Abstract
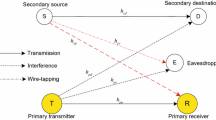
We investigate the secrecy outage performance of maximal ratio combining (MRC) in cognitive radio networks over Rayleigh fading channels. In a single-input multiple-output wiretap system, we consider a secondary user (SU-TX) that transmits confidential messages to another secondary user (SU-RX) equipped with M (M ≥ 1) antennas where the MRC technique is adopted to improve its received signal-to-noise ratio. Meanwhile, an eavesdropper equipped with N (N ≥ 1) antennas adopts the MRC scheme to overhear the information between SU-TX and SU-RX. SU-TX adopts the underlay strategy to guarantee the service quality of the primary user without spectrum sensing. We derive the closed-form expressions for an exact and asymptotic secrecy outage probability.
Similar content being viewed by others
References
Alves, H., Souza, R.D., Debbah, M., et al., 2012. Performance of transmit antenna selection physical layer security schemes. IEEE Signal Process. Lett., 19(6): 372–375. http://dx.doi.org/10.1109/LSP.2012.2195490
Elkashlan, M., Wang, L., Duong, T.Q., et al., 2015. On the security of cognitive radio networks. IEEE Trans. Veh. Technol., 64(8): 3790–3795. http://dx.doi.org/10.1109/TVT.2014.2358624
Gradshteyn, I.S., Ryzhik, I.M., 2007. Table of Integrals, Series, and Products. Academic Press, New York.
He, F.M., Man, H., Wang, W., 2011. Maximal ratio diversity combining enhanced security. IEEE Commun. Lett., 15(5): 509–511. http://dx.doi.org/10.1109/LCOMM.2011.030911.102343
Lee, J., Wang, H., Andrews, J.G., et al., 2011. Outage probability of cognitive relay networks with interference constraints. IEEE Trans. Wirel. Commun., 10(2): 390–395. http://dx.doi.org/10.1109/TWC.2010.120310.090852
Liu, H.Q., Zhao, H., Jiang, H., et al., 2016). Physical-layer secrecy outage of spectrum sharing CRsystems over fading channels. Sci. China Inform. Sci., in press. http://dx.doi.org/10.1007/s11432-015-5451-2
Liu, Y.W., Wang, L.F., Duy, T.T., et al., 2015. Relay selection for security enhancement in cognitive relay networks. IEEE Wirel. Commun. Lett., 4(1): 46–49. http://dx.doi.org/10.1109/LWC.2014.2365808
Liu, Y.W., Wang, L.F., Zaidi, S.A.R., et al., 2016. Secure D2D communication in large-scale cognitive cellular networks: a wireless power transfer model. IEEE Trans. Commun., 64(1): 329–342. http://dx.doi.org/10.1109/TCOMM.2015.2498171
Pan, G.F., Tang, C.Q., Zhang, X., et al., 2015. Physical layer security over non-small scale fading channels. IEEE Trans. Veh. Techol., 65(3): 1326–1339. http://dx.doi.org/10.1109/TVT.2015.2412140
Papoulis, A., Pillai, S.U., 2002. Two Random Variables. In: Howell, R.L., Morriss, J.M. (Eds.), Probability, Random Variables and Stochastic Processes. Tata McGraw-Hill Education, Noida, p.124–148.
Prudnikov, A.P., Brychkov, Y.A., Marichev, O.I., 1986. Elementary Functions. In: Queen, N.M., translator, Integrals and Series. Gordon and Breach Science Publishers, Philadelphia, p.11–45.
Shiu, Y.S., Chang, S.Y., Wu, H.C., et al., 2011. Physical layer security in wireless networks: a tutorial. IEEE Wirel. Commun., 18(2): 66–74. http://dx.doi.org/10.1109/MWC.2011.5751298
Sun, X.J., Wang, J.H., Xu, W., et al., 2012. Performance of secure communications over correlated fading channels. IEEE Signal Process. Lett., 19(8): 479–482. http://dx.doi.org/10.1109/LSP.2012.2203302
Tang, C.Q., Pan, G.F., Li, T.T., 2014. Secrecy outage analysis of underlay cognitive radio unit over Nakagamim fading channels. IEEE Wirel. Commun. Lett., 3(6): 609–612. http://dx.doi.org/10.1109/LWC.2014.2350501
Wang, L.F., Yang, N., Elkashlan, M., et al., 2014. Physical layer security of maximal ratio combining in two-wave diffuse power fading channels. IEEE Trans. Inform. Foren. Sec., 9(2): 247–258. http://dx.doi.org/10.1109/TIFS.2013.2296991
Wang, Q.H., Wang, H.M., Yin, Q.Y., 2014. Distributed beamforming for multi-relay cognitive radio systems. Sci. China Inform. Sci., 44(8): 980–992 (in Chinese). http://dx.doi.org/10.1360/N112013-00174
Yang, N., Suraweera, H.A., Collings, I.B., et al., 2013a. Physical layer security of TAS/MRC with antenna correlation. IEEE Trans. Inform. Foren. Sec., 8(1): 254–259. http://dx.doi.org/10.1109/TIFS.2012.2223681
Yang, N., Yeoh, P.L., Elkashlan, M., et al., 2013b. Transmit antenna selection for security enhancement in MIMO wiretap channels. IEEE Trans. Commun., 61(1): 144–154. http://dx.doi.org/10.1109/TCOMM.2012.12.110670
Zhang, X., Pan, G.F., Tang, C.Q., et al., 2014). Performance analysis of physical layer security over independent/correlated log-normal fading channels. IEEE Telecommunication Networks and Applications Conf., p.23–27. http://dx.doi.org/10.1109/ATNAC.2014.7020868
Zhao, H., Pan, G.F., 2016. The analysis on secure communications for DF and RF relaying SIMO system with Gauss errors. Sci. China Inform. Sci., 46(3): 350–360 (in Chinese).
Zhao, H., Liu, H.Q., Liu, Y.P., et al., 2015. Physical layer security of maximal ratio combining in underlay cognitive radio unit over Rayleigh fading channels. IEEE Int. Conf. on Communication Software and Networks, p.201–205. http://dx.doi.org/10.1109/ICCSN.2015.7296154
Zou, Y.L., Champagne, B., Zhu, W.P., et al., 2015. Relayselection improves the security-reliability trade-off in cognitive radio systems. IEEE Trans. Commun., 63(1): 215–228. http://dx.doi.org/10.1109/TCOMM.2014.2377239
Author information
Authors and Affiliations
Corresponding author
Additional information
Project supported in part by the National Natural Science Foundation of China (Nos. 61401372 and 61531016), the Research Fund for the Doctoral Program of Higher Education of China (No. 20130182120017), the Natural Science Foundation of CQ CSTC (No. cstc2013jcyjA40040), and the Fundamental Research Funds for the Central Universities, China (No. XDJK2015B023)
A preliminary version was presented at the 7th IEEE International Conference on Communication Software and Networks, China, June 6–7, 2015
ORCID: Gao-feng PAN, http://orcid.org/0000-0003-1008-5717
Rights and permissions
About this article
Cite this article
Zhao, H., Wang, Dy., Tang, Cq. et al. Physical layer security of underlay cognitive radio using maximal ratio combining. Frontiers Inf Technol Electronic Eng 17, 929–937 (2016). https://doi.org/10.1631/FITEE.1500351
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1631/FITEE.1500351
Keywords
- Cognitive radio networks
- Maximal ratio combining
- Secrecy outage probability
- Single-input multiple-output