Search
Search Results
-

-
Combinatorial constructions of optimal low-power error-correcting cooling codes
High temperatures have dramatic negative effects on interconnect performance. In a bus, whenever the state transitions from “0” to “1”, or “0” to...
-
Construction of quantum codes from multivariate polynomial rings
In this paper, we use multivariate polynomial rings to construct quantum error-correcting codes (QECCs) via Hermitian construction. We establish a...
-
Optimal binary signed-digit representations of integers and the Stern polynomial
The binary signed-digit (BSD) representation of integers is used for efficient integer computation in various settings. The Stern polynomial is a...

-
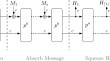
Preimage attacks on reduced-round Ascon-Xof
Ascon , a family of algorithms that supports authenticated encryption and hashing, has been selected as the new standard for lightweight cryptography...
-
Classifying pseudo-ovals, translation generalized quadrangles, and elation Laguerre planes of small order
We provide classification results for translation generalized quadrangles of order less than or equal to 64, and hence, for all incidence geometries...
-
Efficient secure multi-party computation for proof of custody in Ethereum sharding
Ethereum, one of the most prominent and widely deployed blockchain systems, is undergoing a significant upgrade that adopts sharding for capacity...

-
PERK: compact signature scheme based on a new variant of the permuted kernel problem
In this work we introduce PERK a compact digital signature scheme based on the hardness of a new variant of the permuted kernel problem (PKP). PERK...

-
CCA security for contracting (quasi-)Feistel constructions with tight round complexity
Feistel constructions using contracting round functions were introduced in 1990s and generalized by Yun et al. (Des Codes Cryptogr 58(1):45–72, 2011)...

-
Negacyclic BCH codes of length \(\frac{q^{2m}-1}{q+1}\) and their duals
Negacyclic BCH codes are an important subclass of negacyclic codes and have good parameters. Inspired by the recent work on cyclic codes published in...
-
On Bose distance of a class of BCH codes with two types of designed distances
BCH codes are an interesting class of cyclic codes with good error-correcting capability and have wide applications in communication and storage...
-
Balanced reconstruction codes for single edits
Motivated by the sequence reconstruction problem initiated by Levenshtein, reconstruction codes were introduced by Cai et al. to combat errors when a...
-
Impossibility of efficient information-theoretic fuzzy extraction
Fuzzy extractors convert noisy signals from the physical world into reliable cryptographic keys. Fuzzy min-entropy measures the limit of the length...

-
Efficient computation of \((2^n,2^n)\)-isogenies
Elliptic curves are abelian varieties of dimension one; the two-dimensional analogues are abelian surfaces. In this work we present an algorithm to...

-

-
Square root computation in finite fields
In this paper, we present a review of three widely-used practical square root algorithms. We then describe a unifying framework where each of these...

