Search
Search Results
-
Analysis and Architecture of Clinical Workflow Systems using Agent-Oriented Lifecycle Models
Healthcare executives are grappling with a climate of great change in the healthcare industry. This is coming from a number of sources. First, there...
-
Current Status of Computerized Decision Support Systems in Mammography
Breast cancer is one of the most devastating and deadly diseases for women today. Despite advances in cancer treatment, early mammographic detection...
-
Computerization of Clinical Guidelines: an Application of Medical Document Processing
Clinical Guidelines are being developed as a tool to promote Best Practice in Medicine. They are usually defined as “systematically developed...
-
Case-based Medical Informatics
The “applied” nature distinguishes applied sciences from theoretical sciences. To emphasize this distinction, we begin with a general, meta-level...
-
Medical Diagnosis and Prognosis Based on the DNA Microarray Technology
Immense genomic data have been accumulated through various research activities such as the Human Genome Project. A genome is the entire collection of...
-
Wearable Devices in Healthcare
The miniaturization of electrical and electronic equipment is certainly not a new phenomenon, and its effects have long been evident in the...
-
Evidence Based Telemedicine
This chapter focuses on evidence based telemedicine and its various applications. Evidence based medicine is the integration of best research...
-
Virtual Communities in Health Care
A virtual community is a social entity involving several individuals who relate to one another by the use of a specific communication technology that...
-
Simultaneous grading diagnosis of liver fibrosis, inflammation, and steatosis using multimodal quantitative ultrasound and artificial intelligence framework
Noninvasive, accurate, and simultaneous grading of liver fibrosis, inflammation, and steatosis is valuable for reversing the progression and...

-
Threshold ring signature: generic construction and logarithmic size instantiation
A ring signature is a variant of normal digital signature and protects the privacy of a specific signer in the sense that a ring signature can be...

-
Why the use of domain-specific modeling in airworthy software requires new methods and how these might look like? (extended version)
The use of domain-specific modeling (DSM) in safety-critical avionics is rare, even though the ever-increasing complexity of avionics systems makes...

-
Detecting mistakes in a domain model: a comparison of three approaches
Domain models are a fundamental part of software engineering, thus it is important for every software engineer to know the principles of domain...

-
ConKeD: multiview contrastive descriptor learning for keypoint-based retinal image registration
AbstractRetinal image registration is of utmost importance due to its wide applications in medical practice. In this context, we propose ConKeD, a...

-
Enhanced deep leaning model for detection and grading of lumbar disc herniation from MRI
Lumbar disc herniation is one of the most prevalent orthopedic issues in clinical practice. The lumbar spine is a crucial joint for movement and...

-
FedSHE: privacy preserving and efficient federated learning with adaptive segmented CKKS homomorphic encryption
Unprotected gradient exchange in federated learning (FL) systems may lead to gradient leakage-related attacks. CKKS is a promising approximate...

-
Qualitative reasoning and cyber-physical systems: abstraction, modeling, and optimized simulation
Complex systems modeling and simulation are critical in many industrial and research fields, specifically to predict, prove, verify, and understand...

-
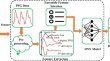
DNN-BP: a novel framework for cuffless blood pressure measurement from optimal PPG features using deep learning model
AbstractContinuous blood pressure (BP) provides essential information for monitoring one’s health condition. However, BP is currently monitored using...
-
A privacy-preserving image retrieval scheme with access control based on searchable encryption in media cloud
With the popularity of the media cloud computing industry, individuals and organizations outsource image computation and storage to the media cloud...

-
Improved homomorphic evaluation for hash function based on TFHE
Homomorphic evaluation of hash functions offers a solution to the challenge of data integrity authentication in the context of homomorphic...

-
A method for visualizing urban road events using distributed acoustic sensing
This study presents the construction of an urban underground sensing system using distributed acoustic sensing (DAS) technology, which utilizes the...

