Search
Search Results
-
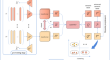
Deep contrastive multi-view clustering with doubly enhanced commonality
Recently, deep multi-view clustering leveraging autoencoders has garnered significant attention due to its ability to simultaneously enhance feature...
-
Sm-vsn-3c: a new Starlings model-based virtual sensor networks for coverage, connectivity, and data ccommunication
The study of continuous natural or industrial phenomena in time and space requires the emergence of new wireless sensor networks. A virtual sensor...

-
Quality evaluation methods of handwritten Chinese characters: a comprehensive survey
Quality evaluation of handwritten Chinese characters aims to automatically quantify and assess handwritten Chinese characters through computer vision...

-
Expediting the design and development of secure cloud-based mobile apps
The adoption and popularity of mobile devices by end-users is partially driven by the increasing development and availability of mobile applications...

-
PULSE: Proactive uncovering of latent severe anomalous events in IIoT using LSTM-RF model
In the IIoT, billions of devices continually provide information that is extremely diverse, variable, and large-scale and presents significant...

-
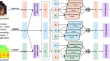
FEF-Net: feature enhanced fusion network with crossmodal attention for multimodal humor prediction
Humor segment prediction in video involves the comprehension and analysis of humor. Traditional humor prediction has been text-based; however, with...
-
Exploring behaviours of RESTful APIs in an industrial setting
A common way of exposing functionality in contemporary systems is by providing a Web-API based on the REST API architectural guidelines. To describe...

-
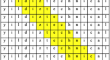
Exploring low-level statistical features of n-grams in phishing URLs: a comparative analysis with high-level features
Phishing attacks are the biggest cybersecurity threats in the digital world. Attackers exploit users by impersonating real, authentic websites to...
-
A comparative study of software defect binomial classification prediction models based on machine learning
As information technology continues to advance, software applications are becoming increasingly critical. However, the growing size and complexity of...

-
Integrated multi-view modeling for reliable machine learning-intensive software engineering
Development of machine learning (ML) systems differs from traditional approaches. The probabilistic nature of ML leads to a more experimentative...

-
Empowering e-learning approach by the use of federated edge computing
Federated learning (FL) is a decentralized approach to training machine learning model. In the traditional architecture, the training requires...

-
Efficient base station deployment in specialized regions with splitting particle swarm optimization algorithm
Signal coverage quality and intensity distribution in complex environments pose a critical challenge, particularly evident in high-density personnel...

-
A channel-gained single-model network with variable rate for multispectral image compression in UAV air-to-ground remote sensing
Unmanned aerial vehicle (UAV) air-to-ground remote sensing technology, has the advantages of long flight duration, real-time image transmission, wide...

-
Bridging distribution gaps: invariant pattern discovery for dynamic graph learning
Temporal graph networks (TGNs) have been proposed to facilitate learning on dynamic graphs which are composed of interaction events among nodes....

-
Metaheuristic algorithms and their applications in wireless sensor networks: review, open issues, and challenges
Metaheuristic algorithms have wide applicability, particularly in wireless sensor networks (WSNs), due to their superior skill in solving and...

-
Service selection based on blockchain smart contracts in cloud-edge environment
The rapid integration of cloud computing and edge computing has brought the cloud-edge environment into the spotlight in information technology....

-
Blockchain enabled secure pharmaceutical supply chain framework with traceability: an efficient searchable pharmachain approach
The complex networks of manufacturers, suppliers, retailers, and customers that make up today’s pharmaceutical supply chain span worldwide. As it is,...

-
An anonymous authentication with blockchain assisted ring-based homomorphic encryption for enhancing security in cloud computing
Nowadays, the need for cloud computing has increased due to the exponential growth in information transmission. Cybercriminals are persistent in...

-
Multi-party codebook distribution strategy based on secret sharing
The paper addresses the issue of secure distribution of codebooks in the field of information security, particularly in the domain of covert...

