Abstract
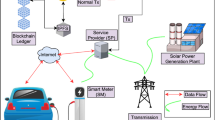
The Smart Grid represents a modernized electrical infrastructure integrating information and communication technology for bidirectional data exchange between power providers and consumers. This advancement enables seamless digital connectivity among intelligent devices such as Smart Meters, Demand Response Control Units, and Service Providers, facilitating remote data management for optimized energy distribution. However, the reliance on unsecured wireless communication channels poses significant security vulnerabilities, including replay, impersonation, man-in-the-middle, and physical capture attacks. To address these challenges, this study introduces a pioneering approach called Deep-Learning and Blockchain-enabled Secure Data Sharing. Specifically, Deep-Learning techniques are leveraged to develop an effective Intrusion Detection System. The proposed RENS (intRusion detEction aNd clasSification) combines Variational AutoEncoder with Attention-based Bidirectional Long Short-Term Memory for feature extraction and attack detection. Moreover, normal instances identified by RENS are utilized in a blockchain-based access control mechanism, ensuring secure and immutable data exchange among Smart Grid entities. In this framework, participating Service Providers form a peer-to-peer network responsible for generating blocks associated with individual SMs. These blocks undergo validation and are appended to a private blockchain ledger using a smart contract-based Proof-of-Authentication consensus mechanism. Experimental results and security analysis demonstrate the superiority of the DBSDS framework over conventional BiLSTM techniques, confirming its effectiveness in safeguarding Smart Grid operations.












Similar content being viewed by others
References
Siniosoglou, I.; Radoglou-Grammatikis, P.; Efstathopoulos, G.; Fouliras, P.; Sarigiannidis, P.: A unified deep learning anomaly detection and classification approach for smart grid environments. IEEE Trans. Netw. Serv. Manage. 18(2), 1137–1151 (2021)
Valuates Reports. Smart grid market size, Online; Accessed 15 Mar 2021 (2020)
Tsai, J.-L.; Lo, N.-W.: Secure anonymous key distribution scheme for smart grid. IEEE Trans. Smart Grid 7(2), 906–914 (2015)
Odelu, V.; Das, A.K.; Wazid, M.; Conti, M.: Provably secure authenticated key agreement scheme for smart grid. IEEE Trans. Smart Grid 9(3), 1900–1910 (2016)
Park, K.; Lee, J.; Das, A.K.; Park, Y.: Bpps: blockchain-enabled privacy-preserving scheme for demand-response management in smart grid environments. IEEE Trans. Depend. Secure Comput., pp. 1–1 (2022)
Kawoosa, A.I..; Prashar, D.: A review of cyber securities in smart grid technology. In: 2021 2nd International Conference on Computation, Automation and Knowledge Management (ICCAKM), pp. 151–156. IEEE (2021)
Llaria, A.; Dos Santos, J.; Terrasson, G.; Boussaada, Z.; Merlo, C.; Curea, O.: Intelligent buildings in smart grids: a survey on security and privacy issues related to energy management. Energies 14(9), 2733 (2021)
Tightiz, L.; Yang, H.: A comprehensive review on iot protocols’ features in smart grid communication. Energies 13(11), 2762 (2020)
Almudayni, Z.; Soh, B.; Li, A.: A comprehensive study on the energy efficiency of iot from four angles: Clustering and routing in wsns, smart grid, fog computing and mqtt & coap application protocols. In: International Conference on Internet of Things as a Service, pp. 54–70. Springer (2021)
Azzedin, F.; Alhazmi, T.: Secure data distribution architecture in iot using mqtt. Appl. Sci. 13(4), 2515 (2023)
