Search
Search Results
-
Location Entropy-Based Privacy Protection Algorithm for Social Internet of Vehicles
In the Social Internet of Vehicles (SIoV), sharing data among entities is prone to leaking private data. Protecting vehicle users privacy through...

-
Snowflake Anonymous Network Traffic Identification
Tor, as a widely used anonymous communication system, is frequently employed by some users for illegal activities. Snowflake server as a plugin that...
-
On the entropy inequality and its exploitation in continuum physics
The paper deals with the statement and the application of the entropy principle, through the Clausius–Duhem inequality, in continuum physics. The...
-
LGAAFS: A lightweight group anonymous mutual authentication and forward security scheme for wireless body area networks
Wireless Body Area Network (WBAN) plays an important role in the modern telemedicine environment. In WBAN, intelligent and resource-limited sensors...

-
Experimental Study on the Entropy Change Failure Precursors of Marble under Different Stress Paths
In this paper, the indoor loading and unloading tests and acoustic emission (AE) monitoring tests of marble under different stress paths are carried...
-
Fault diagnosis of rotating machines based on modified hierarchical fluctuation dispersion entropy and multi-cluster feature selection
The vibration signal of rotating mechanical equipment contains a large amount of information that can be used for the fault diagnosis of rotating...
-
An anonymous mutual authentication and key agreement scheme in WMSN using physiological data
Wireless medical sensor network (WMSN) is an application of the Internet of Things (IoT) that plays a very important role in today’s era for the...

-
Uncertainty quantification in mechanistic epidemic models via cross-entropy approximate Bayesian computation
This paper proposes a data-driven approximate Bayesian computation framework for parameter estimation and uncertainty quantification of epidemic...

-
Secure and lightweight authentication protocol for anonymous data access in cloud assisted IoT system
Rapid evolution of IoT technologies has virtually made connectivity of all the real world objects to the internet possible with the help of tiny...

-
Anonymous Author Identifier Using Machine Learning
Jesmin, Sabrina Damineni, RahulCyber security companies predict potential attacks on their clients by monitoring deep and dark web forums where...
-
Assessment of Attribution in Cyber Deterrence: A Fuzzy Entropy Approach
Against the threat of cyber warfare and cyber-attacks involving cyber kinetics by state and non-state elements traditionally various and the kind of...
-
An anonymous entropy-based location privacy protection scheme in mobile social networks
The popularization of mobile communication devices and location technology has spurred the increasing demand for location-based services (LBSs)....

-
LAPTAS: lightweight anonymous privacy-preserving three-factor authentication scheme for WSN-based IIoT
Nowadays, wireless sensor networks (WSNs) are essential for monitoring and data collection in many industrial environments. Industrial environments...

-
Software-Defined Networking Security System Using Machine Learning Algorithms and Entropy-Based Features
Software-defined networking (SDN) is an exceptional technology among the recent trends in IT. The static quality of the classical network...
-
RAIAP: renewable authentication on isolated anonymous profiles
Implementing pseudonymity, key-management, non-repudiation and data minimisation features in isolated procedures is trivial. However, integrating all...
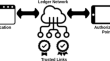
-
K-Anonymity-Based Privacy-Preserving and Efficient Location-Based Services for Internet of Vehicles Withstand Viterbi Attack
With the population of Internet of Vehicles (IoV), location-based services (LBSs) for vehicles have drawn great attention. Meanwhile, users’ location...
-
A secure three-factor anonymous roaming authentication protocol using ECC for space information networks
Nowadays, space information networks (SIN) has been widely used in navigation, observation and military activities due to its advantages of wide...

-
Intelligent Privacy Protection of End User in Long Distance Education
Long distance education is an important part during the COVID-19 age. An intelligent privacy protection with higher effect for the end users is an...

-
Design of Robust Smartcard-Based User Anonymous Authentication Protocol with AVISPA Simulation
Recently, Byun presented a privacy maintaining smartcard-based authentication protocol with provable security. We analyze and identify that his...
-
Multi-Parallel Adaptive Grasshopper Optimization Technique for Detecting Anonymous Attacks in Wireless Networks
For a number of years, due to exponential increase in the demand for sustainable environment, suspicious activities have recently been identified as...

