Search
Search Results
-
Federated learning for digital healthcare: concepts, applications, frameworks, and challenges
Various hospitals have adopted digital technologies in the healthcare sector for various healthcare-related applications. Due to the effect of the...

-
A deep learning based cognitive model to probe the relation between psychophysics and electrophysiology of flicker stimulus
The flicker stimulus is a visual stimulus of intermittent illumination. A flicker stimulus can appear flickering or steady to a human subject,...

-
Understanding the GDPR from a requirements engineering perspective—a systematic map** study on regulatory data protection requirements
Data protection compliance is critical from a requirements engineering (RE) perspective, both from a software development lifecycle (SDLC)...

-
Evaluative Item-Contrastive Explanations in Rankings
The remarkable success of Artificial Intelligence in advancing automated decision-making is evident both in academia and industry. Within the...

-
A new integrated steganography scheme for quantum color images
In this paper, we propose a quantum steganography scheme with a color image as the cover image. In order to enhance the security of the embedded...

-
Why the use of domain-specific modeling in airworthy software requires new methods and how these might look like? (extended version)
The use of domain-specific modeling (DSM) in safety-critical avionics is rare, even though the ever-increasing complexity of avionics systems makes...

-
Exploring recent advances in random grid visual cryptography algorithms
Visual cryptography scheme is initiated to securely encode a secret image into multiple shares. The secret can be reconstructed by overlaying the...

-
Improving Likert scale big data analysis in psychometric health economics: reliability of the new compositional data approach
Bipolar psychometric scales data are widely used in psychologic healthcare. Adequate psychological profiling benefits patients and saves time and...

-
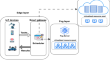
Cost-aware workflow offloading in edge-cloud computing using a genetic algorithm
The edge-cloud computing continuum effectively uses fog and cloud servers to meet the quality of service (QoS) requirements of tasks when edge...
-
Signal processing implementation of low-cost target speed detection of CW radar using FPGA
The low-cost Continuous Wave (CW) radar architecture for object speed detection is presented in this research. An FPGA (Field-Programmable Gate...

-
A robust method for malware analysis using stacking classifiers and dendrogram visualization
Malware analysis is a vital and challenging task in the ever-changing cyber threat landscape. Traditional signature-based methods cannot keep up with...

-
An adaptive service deployment algorithm for cloud-edge collaborative system based on speedup weights
In the contemporary landscape of edge computing, the deployment of services with stringent real-time requirements on edge devices is increasingly...

-
iDOCEM
In the business process lifecycle, models can be approached from two perspectives: on the one hand, models are used to create systems in the design...

-
Exploring the potential of Wav2vec 2.0 for speech emotion recognition using classifier combination and attention-based feature fusion
AbstractSelf-supervised learning models, such as Wav2vec 2.0, extract efficient features for speech processing applications including speech emotion...

-
Electromagnetic properties of coal using microstrip and an algorithm based on the Nicolson-Ross-Weir method
The work implements an experimental methodology to find the dielectric parameters: electrical permittivity, effective permittivity, magnetic...

-
Aggregating the response in time series lag models using quad weight kernel: impact of environmental factors on schizophrenia admissions
There has been a growing apprehension in the past few years concerning the issue of pollution and climate change. Several articles have shown the...

-
Cost-effective clonal selection and AIS-based load balancing in cloud computing environment
Cloud computing faces challenges in increasing efficiency through task scheduling and load balancing. Various load-balancing methods, including the...

-
Requirements for modelling tools for teaching
Modelling is an important activity in software development and it is essential that students learn the relevant skills. Modelling relies on dedicated...

-
Multidimensional graph transformer networks for trajectory prediction in urban road intersections
With the rapid development of autonomous driving, accurately predicting the future movement trajectories of various agents in complex scenarios, such...

-
Exploiting recurrent graph neural networks for suffix prediction in predictive monitoring
Predictive monitoring is a subfield of process mining that aims to predict how a running case will unfold in the future. One of its main challenges...

