Search
Search Results
-
Device (Chip Design) Modeling
This chapter provides the principles and implementations of FPGA device (chip design) modeling. FPGA device information can be derived from the...
-
Device Characterization for Opportunistic Networks
When implementing opportunistic networks in real applications, not only connectivity problems need to be addressed, but also device restrictions....
-
Networked Industrial Control Device Asset Identification Method Based on Improved Decision Tree
Industrial control device asset identification is essential to the active defense and situational awareness system for industrial control network...

-
Towards cyber awareness among smart device users: an interactive, educational display of IoT device vendors compromise history
In recent history, individual-owned devices were used to launch widespread botnet attacks like Mirai. it is therefore critically needed to educate...

-
HandiMathKey-Device
Ty** mathematics is sometimes difficult with text editor functions for students with motor impairment and other associated impairments (visual,...
-
Enhancing smart home device identification in WiFi environments for futuristic smart networks-based IoT
The recognition of smart home devices within WiFi environments stands as a pivotal focus within contemporary Internet of Things (IoT) security,...

-
Radio frequency fingerprinting techniques for device identification: a survey
The Internet of Things (IoT) paradigm and the advanced wireless technologies of 5G and beyond are expected to enable diverse applications such as...

-
Advanced Memory and Device Packaging
Assembly and reliability of memory device packaging are very important topics in semiconductor manufacturing. There are many books and papers written...
-
Wearable Device Dataset for Stress Detection
Stressful situations produce physiological changes that are difficult to measure. Among the acute stress body effects, increased blood glucose level...
-
H4VDM: H.264 Video Device Matching
Methods that can determine if two given video sequences are captured by the same device (e.g., mobile telephone or digital camera) can be used in...
-
An embedded device-oriented fatigue driving detection method based on a YOLOv5s
Currently, most fatigue driving detection methods rely on complex neural networks whose feasibility in hardware implementation needs to be further...
-
Lattice-based device-to-device authentication and key exchange protocol for IoT system
Protecting IoT environments from the increasing number of cyber threats has grown more important as the number of Internet of Things (IoT) devices...

-
Experience Design for Multi-device Sharing Based on 3C Framework
With the development of current technology, intelligent interaction scenarios based on multi-device collaboration are becoming more and more...
-
On-Device Query Auto-completion for Email Search
Traditional query auto-completion (QAC) relies heavily on search logs collected over many users. However, in on-device email search, the scarcity of...
-
Adaptive device sampling and deadline determination for cloud-based heterogeneous federated learning
As a new approach to machine learning, Federated learning enables distributned traiing on edge devices and aggregates local models into a global...

-
Device personalization for heterogeneous populations: leveraging physician expertise and national population data to identify medical device patient user groups
Interaction with patient-facing medical devices requires integrated performance of both physical and cognitive tasks that are highly dependent on...

-
Device to Device Communication over 5G
The dependency on small cells, the cost of establishing a 5G infrastructure, and traffic at the Base Transceiver Station (BTS) can be reduced by...
-
Opening the “Black Box” of VR for Workforce Development: Investigating Learners’ Device, Usage, and Identities
Virtual reality (VR) technologies are increasingly used in workforce development and training, and studies show they can be effective tools to...
-
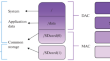
Approach for Protecting Mobile Device User’s Data Based on Multifactor Authentication, Visual Cryptography, and Steganography
AbstractAn approach is proposed to protect user’s personal data stored on mobile devices running the Android OS, which combines multifactor...
-
Research of ReLU output device in ternary optical computer based on parallel fully connected layer
When implementing fully connected layer computation on electronic computer (EC), slow computing speed and high power consumption result in the...