Azzedin, F.; Alhejri, I.: A layered taxonomy of internet of things attacks. In: Proceedings of the 6th International Conference on Future Networks and Distributed Systems, pp. 631–636 (2022)
Sasi, T.; Lashkari, A.H.; Lu, R.; **ong, P.; Iqbal, S.: A comprehensive survey on iot attacks: taxonomy, detection mechanisms and challenges. J. Inf. Intell. (2023)
Azzedin, F.; Albinali, H.: Security in internet of things: Rpl attacks taxonomy. In: The 5th International Conference on Future Networks and Distributed Systems, pp. 820–825 (2021)
Kumar, P.; Gupta, G.P.; Tripathi, R.: Tp2sf: a trustworthy privacy-preserving secured framework for sustainable smart cities by leveraging blockchain and machine learning. J. Syst. Archit. 115, 101954 (2021)
Mall, P.; Amin, R.; Das, A.K.; Leung, M.T.; Choo, K.-K.R.: Puf-based authentication and key agreement protocols for iot, wsns and smart grids: a comprehensive survey. IEEE Internet Things J., pp. 1–1 (2022)
Kumar, N.; Aujla, G.S.; Das, A.K.; Conti, M.: Eccauth: a secure authentication protocol for demand response management in a smart grid system. IEEE Trans. Ind. Inf. 15(12), 6572–6582 (2019)
Srinivas, J.; Das, A.K.; Li, X.; Khan, M.K.; Jo, M.: Designing anonymous signature-based authenticated key exchange scheme for internet of things-enabled smart grid systems. IEEE Trans. Ind. Inf. 17(7), 4425–4436 (2020)
Wazid, M.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C.: Secure three-factor user authentication scheme for renewable-energy-based smart grid environment. IEEE Trans. Ind. Inf. 13(6), 3144–3153 (2017)
Zhuang, P.; Zamir, T.; Liang, H.; Zhuang, P.; Zamir, T.; Liang, H.: Blockchain for cybersecurity in smart grid: a comprehensive survey. IEEE Trans. Ind. Inf. 17(1), 3–19 (2020)
Mollah, M.B.; Zhao, J.; Niyato, D.; Lam, K.-Y.; Zhang, X.; Ghias, A.M.Y.M.; Koh, L.H.; Yang, L.: Blockchain for future smart grid: a comprehensive survey. IEEE Internet Things J. 8(1), 18–43 (2020)
Kumar, R.; Kumar, P.; Tripathi, R.; Gupta, G.P.; Kumar, N.; Hassan, M.M.: A privacy-preserving-based secure framework using blockchain-enabled deep-learning in cooperative intelligent transport system. IEEE Tran. Intell. Transport. Syst., pp. 1–12 (2021)
Bera, B.; Saha, S.; Das, A.K.: Designing blockchain-based access control protocol in iot-enabled smart-grid system. IEEE Internet Things J. 8(7), 5744–5761 (2020)
Gai, K.; Yulu, W.; Zhu, L.; Lei, X.; Zhang, Y.: Permissioned blockchain and edge computing empowered privacy-preserving smart grid networks. IEEE Internet Things J. 6(5), 7992–8004 (2019)
Hasan, M.K.; Habib, A.K.M.A.; Shukur, Z.; Ibrahim, F.; Islam, S.; Razzaque, M.A.: Review on cyber-physical and cyber-security system in smart grid: standards, protocols, constraints, and recommendations. J. Netw. Comput. Appl. 209, 103540 (2023)
Kumar, R.; Javeed, D.; Aljuhani, A.; Jolfaei, A.; Kumar, P.; Islam, A.K.M.N.: Blockchain-based authentication and explainable ai for securing consumer iot applications. IEEE Trans. Consumer Electron. (2023)
Kumar, P.; Kumar, R.; Islam, A.K.M.N.; Garg, S.; Kaddoum, G.; Han, Z.: Distributed ai and blockchain for 6g-assisted terrestrial and non-terrestrial networks: challenges and future directions. IEEE Netw. 37(2), 70–77 (2023)
Javeed, D.; Gao, T.; Saeed, M.S.; Kumar, P.; Kumar, R.; Jolfaei, A.: A softwarized intrusion detection system for iot-enabled smart healthcare system. ACM Trans. Internet Technol. (2023)
Kumar, P.; Gupta, G.P.: Toward design of an intelligent cyber attack detection system using hybrid feature reduced approach for iot networks. Arab. J. Sci. Eng. 46, 3749–3778 (2021)
Lv, L.; Wu, Z.; Zhang, L.; Gupta, B.B.: An edge-ai based forecasting approach for improving smart microgrid efficiency. IEEE Trans. Ind. Inf. 18(11), 7946–7954 (2022)
