Search
Search Results
-
Explicit constructions of NMDS self-dual codes
Near maximum distance separable (NMDS) codes are important in finite geometry and coding theory. Self-dual codes are closely related to...
-
M2AST:MLP-mixer-based adaptive spatial-temporal graph learning for human motion prediction
Human motion prediction is a challenging task in human-centric computer vision, involving forecasting future poses based on historical sequences....

-
Global adaptive histogram feature network for automatic segmentation of infection regions in CT images
Accurate and timely diagnosis of COVID-like virus is of paramount importance for lifesaving. In this work, deep learning techniques are applied to...

-
Smart contract vulnerabilities detection with bidirectional encoder representations from transformers and control flow graph
Up to now, the smart contract vulnerabilities detection methods based on sequence modal data and sequence models have been the most commonly used....

-

-
Survey-based analysis of cybersecurity awareness of Turkish seafarers
In recent years, vessels have become increasingly digitized, reflecting broader societal trends. As a result, maritime operations have become an...

-
Impact of linkage level on inferences from big data analyses in health and medical research: an empirical study
BackgroundLinkage errors that occur according to linkage levels can adversely affect the accuracy and reliability of analysis results. This study...

-
Improve the efficiency and accuracy of ophthalmologists’ clinical decision-making based on AI technology
BackgroundAs global aging intensifies, the prevalence of ocular fundus diseases continues to rise. In China, the tense doctor-patient ratio poses...

-
Adaptive context-aware access control for IoT environments leveraging fog computing
The increasing use of the Internet of Things (IoT) has driven the demand for enhanced and robust access control methods to protect resources from...

-
Digital Sustainability for Energy-Efficient Behaviours: A User Representation and Touchpoint Model
In response to climate change, nations have been tasked with reducing energy consumption and lessening their carbon footprint through targeted...

-
Using the ACE framework to enforce access and usage control with notifications of revoked access rights
The standard ACE framework provides authentication and authorization mechanisms similar to those of the standard OAuth 2.0 framework, but it is...

-
A three-stage quality evaluation method for experience products: taking animation as an example
The diversity and dynamics of quality index information bring challenges to quality assessment of experience products. This paper proposes a...

-
Virtual Experiences, Real Memories? A Study on Information Recall and Recognition in the Metaverse
There are high expectations towards extended reality (XR), namely the “metaverse”. However, human performance in the metaverse has been called into...

-
Optimization of vision transformer-based detection of lung diseases from chest X-ray images
BackgroundRecent advances in Vision Transformer (ViT)-based deep learning have significantly improved the accuracy of lung disease prediction from...

-
A Taxonomy of Home Automation: Expert Perspectives on the Future of Smarter Homes
Recent advancements in digital technologies, including artificial intelligence (AI), Internet of Things (IoT), and information and communication...

-
Automating shareable cyber threat intelligence production for closed source software vulnerabilities: a deep learning based detection system
Software can be vulnerable to various types of interference. The production of cyber threat intelligence for closed source software requires...

-
Accurate entropy modeling in learned image compression with joint enchanced SwinT and CNN
Recently, learned image compression (LIC) has shown significant research potential. Most existing LIC methods are CNN-based or transformer-based or...

-
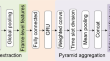
A multi-scale no-reference video quality assessment method based on transformer
Video quality assessment is essential for optimizing user experience, enhancing network efficiency, supporting video production and editing,...
-
ViCLEVR: a visual reasoning dataset and hybrid multimodal fusion model for visual question answering in Vietnamese
In recent years, visual question answering (VQA) has gained significant attention for its diverse applications, including intelligent car assistance,...

