Search
Search Results
-
Ensemble recognition model with optimal training for multimodal biometric authentication
Biometric security methods deploy any type of biometric recognition for safety purposes. Different from unimodal biometric system that uses single...

-
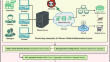
Cryptography with optimal deep learning-based authentication scheme for preserving anonymity in telecare medical information system
The Telecare Medicine Information System (TMIS) revolutionizes healthcare delivery by integrating medical equipment and sensors, facilitating...
-
Authentication Protocols and Key Establishment
This chapter discusses authentication protocols involving cryptographic algorithms. The main focus is authenticated key establishment protocols...
-
SUACC-IoT: secure unified authentication and access control system based on capability for IoT
With the widespread use of Internet of Things (IoT) in various applications and several security vulnerabilities reported in them, the security...

-
Security of lightweight mutual authentication protocols
Sensors and IoT (Internet of Things), which include RFID (Radio-Frequency IDentification) tags, have witnessed widespread adoption across a wide...

-
Towards serverless fast one round authentication with two mobile end devices
We newly present a
f asto ne-rounda uthentication protocol between two IoTm obile end devices (FOAM ). OurFOAM is based on a practical authentication...
-
Blockchain enabled zero trust based authentication scheme for railway communication networks
With the introduction of emerging technologies such as cloud computing, the railway communication network has the characteristics of complex...

-
TAKM-FC: Two-way Authentication with efficient Key Management in Fog Computing Environments
A mechanism of fog computing environment is employed in order to enhance the cloud computing services toward the edge devices in a range of locations...

-
Approach for Protecting Mobile Device User’s Data Based on Multifactor Authentication, Visual Cryptography, and Steganography
AbstractAn approach is proposed to protect user’s personal data stored on mobile devices running the Android OS, which combines multifactor...
-
Enhancing security of biometrics based authentication framework for DRM system
Due to current advancements in digital and Internet technologies, digital content theft has grown to a significant degree. Digital rights management...

-
An efficient mCK signing and mobile based identity solution for authentication
With the growing spread of mobile devices, many services are accessed using such devices and hence there is a need to have an authentication...

-
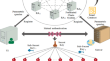
Blockchain-based mutual authentication protocol without CA
Nowadays, most of the federation chain identity authentication adopts the certificate authentication of CA (Certification Authority) under PKI...
-
Use of hybrid post-quantum key exchange in internet protocols
This article describes the current situation with incorporating hybrid post-quantum key exchange into the internet security protocols taking TLS 1.3...

-
AMAKAS: Anonymous Mutual Authentication and Key Agreement Scheme for securing multi-server environments
The rapid growth of Internet users was the motivation of the emerge appearance of new computing models such as cloud computing, fog computing and...

-
A conditional privacy-preserving and desynchronization-resistant authentication protocol for vehicular ad hoc network
Vehicular ad hoc network (VANET) has become an indispensable requirement in smart cities. The major applications are acquiring traffic information,...

-
Hiding Your Signals: A Security Analysis of PPG-Based Biometric Authentication
Recently, physiological signal-based biometric systems have received wide attention. Photoplethysmogram (PPG) signal is easy to measure, making it...
-
A double-embedding hidden image encryption and authentication scheme based on compressed sensing and double random phase encoding
The image may be maliciously tampered when transmitted on the shared platform, and the receiver cannot determine whether the received image is a true...

-
Blockchain assisted AHMFA authentication in employee performance assessment system
The concept of blockchain has attained more attention recently to promote secured encryption and decryption, especially in industrial explorations...

-
A fog-based anonymous authentication scheme with location privacy for wireless body area network with FPGA implementation
In Healthcare 4.0, Wireless Body Area Networks (WBAN) takes place a major role in gathering real-time data of patients. The gathered real-time...

-
Performance analysis of 5GMAKA: lightweight mutual authentication and key agreement scheme for 5G network
In this paper, we have proposed a lightweight mutual authentication and key agreement scheme for 5G (5GMAKA) using the symmetric-key cryptographic...

