Search
Search Results
-
A Pseudonym Changing Strategy for Dynamic Grou** in VANETs
For complex VANETs and highly dynamic vehicles, vehicle location privacy becomes increasingly important. Pseudonyms are commonly used in VANETs to...
-
An Anonymous Authentication Scheme Based on Self-generated Pseudonym for VANETs
With the maturity of mobile communication and Internet of Things, the extensive deployment of Vehicular Ad-hoc Networks (VANETs) and the popularity...
-
Pseudonym Changing Strategy with Mix Zones Based Authentication Protocol for Location Privacy in Road Networks
A great advancement has been made in intelligent transportation system and communication technologies in order to exchange secure information between...

-
Combination of Pseudonym Changing with Blockchain-Based Data Credibility for Verifying Accuracy of Latest Vehicle Information in VANETs
With the rapid development of the automobile industry, the security of vehicle communication networks and the authenticity of messages have been...
-
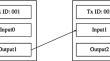
Blockchain-Based Privacy-Aware Pseudonym Management Framework for Vehicular Networks
Vehicular networks rely on public key infrastructure (PKI) to generate the long-term and short-term (pseudonyms) certified pair of keys. This allows...
-
Pseudonym Schemes Based on Location Privacy Protection in VANETs: A Survey
In vehicle ad-hoc networks (VANETs), the location privacy of vehicles is a major security issue. In recent years, a large amount of pseudonym-based...
-
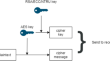
Cryptography-based location privacy protection in the Internet of Vehicles
The evolution of the Internet of Things paradigm in recent years demonstrate a significant impact on the transportation sector, leading to the...
-
An anonymous and secure key agreement protocol for NFC applications using pseudonym
Near Field Communication (NFC) is a promising technology that facilitate E-commerce through contactless communications. In the past decade, the NFC...

-
Privacy-preserving aggregate signcryption scheme with allowing dynamic updating of pseudonyms for fog-based smart grids
Fog-based smart grids have been a hit research field in recent years, providing low latency, location-sensitive and latency-aware local data...
-
An effective variant ring signature-based pseudonym changing mechanism for privacy preservation in mixed zones of vehicular networks
The privacy information related to the location of the vehicles need to be concealed with utmost care in the vehicular network since its disclosure...

-
Cryptanalysis of Near Field Communication Based Authentication Protocol for Mobile Payment System
Near field communication (NFC) is one of the utmost pullulating technology in the lea of pervasive computing. In the domain of mobile commerce,...

-
Blockchain-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks
Security and privacy are two challenging issues in Vehicular Ad-hoc Networks (VANETs), which have attracted widespread concern from industry and...

-
A conditional privacy-preserving fair electronic payment scheme based on blockchain without trusted third party
There is an increasing demand for the security of electronic payment systems. The importance of characteristics such as preventing double-spending,...

-
A location privacy protection scheme for convoy driving in autonomous driving era
Convoy driving has great potential in the development of autonomous driving industry, which can bring great improvement to the utilization rate of...

-
A Chebyshev polynomial-based conditional privacy-preserving authentication and group-key agreement scheme for VANET
Vehicle ad hoc network (VANET) is an open communication environment. Any user can broadcast messages, which means that it can be easily attacked by...

-
Secure and efficient authentication protocol with user untraceability for global roaming services
In case of global roaming services, user authentication plays an important role in order to prevent any unauthorized user from accessing services....

-
A novel trust management method to preserve privacy in vehicular ad-hoc networks
Vehicular ad-hoc network is one of the networks based on wireless sensor networks which, nowadays, plays a crucial role in life. Due to the autonomy...

-
An Efficient Privacy-Preserving Authentication Scheme Based on Shamir Secret Sharing for VANETs
As the technology of mobile communication and Internet of Things by leaps and bounds, Vehicular Ad-hoc Networks (VANETs), a new type of intelligent...
-
A Blockchain enabled location-privacy preserving scheme for vehicular ad-hoc networks
n the imminent future, with the immense need for improving road safety and demand for enhancing the overall driving experience, the utility of...

-
Desynchronization resistant privacy preserving user authentication protocol for location based services
Preserving user privacy and authenticity are essential requirements for location based services in order to protect user’s confidential information...

