Search
Search Results
-
L3AM: Linear Adaptive Additive Angular Margin Loss for Video-Based Hand Gesture Authentication
Feature extractors significantly impact the performance of biometric systems. In the field of hand gesture authentication, existing studies focus on...

-
Dynamic authentication for intelligent sensor clouds in the Internet of Things
Sensor clouds are formed by IP-enabled wireless sensors and Internet of Things devices that are used for sensing and actuation in commercial and...

-
Provable secure authentication key agreement for wireless body area networks
Wireless body area networks (WBANs) guarantee timely data processing and secure information preservation within the range of the wireless access...
-
Challenges and Future Directions in the Implementation of Quantum Authentication Protocols
Quantum computing is a powerful concept in the technological world that is critically valued in information security due to its enhanced computation...
-
A secure elliptic curve based anonymous authentication and key establishment mechanism for IoT and cloud
Abstract
With the increased number of smart devices in IoT and cloud, communication messages are exchanged extensively throughout the network. This...

-
A provably lightweight mutually authentication and key establishment protocol using extended chaotic map for telecare medicine information system
Telecare Medicine Information System (TMIS) provides patient’s efficient and convenient e-healthcare services where the patient private health...

-
Time dependency: an efficient biometric-based authentication for secure communication in wireless healthcare sensor networks
Healthcare systems promise a significant impact in the field of quality of life. However, security is one of the hottest topics that must be...

-
ECG-based authentication systems: a comprehensive and systematic review
In recent years, security systems based on biometric features have become a promising solution to identify humans, and it is preferred over...

-
Enhanced authentication security for IoT client nodes through T-ECDSA integrated into MQTT broker
Advancements in computing and communication technology have increased the number of devices connected to the Internet, leading to the emergence of...

-
Impact of Consensus Protocols on the Efficiency of Registration and Authentication Process in Self-sovereign Identity
Self-Sovereign Identity (SSI), allows each entity to control its identities with minimal data disclosure to ensure privacy, through its concepts of...
-
A secure blockchain-assisted authentication framework for electronic health records
The evolution of internet technology has significantly broadened the accessibility of E-healthcare services, with Electronic Healthcare Records (EHR)...

-
A biometrics-based mutual authentication and key agreement protocol for TMIS using elliptic curve cryptography
Telecare Medicine Information System (TMIS) refers to a medical model that uses communication and information technology to realize multiple medical...

-
BSAS: blockchain-based shareable authentication scheme for smart healthcare
Nowadays, research efforts are strongly directed toward integrating Blockchain into Smart Healthcare Systems to achieve distribution, transparency,...

-
A dynamic C-V2X anonymous authentication and group key agreement protocol
At present, in addressing security challenges within 5 G-era Vehicular Ad-Hoc Networks (VANET), a new protocol has been designed in this paper, named...

-
Secure authentication framework for IoT applications using a hash-based post-quantum signature scheme
In today’s era, numerous applications are evolving into smart applications by leveraging technologies like the Internet of Things (IoT), Artificial...

-
Password based authentication for web based graphics computing services retrieval in cloud
In the global environment privacy and security issues were critical to handle the huge number of participants. Many security-based research works...

-
Blockchain-assisted secure message authentication with reputation management for VANETs
Message authentication is of great significance for secure information sharing in vehicular ad hoc networks. Due to the lack of verification of...

-
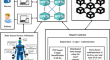
A privacy preserving quantum authentication scheme for secure data sharing in wireless body area networks
The wireless body area network (WBAN) has emerged as a promising networking paradigm thanks to embedded systems, integrated circuit technologies, and...
-
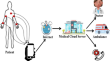
TFAS: two factor authentication scheme for blockchain enabled IoMT using PUF and fuzzy extractor
Security vulnerabilities associated with Internet of Medical Things (IoMT) may lead to health disasters. The researchers already have designed...
-
Stronger Authentication
Different methods of authentication are not considered equal. The static passwords that still enable access to many Internet services are considered...
