9617796
Bao J, Zhang Y, Yi L, Li M (2022) Group key dynamic management method for wireless sensor network. In: Second International Conference on Sensors and Information Technology (ICSI 2022), Nan**g, China. SPIE, vol 12248, pp 119–124
Abdel Hakeem SA, Kim H (2022) Centralized threshold key generation protocol based on Shamir secret sharing and HMAC authentication. Sensors. https://doi.org/10.3390/s22010331
Chen HC, Christiana A (2014) A role-based RSA key management approach in a hierarchy scheme. In: 2014 Eighth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Birmingham, UK. IEEE, pp 258–264
Fan X, Gong G (2012) LPKM: a lightweight polynomial-based key management protocol for distributed wireless sensor networks. In: International Conference on Ad Hoc Networks, Paris, France. Springer, pp 180–195
Saied YB, Olivereau A (2019) Hip tiny exchange (TEX): a distributed key exchange scheme for hip-based internet of things. In: Third International Conference on Communications and Networking, Hammamet, Tunisia. IEEE, pp 1–8
Okamoto E, Tanaka K (1989) Key distribution system based on identification information. IEEE J Sel Areas Commun 7(4):481–485
Braeken A (2022) Authenticated key agreement protocols for dew-assisted IoT systems. J Supercomput 1–21
Messai M-L, Seba H, Aliouat M (2015) A lightweight key management scheme for wireless sensor networks. J Supercomput 71(12):4400–4422
De Meulenaer G, Gosset F, Standaert F-X, Pereira O (2008) On the energy cost of communication and cryptography in wireless sensor networks. In: 2008 IEEE International Conference on Wireless and Mobile Computing, Networking and Communications, Avignon, France. IEEE, pp 580–585
Funding
No funds, grants, or other support was received.
Author information
Authors and Affiliations
Contributions
All the authors have equally contributed.
Corresponding author
Ethics declarations
Conflict of interest
The authors have no conflicts of interest to declare that are relevant to the content of this article.
Consent to participate
Yes.
Consent for publication
Yes.
Ethics approval
Yes.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Trivedi, C., Rao, U.P. Secrecy aware key management scheme for Internet of Healthcare Things. J Supercomput 79, 12492–12522 (2023). https://doi.org/10.1007/s11227-023-05144-z
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-023-05144-z