Search
Search Results
-
Anticipative and Non-anticipative Controller Design for Network Control Systems
We propose a numerical procedure to design a linear output-feedback controller for a remote linear plant in which the loop is closed through a...
-
Q-Learning Based Load Balancing in Heterogeneous Networks with Human and Machine Type Communication Co-existence
A heterogeneous network, also known as a HetNet, is a network made up of numerous distinct wireless network nodes placed throughout the cellular...

-
Path Planning of Mobile Robots Under Uncertain Navigation Environments Using FCM Clustering ANFIS
In this paper an improved multiple adaptive neuro-fuzzy inference system (MANFIS) to solve the wheeled mobile robots path planning in unstructured...
-
A Pragmatic Review of QoS Optimisations in IoT Driven Networks
With advent of Internet of Things (IoT) an exponential growth has been observed in recent times towards the use of fifth generation (5G) network to...

-
Adaptive context-aware access control for IoT environments leveraging fog computing
The increasing use of the Internet of Things (IoT) has driven the demand for enhanced and robust access control methods to protect resources from...

-
English listening and speaking ability improvement strategy from Artificial Intelligence wireless network
With the rapid development of science and technology, there are many derivatives of Artificial Intelligence (AI) technology based on wireless...
-
Using the ACE framework to enforce access and usage control with notifications of revoked access rights
The standard ACE framework provides authentication and authorization mechanisms similar to those of the standard OAuth 2.0 framework, but it is...

-
UWB Wireless Positioning Method Based on LightGBM
In the ultra-wideband indoor positioning sceneraio, the non-line of sight (NLOS) propagation may be caused by obstacles, which may lead to the...

-
Research on Power Control Routing Algorithm for Wireless Sensor Networks Based on Ant Colony Optimization
Improving node energy consumption efficiency to increase network survival time is one of the main research priorities in wireless sensor networks...

-
TDOA and FDOA Hybrid Positioning of Mobile Radiation Source with Receiver Position Errors
High-precision position awareness is essential to ubiquitous wireless networks, which can provide real-time position information and abundant status...

-
Experimental Investigation on Insulation Performance of SO2/CO2 Gas Mixtures
In an effort to replace the use of SF 6 gas in high-voltage equipment, research has been conducted on more environmentally favorable alternative gases...

-
End-to-End No-wait Scheduling for Time-Triggered Streams in Mixed Wired-Wireless Networks
Proprietary communication technologies for time-critical communication in industrial environments are being gradually replaced by Time-sensitive...

-
JAYA NL-WSN: Jaya Algorithm for Node Localization Issue in Wireless Sensor Network
The process of discovering the location of occurring event is critical task in wireless sensor network but it is foremost necessity of various...

-
Performance Analysis of NR 5G Cellular Vehicle to Everything Communication in Mode 3
In the future, intelligent transportation systems will rely heavily on vehicle to vehicle (V2V) communication-based cooperative vehicular networks...

-
DenseNet-121 Model for Diagnosis of COVID-19 Using Nearest Neighbour Interpolation and Adam Optimizer
The pandemic of COVID-19 has caused disaster all over the world since its outbreak. It is a disease which affects the respiratory system of patient...

-
Verifiable Changeable Threshold Secret Image Sharing Scheme Based on LWE Problem
In common threshold secret image sharing (t, n) schemes, each of n shareholders has a share of secret image S. By having at least t shares, the...

-
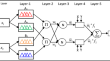
IAFPN: interlayer enhancement and multilayer fusion network for object detection
Feature pyramid network (FPN) improves object detection performance by means of top-down multilevel feature fusion. However, the current FPN-based...

-
Automating shareable cyber threat intelligence production for closed source software vulnerabilities: a deep learning based detection system
Software can be vulnerable to various types of interference. The production of cyber threat intelligence for closed source software requires...

-
Investigation of the Seasonal Impact of Diversity Gain and Improvement Factors on Signal Availability in Tropical Location
A satellite communication signal suffers from attenuation due to rain, and this offers many problems for effective signal transfer and quality,...

-
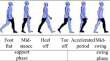
Research on the Gait Phase Analysis Method of Femoral Amputation Patients Based on the Thin Film Pressure Sensor
The running-in of amputees and prostheses usually requires a long time. Many objective evaluation parameters must be obtained to fit prosthetic...