Search
Search Results
-
External codes for multiple unicast networks via interference alignment
We introduce a formal framework to study the multiple unicast problem for a coded network in which the network code is linear over a finite field and...

-
On prefer-one sequences
We study the sequences generated by prefer-one rule with different initial vectors. Firstly, we give upper bounds of their periods and for initial...

-
On the classification of skew Hadamard matrices of order \(\varvec{36}\) and related structures
Two skew Hadamard matrices are considered
SH -equivalent if they are similar by a signed permutation matrix. This paper determines the number ofSH -ine... -
Indicator functions, v-numbers and Gorenstein rings in the theory of projective Reed–Muller-type codes
For projective Reed–Muller-type codes we give a global duality criterion in terms of the v-number and the Hilbert function of a vanishing ideal. As...

-

-
ZLR: a fast online authenticated encryption scheme achieving full security
Online authenticated encryption has been considered of practical relevance in light-weight environments due to low latency and constant memory usage....

-
Constructions of t-strongly multimedia IPP codes with length \(t+1\)
Strongly multimedia identifiable parent property code ( t -SMIPPC) was introduced for protecting multimedia contents from illegally redistributing...
-
Some new constructions of optimal linear codes and alphabet-optimal \((r,\delta )\)-locally repairable codes
In distributed storage systems, an r -Locally Repairable Code ( r -LRC) ensures that a failed symbol can be recovered by accessing at most r other...
-
Structure of CSS and CSS-T quantum codes
We investigate CSS and CSS-T quantum error-correcting codes from the point of view of their existence, rarity, and performance. We give a lower bound...
-
Bounds on data limits for all-to-all comparison from combinatorial designs
In situations where every item in a data set must be compared with every other item in the set, it may be desirable to store the data across a number...
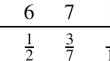
-
Efficient quantum algorithms for some instances of the semidirect discrete logarithm problem
The semidirect discrete logarithm problem (SDLP) is the following analogue of the standard discrete logarithm problem in the semidirect product...
-
On duplication-free codes for disjoint or equal-length errors
Motivated by applications in DNA storage, we study a setting in which strings are affected by tandem-duplication errors. In particular, we look at...

-

-
LCD codes and almost optimally extendable codes from self-orthogonal codes
LCD codes and (almost) optimally extendable codes can be used to safeguard against fault injection attacks (FIA) and side-channel attacks (SCA) in...
-
On optimal constant weight codes derived from \(\omega \)-circulant balanced generalized weighing matrices
Balanced generalized weight matrices are used to construct optimal constant weight codes that are monomially inequivalent to codes derived from the...
-

-
Yoyo attack on 4-round Lai-Massey scheme with secret round functions
In this study, we present the first yoyo attack to recover the secret round function of the 4-round Lai-Massey scheme with an affine orthomorphism....

