Search
Search Results
-
SCL-SKG: software knowledge extraction with span-level contrastive learning
The text of software knowledge community contains abundant knowledge of software engineering field. The software knowledge entity and relation can be...

-
SV2-SQL: a text-to-SQL transformation mechanism based on BERT models for slot filling, value extraction, and verification
Information retrieval from databases is challenging for a non-SQL-domain expert. Some previous studies have provided solutions for translating the...

-
Enhanced kinship verification analysis based on color and texture handcrafted techniques
Nowadays, kinship verification is an attractive research area within computer vision. It significantly affects applications in the real world, such...

-
A multi-dimensional review on handwritten signature verification: strengths and gaps
A handwritten signature is the most widely accepted method to authenticate an individual in banking, financial, business transactions, cheque...

-
Knowledge Graph of Urban Firefighting with Rule-Based Entity Extraction
There is little research on entity extraction in constructing the knowledge graphs for urban firefighting. In this paper, we propose a rule-based...
-
Enhanced user verification in IoT applications: a fusion-based multimodal cancelable biometric system with ECG and PPG signals
The core premise of cancelable biometrics lies in the creation of a distinct biometric template for every individual, which can be either canceled or...

-
Embedding and extraction of knowledge in tree ensemble classifiers
The embedding and extraction of knowledge is a recent trend in machine learning applications, e.g., to supplement training datasets that are small....

-
A review on kinship verification from facial information
AbstractKinship verification is a challenging computer vision task that aims to mainly answer the question: “Are these two persons blood relatives?”....

-
Knowledge Sources
Knowledge sources are essential components of many NLP tasks, such as question answering (Chen et al., Reading wikipedia to answer open-domain...
-
The multiple relationships among knowledge heterogeneity, knowledge transfer and knowledge innovation as moderated by microstructure holes
The positive relationship between knowledge transfer and knowledge innovation is recognized by most scholars, while knowledge heterogeneity, as a...

-
A survey of safety and trustworthiness of large language models through the lens of verification and validation
Large language models (LLMs) have exploded a new heatwave of AI for their ability to engage end-users in human-level conversations with detailed and...

-
Enhanced Named Entity Recognition algorithm for financial document verification
Many enterprise systems are document-intensive and require extensive manual verification. The verification process has challenge in terms of time and...

-
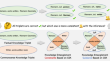
CoolGust: knowledge representation learning with commonsense knowledge guidelines and constraints
Representation learning serves as a crucial link between knowledge graphs and neural models. Knowledge graphs are typical symbolic models and require...
-
Multi-dilation Convolutional Neural Network for Automatic Handwritten Signature Verification
With the recent advancements in deep learning techniques, the application areas of unstructured data analytics are emerging in multiple domains. One...

-
Synews: a synergy-based rumor verification system
Online social networks (OSNs) are now implied as an important source of news and information besides establishing social connections. However, such...

-
Stationary wavelet transform features for kinship verification in childhood images
Estimating blood relationships from facial images is a complex task in computer vision due to subtle differences. Existing models are facing...

-
Real-time face verification on mobile devices using margin distillation
Face verification is an attractive yet challenging research area in computer vision. To make an improvement in the existing models for face...

-
Multi-scripted Writer Independent Off-line Signature Verification using Convolutional Neural Network
Signature is a biometrics trait widely used for personal verification in financial and most other organizations where financial and relevant types of...

-
Attendance Monitoring System Using Facial and Geo-Location Verification
Face verification is the most distinctive method used in the most effective image processing software, and it is essential in the technical world....
-
Tooling and Knowledge Deployment
We introduce example tooling to support the knowledge graph life cycle presented in the previous chapters in Part III. Additionally, we explain...
