Abstract
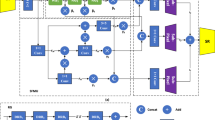
In recent years, deep learning has been used in steganography scheme, and the implemented solution had a large hidden capacity. In order to further study the effect of basic deep learning network on image steganography, a deep learning image steganography scheme based on ResNet was proposed in this paper, which applied the idea of residual blocks in ResNet to the field of image steganography. Image hiding and image extraction were realized by encoder network and decoder network. In the proposed scheme, by setting the balance parameter during training, different hiding and extraction qualities could be obtained for different scenarios. At the same time, a new performance analysis method was proposed for the field of deep steganography: the scatter plots of PSNR and SSIM. For a test set with a large amount of data, it could clearly reflect the performance of the solution, and it had a certain degree of application value in the field of deep steganography. The experimental results showed that the scheme had better invisibility when hiding, high data accuracy when extracting, and had certain advantages compared with the existing scheme. And it performed better when detected by steganalysis tools.








Similar content being viewed by others
References
Abdulla AA, Jassim SA, Sellahewa H (2013) Secure Steganography technique based on bitplane indexes. In: 2013 IEEE International Symposium on Multimedia, 9–11, 287–291. https://doi.org/10.1109/ISM.2013.55
Abdulla AA, Sellahewa H, Jassim SA (2014) Stego quality enhancement by message size reduction and fibonacci bit-plane map**. In: Chen L, Mitchell C (eds) Security Standardisation Research. Springer International Publishing, Cham, pp 151–166
Abdulla AA, Sellahewa H, Jassim SA (2019) Improving embedding efficiency for digital steganography by exploiting similarities between secret and cover images. Multimed Tools Appl 78(13):17799–17823. https://doi.org/10.1007/s11042-019-7166-7
Baluja S (2017) Hiding images in plain sight: Deep steganography. In: Proceedings of the 31st International Conference on Neural Information Processing Systems, 2066–2076
Boehm B (2014) StegExpose - a tool for detecting LSB steganography journal. https://doi.org/10.48550/ar**v.1410.6656
Chen BJ, Wang JX, Chen YY, ** ZL, Shim HJ, Shi YQ (2020) High-capacity robust image steganography via adversarial network. Ksii Trans Internet Inform Syst 14(1):366–381. https://doi.org/10.3837/tiis.2020.01.020
Duan XT, Jia K, Li BX, Guo DD, Zhang E, Qin C (2019) Reversible image steganography scheme based on a U-Net structure. IEEE Access 7:9314–9323. https://doi.org/10.1109/access.2019.2891247
Duan X, Wang W, Liu N, Yue D, **e Z, Qin C (2020) StegoPNet: Image steganography with generalization ability based on pyramid pooling module. IEEE Access 8:195253–195262. https://doi.org/10.1109/ACCESS.2020.3033895
Duan XT, Liu N, Gou MX, Wang WX, Qin C (2020) SteganoCNN: Image steganography with generalization ability based on convolutional neural network. Entropy 22(10). https://doi.org/10.3390/e22101140
Duan X, Guo D, Liu N, Li B, Qin C (2020) A new high capacity image steganography method combined with image elliptic curve cryptography and deep neural network. IEEE Access 99:1–1
Duan XT, Gou MX, Liu N, Wang WX, Qin C (2020) High-capacity image steganography based on improved Xception. Sensors 20(24). https://doi.org/10.3390/s20247253
Duan X, Li B, **e Z, Yue D, Ma Y (2021) High-capacity information hiding based on residual network. IETE Tech Rev 38(1):172–183. https://doi.org/10.1080/02564602.2020.1808097
Everingham M, VanGool L, Williams CKI, Winn J, Zisserman A (2012) The pascal visual object classes challenge 2012 (voc2012) results (2012)[C]//URL http://www.pascalnetwork.org/challenges/VOC/voc2012/workshop/index.html
Gao GY, Tong SK, **a ZH, Wu B, Xu LY, Zhao ZQ (2021) Reversible data hiding with automatic contrast enhancement for medical images. Sig Process 178. https://doi.org/10.1016/j.sigpro.2020.107817
Goodfellow IJ, Pouget-Abadie J, Bengio Y (2014) Generative Adversarial Nets, 28th Conference on Neural Information Processing Systems (NIPS), 27, 2672–2680
He K, Zhang X, Ren S, Sun J (2016) Deep residual learning for image recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition, 770–778