Assi, M.; Haraty, R.A.; Thoumi, S.; Kaddoura, S.; Belal, N.A.: Scheduling household appliances using genetic algorithms. In: 2022 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), pp. 1–6 (2022)
Kumar, P.; Tripathi, R.; Gupta, G.P.: P2idf: a privacy-preserving based intrusion detection framework for software defined internet of things-fog (sdiot-fog). In: Adjunct Proceedings of the 2021 International Conference on Distributed Computing and Networking, ICDCN ’21, pp. 37–42, New York, NY, USA, Association for Computing Machinery (2021)
Kumar, P.; Gupta, G.P.; Tripathi, R.: Design of anomaly-based intrusion detection system using fog computing for iot network. Autom. Control. Comput. Sci. 55(2), 137–147 (2021)
Alkahtani, H.; Aldhyani, T.H.H.: Intrusion detection system to advance internet of things infrastructure-based deep learning algorithms. Complexity (2021)
Khoei, T.T.; Aissou, G.: When Chen Hu, and Naima Kaabouch. Ensemble learning methods for anomaly intrusion detection system in smart grid. In: 2021 IEEE International Conference on Electro Information Technology (EIT), pp. 129–135. IEEE (2021)
Khan, S.; Kifayat, K.; Kashif B.A.; Gurtov, A.; Hassan, M.: Intelligent intrusion detection system in smart grid using computational intelligence and machine learning. Trans. Emerg. Telecommun. Technol., 32(6), e4062 (2021)
Li, D.; Peng, W.; Deng, W.; Gai, F.: A blockchain-based authentication and security mechanism for IoT. In: 2018 27th International Conference on Computer Communication and Networks (ICCCN), pp. 1–6. IEEE (2018)
Dehalwar, V.; Kolhe, M.L.; Deoli, S.; Jhariya, M.K.: Blockchain-based trust management and authentication of devices in smart grid. Clean. Eng. Technol., 8, 100481 (2022)
Kumar, P.; Kumar, R.; Gupta, G.P.; Tripathi, R.; Srivastava, G.: P2tif: a blockchain and deep learning framework for privacy-preserved threat intelligence in industrial iot. IEEE Trans. Ind. Inform., pp. 1–1 (2022)
Kumar, R.; Kumar, P.; Tripathi, R.; Gupta, G.P.; Islam, A.K.M.N.; Shorfuzzaman, M.: Permissioned blockchain and deep-learning for secure and efficient data sharing in industrial healthcare systems. IEEE Trans. Ind. Inform., pp. 1–1 (2022)
Kumar, P.; Gupta, G.P.; Tripathi, R.: A review on intrusion detection systems and cyber threat intelligence for secure iot-enabled networks. In: Big Data Analytics in Fog-Enabled IoT Networks: Towards a Privacy and Security Perspective, p. 51 (2023)
Kumar, P.; Kumar, R.; Gupta, G.P.; Tripathi, R.: Bdedge: blockchain and deep-learning for secure edge-envisioned green cavs. IEEE Trans. Green Commun. Netw. 6(3), 1330–1339 (2022)
Kumar, R.; Kumar, P.; Tripathi, R.; Gupta, G.P.; Hassan, M.M.: Bdtwin: an integrated framework for enhancing security and privacy in cybertwin-driven automotive industrial internet of things. IEEE Internet Things J. 9(18), 17110–17119 (2021)
Dolev, D.; Yao, A.: On the security of public key protocols. IEEE Trans. Inf. Theory 29(2), 198–208 (1983)
Moustafa, N.: Dr Ton-iot datasets for cybersecurity applications based artificial intelligence. [Online; Accessed 10 Dec 2021] (2019)
Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B.: Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: bot-iot dataset. Futur. Gener. Comput. Syst. 100, 779–796 (2019)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kumar, C., Chittora, P. Deep-Learning and Blockchain-Empowered Secure Data Sharing for Smart Grid Infrastructure. Arab J Sci Eng (2024). https://doi.org/10.1007/s13369-024-08882-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s13369-024-08882-1