Search
Search Results
-
Networking and cryptography library with a non-repudiation flavor for blockchain
Blockchain is currently one of the most widely discussed inventions in the information and communication technology industry. It is a pillar of the...

-
Freight tour synthesis based on entropy maximization with fuzzy logic constraints
This paper presents an improved entropy-based freight tour synthesis (FTS) using fuzzy logic (FL). One approach used in formulating FTS models is...
-
Evidence-Based Intervention (EBI) Map**: a systematic approach to understanding the components and logic of EBIs
BackgroundDespite the development of numerous evidence-based interventions (EBIs), many go unused in practice. Hesitations to use existing EBIs may...

-
Proving authentication property of PUF-based mutual authentication protocol based on logic of events
PUF (Physical unclonable function) is a new hardware security primitive, and the research on PUFs is one of the emerging research focuses. For...

-
SLAKA_CPS: Secured lightweight authentication and key agreement protocol for reliable communication among heterogenous devices in cyber-physical system framework
The rapid expansion of Cyber-Physical Systems (CPS) is crucial for enhancing connectivity in the smart world. Encompassing smart homes, cities,...

-
Can Non-classical Logic Treat Mathematics as Exceptional?
The paper criticizes a ‘lazy’ strategy popular amongst contemporary advocates of non-classical logic motivated by non-mathematical phenomena (e.g....
-
Where Policy and Culture Collide: Perceptions and Responses of Swidden Farmers to the Burn Ban in West Kalimantan, Indonesia
Catastrophic uncontrolled fires are a leading social-environmental challenge that now occur even in the humid tropics. In 2015 extensive Indonesian...

-
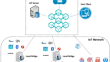
An authentication mechanism based on blockchain for IoT environment
The Internet of Things (IoT) is a network where physical objects with unique addresses can connect and communicate with each other through the...
-
Secure privacy-enhanced fast authentication and key management for IoMT-enabled smart healthcare systems
The smart healthcare system advancements have introduced the Internet of Things, enabling technologies to improve the quality of medical services....

-
Proxy signature-based role delegation scheme: formal analysis and simulation
In the security domain, wide variety of signature schemes are available for providing confidentiality, Integrity and non-repudiation. Proxy signature...

-
RETRACTED ARTICLE: Improved RFID mutual authentication protocol against exhaustive attack in the context of big data
The development of big data has epromoted the development of Internet technology, but it has brought more network security and privacy problems....

-
Secret sharing based RFID protocol using ECC for TMIS
With the moderate and constant advancement of the smart internet of things (IoT) and the propagation of 5 G correspondence innovation, the security...

-
A signcryption with identity-based authentication for secure EHR sharing in IoMT utilizing ECC
Due to real-time data sharing in the Internet of Medical Things (IoMT), the healthcare sector has evolved significantly in recent years. However,...

-
Anonymous and robust biometric authentication scheme for secure social IoT healthcare applications
In the era of rapid technological advancement, the Internet of Things (IoT) has revolutionised healthcare through systems like the Telecare Medicine...

-
Normalisation and subformula property for a system of intuitionistic logic with general introduction and elimination rules
This paper studies a formalisation of intuitionistic logic by Negri and von Plato which has general introduction and elimination rules. The...

-
Normalisation and subformula property for a system of classical logic with Tarski’s rule
This paper considers a formalisation of classical logic using general introduction rules and general elimination rules. It proposes a definition of...

-
Security, Disinformation and Harmful Narratives: RT and Sputnik News Coverage about Sweden
It is a well-known fact both among scholars of propaganda and disinformation, and among political leaders that Sputnik and RT are using their news...

-
Sentential Logic Languages ∑
The fourth chapter begins the construction of a series of named formal languages, beginning with a formal language for sentential logic. The logical...
-
Provable secure authentication key agreement for wireless body area networks
Wireless body area networks (WBANs) guarantee timely data processing and secure information preservation within the range of the wireless access...
-
A Lightweight Two-Factor Continuous Authentication Protocol for Agricultural IoT Devices
The rapid development of Internet of Things (IoT) technology has led to increased attention to its potential applications in agriculture. IoT-based...

