Search
Search Results
-
Detection of vulnerabilities in blockchain smart contracts using deep learning
Blockchain helps to give a sense of security as there is only one history of transactions visible to all the involved parties. Smart contracts enable...

-
A Survey of Security Vulnerabilities and Detection Methods for Smart Contracts
At present, smart contracts cannot guarantee absolute security, and they have exposed many security issues and caused incalculable losses. Due to the...
-
Adobe Photoshop Vulnerabilities
The impact of rapidly changing technology is now majorly contributing to the risk of upcoming new challenges. The advancements of computers can’t be...
-
A Study on Networked Industrial Robots in Smart Manufacturing: Vulnerabilities, Data Integrity Attacks and Countermeasures
The recent integration and collaboration of robots with networks expose new challenges and problems in terms of security. However, to the best of our...
-
A CNN-based automatic vulnerability detection
With the advent of the Internet, the activities of individuals and businesses have expanded into the online realm. As a result, vulnerabilities that...

-
WNV-Detector: automated and scalable detection of wireless network vulnerabilities
The security of wireless routers receives much attention given by the increasing security threats. In the era of Internet of Things, many devices...

-
Security Issues and Vulnerabilities in Web Application
Role of web security has become an important topic as web and web application became quite demanding and people started using them every day. Last...
-
Security Vulnerabilities in Facebook Data Breach
This research explores the intricate landscape of data breaches within Facebook (now Meta) from 2018 to 2021. The goal of this case study is to...
-
An optimization technique for intrusion detection of industrial control network vulnerabilities based on BP neural network
The aim of this research is to solve the problem that the intrusion detection model of industrial control system has low detection rate and detection...

-
Prediction of Software Vulnerabilities Using Random Forest Regressor
The launch of new software technologies with new features helps the developer in software development but it can be prone to vulnerabilities....
-
Application of ISM in Evaluating Inter-relationships Among Software Vulnerabilities
Complicated digital communication networks generate faults in development, implementation and governance, which are the main cause of software...
-
A Comparative Study of Vulnerabilities Scanners for Web Applications: Nexpose vs Acunetix
As known, everyone uses web applications to make purchases, transfer funds, upload data, etc. Meanwhile, the security of these web applications has...
-
Visual Studio Vulnerabilities and Its Secure Software Development
The rapid advances in technology are bringing about a new set of difficulties in the form of vulnerabilities and their exploitation by attackers to...
-
Cybersecurity for Industrial IoT, Threats, Vulnerabilities, and Solutions: A Brief Review
The Industrial Internet of Things (IIoT) refers to use connected devices and technology in industrial settings such as manufacturing, energy, and...
-
APT Attack Detection Based on Graph Convolutional Neural Networks
Advanced persistent threat (APT) attacks are malicious and targeted forms of cyberattacks that pose significant challenges to the information...

-
A Scalable Middleware for IoT Vulnerability Detection
Cyberattacks targeting vulnerabilities in the internet of things (IoT) devices are increasing in number annually. Accordingly, various methods and...
-
A Novel Smart Contract Reentrancy Vulnerability Detection Model based on BiGAS
With the development of blockchain technology, smart contracts have attracted a lot of attention in recent years. They are widely used because they...

-
CFG Analysis for Detecting Vulnerabilities in Smart Contracts
Smart contracts are a leading light moment in blockchain technology 2.0 and are universally used in various applications. A smart contract is a...
-
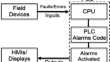
Applied methods to detect and prevent vulnerabilities within PLC alarms code
AbstractAdversaries may target alerting alarms raised by PLCs (Programmable Logic Controllers) to prevent notifying operators of critical conditions,...
-
A Comparative Study of Novelty Detection Models for Zero Day Intrusion Detection in Industrial Internet of Things
The detection of zero-day attacks in the IoT network is a challenging task due to unknown security vulnerabilities. Also, the unavailability of the...
