Search
Search Results
-
Graph-Level Anomaly Detection via Hierarchical Memory Networks
Graph-level anomaly detection aims to identify abnormal graphs that exhibit deviant structures and node attributes compared to the majority in a...
-
Virtual Memory
Virtual memory is a technique that allows the execution of the processes that may not be completely in memory. One major advantage of this scheme is...
-
HeterMM: applying in-DRAM index to heterogeneous memory-based key-value stores
We propose HeterMM, a versatile framework that leverages in-DRAM indexes in KV stores on heterogeneous memory. HeterMM incorporates a plug-in...
-

-
NEHASH: high-concurrency extendible hashing for non-volatile memory
Extendible hashing is an effective way to manage increasingly large file system metadata, but it suffers from low concurrency and lack of...
-
Iteration Structures
This chapter shows how iterations structures work using flowcharts, pseudocode and Java. It includes pretest indefinite loop structures, both count...
-
Main memory controller with multiple media technologies for big data workloads
SRAM and DRAM memory technologies have been dominant in the implementations of memory subsystems. In recent years, and mainly driven by the huge...

-
Pimo: memory-efficient privacy protection in video streaming and analytics
Video streaming from cameras to backend cloud or edge servers for neural-based analytics has gained significant popularity. However, the transmission...
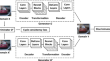
-
Predicting Memory Demands of BDD Operations Using Maximum Graph Cuts
The BDD package Adiar manipulates Binary Decision Diagrams (BDDs) in external memory. This enables handling big BDDs, but the performance suffers...
-
Range Indexes on Non-Volatile Memory
In this chapter, we survey range indexes built for non-volatile memory. They are typically built on top of B+-trees, tries, or a hybrid of both. Our...
-
Implementation of 16 Boolean logic operations based on one basic cell of spin-transfer-torque magnetic random access memory
In-memory computing (IMC) systems based on emerging nonvolatile memories (NVMs) provide a thorough solution for memory wall issues and von Neumann...
-
Chinese Named Entity Recognition Augmented with Lexicon Memory
Inspired by the concept of content-addressable retrieval from cognitive science, we propose a novel fragmentbased Chinese named entity recognition...
-
Transformation of C Programming Language Memory Model into Object-Oriented Representation of EO Language
Abstract—The paper analyzes the possibilities of transforming C programming language constructs into objects of EO programming language. The key...
-
Distributed out-of-memory NMF on CPU/GPU architectures
We propose an efficient distributed out-of-memory implementation of the non-negative matrix factorization (NMF) algorithm for heterogeneous...

-
More Data Structures
Welcome to Chapter 5 ! In this chapter, we’ll spend some more time exploring some common data structures provided...
-
Optimizing B+-tree for hybrid memory with in-node hotspot cache and eADR awareness
The advance in Non-Volatile Memory (NVM) has changed the traditional DRAM-only memory system. Compared to DRAM, NVM has the advantages of...
-
Optimization of OLAP In-Memory Database Management Systems with Processing-In-Memory Architecture
With the growing popularity of Processing-In-Memory (PIM) technology, many sectors of the industry are willing to take advantage of this new...
-
Deep Memory-Augmented Proximal Unrolling Network for Compressive Sensing
Map** a truncated optimization method into a deep neural network, deep proximal unrolling network has attracted attention in compressive sensing...

-
Memory Management
Most programs work on more data than a typical processor can hold in its registers, so data needs to be stored in memory or long-term store (such as...
-
Memory enhancement method based on Skip-GANomaly for anomaly detection
Unsupervised anomaly detection methods based on the Generative Adversarial Network have solved the problem of supervised anomaly detection methods...

