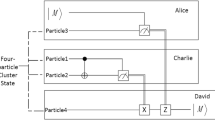
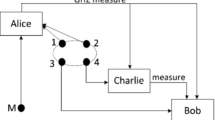
Abstract
An arbitrated quantum multi-proxy blind signature scheme, which is based on four-qubit cluster states, is proposed in this paper. This scheme satisfies all the characteristics of a multi-proxy blind signature scheme. To guarantee the security of this scheme, some quantum technologies such as quantum key distribution (QKD) protocol, eavesdrop** check, quantum one-time pad and quantum secure direct communication (QSDC) protocol are used. Analysis results show that our scheme is secure.

Similar content being viewed by others
References
Ekert, A.: Quantum cryptography based on Bell theorem. Phys. Rev. Lett. 67, 661–664 (1991)
Bennett, C.H.: Quantum cryptography using any two non-orthogonal states. Phys. Rev. Lett. 68, 3121–3124 (1992)
Lin, S., Wang, H., Guo, G.D., Ye, G.H.: Authenticated multi-user quantum key distribution with single particles. Int. J. Quantum Inform. 14, 1650002 (2016)
Hang, P., Zhu, J., He, G.Q., et al.: A modified quantum key distribution without public announcement bases against photon-number-splitting attack. Int. J. Theor. Phys. 51, 2514–2523 (2012)
Hillery, M., Buzek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829–1834 (1999)
Karlsson, A., Koashi, M., Imoto, N.: Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 59(1), 162–168 (1999)
Cleve, R., Gottesman, D., Lo, H.K.: How to share a quantum secret. Phys. Rev. Lett. 83, 648–651 (1999)
**ao, L., Long, G.L., Deng, F.G., et al.: Efficient multiparty quantum secret sharing schemes. Phys. Rev. A 69(5), 052307 (2004)
Yang, Y.G., Cao, W.F., Wen, Q.Y.: Three-party quantum secret sharing of secure direct communication based on chi-type entangled states. Chin. Phys. B 19(5), 050306 (2010)
Yang, Y.G., Wang, Y., Teng, Y.W., Wen, Q.Y.: Universal three-party quantum secret sharing against collective noise. Commun. Theor. Phys. 55(4), 589–593 (2011)
Zhang, Z.J., Yang, J., Man, Z.X., et al.: Multiparty secret sharing of quantum information using and identifying Bell states. Eur. Phys. J. D 33, 133–136 (2005)
Yan, F.L., Gao, T., Li, Y.C.: Quantum secret sharing between multiparty and multiparty with four states. Sci. China Ser. G-Phys. Mech. Astron. 50(5), 572–580 (2007)
Wang, T.Y., Wen, Q.Y., Zhu, F.C.: Secure authentication of classical messages with single photons. Chin. Phys. B 18, 3189–3192 (2009)
Wang, T.Y., Wen, Q.Y., Zhu, F.C.: Secure authentication of classical messages with decoherence-free states. Opt. Commun. 282, 3382–3385 (2009)
He, Y.F., Ma, W.P.: Quantum key agreement protocols with four-qubit cluster states. Quantum Inf. Process. 14(9), 3483–3498 (2015)
He, Y.F., Ma, W.P.: Two-party quantum key agreement based on four-particle GHZ states. Int. J. Quantum Inf. 14(1), 1650007 (2016)
He, Y.F., Ma, W.P.: Two-party quantum key agreement against collective noise. Quantum Inf. Process. 15(12), 5023–5035 (2016)
Boström, K., Felbinger, T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89, 187902 (2002)
Yang, C.W., Tsai, C.W., Hwang, T.: Fault tolerant two-step quantum secure direct communication protocol against collective noises. Sci. China-Phys. Mech. Astron. 54(3), 496–501 (2011)
Cao, W.F., Yang, Y.G., Wen, Q.Y.: Quantum secure direct communication with cluster states. Sci. China-Phys. Mech. Astron. 53(7), 1271–1275 (2010)
Deng, F.G., Long, G.L., Liu, X.S.: Two-step quantum direct communication protocol using the Einstein-Podolsky-Rosen pair block. Phys. Rev. A 68(4), 042317 (2003)
Gu, B., Zhang, C.Y., Cheng, G.S., et al.: Robust quantum secure direct communication with a quantum one-time pad over a collective-noise channel. Sci. China-Phys. Mech. Astron. 54(5), 942–947 (2011)
Long, G.L., Wang, C., Li, Y.S.: Quantum secure direct communication (in Chinese). Sci. Sin-Phys. Mech. Astron. 41, 332–342 (2011)
