Search
Search Results
-
Towards graph-anonymization of software analytics data: empirical study on JIT defect prediction
As the usage of software analytics for understanding different organizational practices becomes prevalent, it is important that data for these...

-
Semantic-aware deidentification generative adversarial networks for identity anonymization
Privacy protection in the computer vision field has attracted increasing attention. Generative adversarial network-based methods have been explored...

-
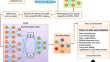
A novel Jarratt butterfly Ebola optimization-based attentional random forest for data anonymization in cloud environment
Privacy and security are the most essential barriers preventing widespread public cloud adaptation. The data that is distributed within the cloud...
-
Experiments and Analyses of Anonymization Mechanisms for Trajectory Data Publishing
With the advancing of location-detection technologies and the increasing popularity of mobile phones and other location-aware devices, trajectory...
-
HAkAu: hybrid algorithm for effective k-automorphism anonymization of social networks
Online social network datasets contain a large amount of various information about their users. Preserving users’ privacy while publishing or sharing...

-
Manhattan-based k-member clustering and enhanced rabbit optimization algorithm for k-anonymization in social network
Online social networks are becoming more and more popular, according to recent trends. The user's primary concern is the secure preservation of their...

-
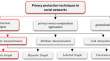
Protecting the privacy of social network data using graph correction
Today, the rapid development of online social networks, as well as low costs, easy communication, and quick access with minimal facilities have made...
-
Application-Oriented Anonymization Framework for Social Network Datasets and IoT Environments
Everyday usage of online Internet services and the recent rise of the Internet of Things (IoT) cause the collection of a massive amount of data,...
-
Model-Agnostic Utility-Preserving Biometric Information Anonymization
The recent rapid advancements in both sensing and machine learning technologies have given rise to the universal collection and utilization of...

-
Path-Preserving Anonymization for Inter-domain Routing Policies
The Internet consists of tens of thousands of autonomous systems (ASes), which exchange routing information through policy-based routing protocols,...
-
Utility-Preserving Biometric Information Anonymization
The use of biometrics such as fingerprints, voices, and images are becoming increasingly more ubiquitous through people’s daily lives, in...
-
Community-Preserving Social Graph Release with Node Differential Privacy
The goal of privacy-preserving social graph release is to protect individual privacy while preserving data utility. Community structure, which is an...
-
Globally Consistent Vertical Federated Graph Autoencoder for Privacy-Preserving Community Detection
Community detection is a trendy area in research on complex network analysis and has a wide range of real-world applications, like advertising. As...
-
Based on Financial Characteristics to Capture the Source of Funds of the Ponzi Scheme on Ethereum with Graph Traversal Technology
Detecting Ponzi schemes in blockchain is an urgent task due to the various illegal transactions generated on the blockchain, among which Ponzi...
-
Graph neural networks: a survey on the links between privacy and security
Graph neural networks (GNNs) are models that capture the dependencies between graph data by passing messages between graph nodes and they have been...

-
High-performance pseudo-anonymization of virtual power plant data on a CPU cluster
The considerable move towards the use of renewable energy resources has been provided by the digitization of energy systems with the help of virtual...

-
DUEF-GA: data utility and privacy evaluation framework for graph anonymization
Anonymization of graph-based data is a problem which has been widely studied over the last years, and several anonymization methods have been...

-
Heterogeneous graph neural network with semantic-aware differential privacy guarantees
Most social networks can be modeled as heterogeneous graphs. Recently, advanced graph learning methods exploit the rich node properties and...

-
Efficient approximation and privacy preservation algorithms for real time online evolving data streams
Because of the processing of continuous unstructured large streams of data, mining real-time streaming data is a more challenging research issue than...

-
DYGL: A Unified Benchmark and Library for Dynamic Graph
Difficulty in reproducing the code and inconsistent experimental methods hinder the development of the dynamic network field. We present DYGL, a...