Li C, Jiang Y, Cheslyar M (2018) Embedding image through generated intermediate medium using deep convolutional generative adversarial network. Comput Mater Continua 56(2):313–324
Li Q, Wang XY, Wang XY, Ma B, Wang CP, **an YJ, Shi YQ (2020) A novel grayscale image steganography scheme based on chaos encryption and generative adversarial networks. IEEE Access 8:168166–168176. https://doi.org/10.1109/access.2020.3021103
Liu B, Liu Q, Zhu Z, Zhang T, Yang Y (2019) MSST-ResNet: Deep multi-scale spatiotemporal features for robust visual object tracking. Knowl Based Syst 164:235–252. https://doi.org/10.1016/j.knosys.2018.10.044
Liu Q, **. Knowl Based Syst 192:15. https://doi.org/10.1016/j.knosys.2019.105375
Meng R, Rice SG, Wang J, Sun X (2018) A fusion steganographic algorithm based on faster R-CNN. Comput Mater Continua 55(1):1–16
Meng L, Liu L, Tian G, Wang X (2021) An adaptive reversible watermarking in IWT domain. Multimed Tools Appl 80(1):711–735. https://doi.org/10.1007/s11042-020-09686-9
Naito H, Zhao Q (2019) A new steganography method based on generative adversarial networks. In: 2019 IEEE 10th International Conference on Awareness Science and Technology (iCAST), 23–25. 1–6. https://doi.org/10.1109/ICAwST.2019.8923579
Ouahabi A, Taleb-Ahmed A (2021) Deep learning for real-time semantic segmentation: Application in ultrasound imaging. Pattern Recognit Lett 144:27–34. https://doi.org/10.1016/j.patrec.2021.01.010
Rehman Au, Rahim R, Nadeem S, Hussain S (2019) End-to-end trained CNN Encoder-decoder networks for image steganography. In: LealTaixe L, Roth S (eds) Computer Vision - Eccv 2018 Workshops, Pt Iv, vol 11132. Lecture Notes in Computer Science, 723–729. https://doi.org/10.1007/978-3-030-11018-5_64
Ronneberger O, Fischer P, Brox T (2015) U-Net: Convolutional networks for biomedical image segmentation. In: International Conference on Medical Image Computing and Computer-Assisted Intervention. Germany
Russakovsky O, Deng J, Su H, Krause J, Satheesh S, Ma S, Huang Z, Karpathy A, Khosla A, Bernstein M, Berg AC, Fei-Fei L (2015) ImageNet large scale visual recognition challenge. Int J Comput Vis 115(3):211–252. https://doi.org/10.1007/s11263-015-0816-y
Shi Y-Q, Li X, Zhang X, Wu H-T, Ma B (2016) Reversible data hiding: Advances in the past two decades. IEEE Access 4:3210–3237. https://doi.org/10.1109/access.2016.2573308
Tang W, Tan S, Li B, Huang J (2017) Automatic steganographic distortion learning using a generative adversarial network. IEEE Signal Process Lett 24(10):1547–1551. https://doi.org/10.1109/LSP.2017.2745572
Wang H, Qian Z, Feng G, Zhang X (2020) Defeating data hiding in social networks using generative adversarial network. EURASIP J Image Video Process 2020(1):30. https://doi.org/10.1186/s13640-020-00518-2
Wu P, Yang Y, Li XQ (2018) Image-into-Image Steganography Using Deep Convolutional Network. In: Hong R, Cheng WH, Yamasaki T, Wang M, Ngo CW (eds) Advances in Multimedia Information Processing - Pcm 2018, Pt Ii, vol 11165. Lecture Notes in Computer Science, 792–802. https://doi.org/10.1007/978-3-030-00767-6_73
Yedroudj M, Comby M (2018) Chaumont Yedroudj-Net: An efficient CNN for spatial steganalysis. ICASSP: International Conference on Acoustics, Speech and Signal Processing, Calgary, Alberta, Canada. 2092–2096. https://doi.org/10.1109/ICASSP.2018.8461438
Yu C (2020) Attention based data hiding with generative adversarial networks. Proceedings of the AAAI Conference on Artificial Intelligence, 34(01), 1120–1128. https://doi.org/10.1609/aaai.v34i01.5463
Zhu J, Kaplan R, Johnson J, Fei-Fei L (2018) HiDDeN: Hiding data with deep networks. In: Ferrari V, Hebert M, Sminchisescu C, Weiss Y (eds) Computer Vision – ECCV 2018. Springer International Publishing, Cham, pp 682–697
Acknowledgements
This work was supported in part by National Natural Science Foundation of China (No. 61976126), Shandong Natural Science Foundation (No. ZR2019MF003).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors certify that they have no affiliations with or involvement in any organization or entity with any financial interest or non-financial interest in the subject matter or materials discussed in this manuscript.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Liu, L., Meng, L., Wang, X. et al. An image steganography scheme based on ResNet. Multimed Tools Appl 81, 39803–39820 (2022). https://doi.org/10.1007/s11042-022-13206-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13206-2