Nie, Y.Y., Li, Y.H., Wang, Z.S.: Semi-quantum information splitting using GHZ-type states. Quantum Inf. Process. 12(1), 437–448 (2013)
Ye, T.Y., Jiang, L.Z.: False alarm probability of eavesdrop** checks for controllable quantum secret sharing. Acta Photon. Sin. 41(9), 1113–1117 (2012)
Sheng, Y.B., Zhou, L., Zhao, S.M.: Efficient two-step entanglement concentration for arbitrary W states. Phys. Lett. A 85(4), 042302 (2012)
Li, Y.H., Liu, J.C., Nie, Y.Y.: Quantum identification scheme of cross-center based on W-state. Acta Photon. Sin. 39(9), 1616–1620 (2010)
Zhou, X.Q., Wu, Y.W.: Token-bus network fidelity of quantum teleportation by three-photon entangled W state. Acta Photon. Sin. 39(11), 2093–2096 (2010)
Briegel, H.J., Raussendorf, R.: Persistent entanglement in arrays of interacting particles. Phys. Rev. Lett. 86(5), 910–913 (2001)
Gottesman, D., Chuang, I.L.: Quantum digital signature. ar**v:quant-ph/0105032v2 (2001)
Wen, X.J., Liu, Y., Sun, Y.: Quantum multi-signature protocol based on teleportation. Z. Naturforsch. A 62(3–4), 147–151 (2007)
Zeng, G.H., Keitel, C.H.: Arbitrated quantum-signature scheme. Phys. Rev. A 65(4), 042312 (2002)
Mambo, M., Usuda, K., Okamoto, E.: Proxy signatures for delegating signing operation. In: Proceedings of the 3rd ACM Conference on Computer and Communications Security, pp. 48–57, New Delhi (1966)
Cao, H.J., Huang, J., et al.: A quantum proxy signature scheme based on genuine five-qubit entangled state. Int. J. Theor. Phys. 53, 3095–3100 (2014)
Zeng, C., Zhang, J.Z., **e, S.C.: A quantum proxy blind signature scheme based on genuine five-qubit entangled state. Int. J. Theor. Phys. 56, 1762–1770 (2017)
Xu, G.B.: Novel quantum proxy signature without entanglement. Int. J. Theor. Phys. 54(8), 2605–2612 (2015)
Boykin, P., Roy Chowdhury, V.: Optimal encryption of quantum bits. Phys. Rev. A 67, 042317 (2003)
Vernam, G.: Cipher printing telegraph systems for secret wire and radio telegraphic communication. Trans. A. I. E. E. XLV 295–301 (1926)
Zhao, Q.L., Li, X.Y.: A bargmann system and the involutive solutions associated with a new 4-order lattice hierarchy. Anal. Math. Phys. 6(3), 237–254 (2016)
Wang, Y.H.: Beyond regular semigroups. Semigroup Forum 92(2), 414–448 (2016)
Zhang, J.K., Wu, X.J., **ng, L.S., Zhang, C.: In Herbert bifurcation analysis of five-level cascaded H-bridge inverter using proportional-resonant plus time-delayed feedback. Int. J. Bifurcat. Chaos 26, 11 (2016)
Zhang, T.Q., Meng, X.Z., Zhang, T.H.: Global analysis for a delayed siv model with direct and environmental transmissions. J. Appl. Anal. Comput. 6(2), 479–491 (2016)
Meng, X.Z., Wang, L., Zhang, T.H.: Global dynamics analysis of a nonlinear impulsive stochastic chemostat system in a polluted environment. J. Appl. Anal. Comput. 6(3), 865–875 (2016)
Meng, X.Z., Zhao, S.N., Zhang, W.Y.: Adaptive dynamics analysis of a predator-prey model with selective disturbance. Appl. Math. Comput. 266, 946–958 (2015)
Zhao, W.C., Li, J., Meng, X.Z.: Dynamical analysis of SIR epidemic model with nonlinear pulse vaccination and lifelong immunity. Discrete Dyn. Nat. Soc. 2015, 848623 (2015)
Cui, Y.J., Zou, Y.M.: An existence and uniqueness theorem for a second order nonlinear system with coupled integral boundary value conditions. Appl. Math. Comput. 256, 438–444 (2015)
Yu, J., Li, M.Q., Wang, Y.L., He, G.P.: A decomposition method for large-scale box constrained optimization. Appl. Math. Comput. 231, 9–15 (2014)
Jiang, T.S., Jiang, Z.W., Ling, S.T.: An algebraic method for quaternion and complex least squares coneigen-problem in quantum mechanics. Appl. Math. Comput. 249, 222–228 (2014)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liang, XQ., Wu, YL., Zhang, YH. et al. Quantum Multi-proxy Blind Signature Scheme Based on Four-Qubit Cluster States. Int J Theor Phys 58, 31–39 (2019). https://doi.org/10.1007/s10773-018-3907-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-018-3907-z