Search
Search Results
-
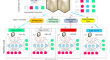
IoT workload offloading efficient intelligent transport system in federated ACNN integrated cooperated edge-cloud networks
Intelligent transport systems (ITS) provide various cooperative edge cloud services for roadside vehicular applications. These applications offer...
-
Using Blockchains for Censorship-Resistant Bootstrap** in Anonymity Networks
With Tor being a popular anonymity network, many censors and ISPs have blocked access to it. Tor relies on privately and selectively distributing IPs...
-
On Evaluating Anonymity of Onion Routing
Anonymous communication networks (ACNs) aim to thwart an adversary, who controls or observes chunks of the communication network, from determining...
-
Measuring Tor Relay Popularity
Tor is one of the most popular anonymity networks. It has been reported that over 2 million unique users utilize the Tor network daily. The Tor...
-
A Machine Learning Approach to Detect Differential Treatment of Anonymous Users
Anonymous Internet use is essential to safeguard against mass surveillance and to protect privacy online. Tor Browser and the Tor anonymity network...
-
Handling Exit Node Vulnerability in Onion Routing with a Zero-Knowledge Proof
Onion routing is a method for anonymous data transfer in a communication network. It is mostly used for the deep web via TOR's (The Onion Router)...
-
RAP: A Lightweight Application Layer Defense Against Website Fingerprinting
Website fingerprinting (WFP) attacks threaten user privacy on anonymity networks because they can be used by network surveillants to identify...
-
Blockchain Capabilities in Defending Advanced Persistent Threats Using Correlation Technique and Hidden Markov Models (HMM)
In December 2019, the world witnessed the start of a pandemic outbreak (Coronavirus or COVID-19) in Wuhan the capital of China’s Hubei province and...
-
Ransomware attacks in the context of generative artificial intelligence—an experimental study
Ransomware attacks continue to be one of the biggest risks faced by both organizations and governments. In this experimental study, the author tested...
-
Beyond the Surface Web: How Criminals Are Utilising the Internet to Commit Crimes
The internet has revolutionised society and plays a key role in users lives. The rapid advances in technology means that now more than ever, users...
-
Mobile botnet detection: a comprehensive survey
The number of people using mobile devices is increasing as mobile devices offer different features and services. Many mobile users install various...

-
An Information Privacy Competency Model for Online Consumers
E-commerce has taken a prominent role in our everyday life. However, the increasing disclosure of personal information as a prerequisite to join in...
-
Hybrid intelligent feature selector framework for darknet traffic classification
With the rapid growth in the internet traffic, analysis and exploration of traffic classification has become more challenging task especially for...

-
Hydra: Practical Metadata Security for Contact Discovery, Messaging, and Voice Calls
Protecting communications’ metadata can be as important as protecting their content, i.e., recognizing someone contacting a medical service may...

-
Assessing the Health of the Dark Web:
A hidden part of the World Wide Web is known as the Dark Web, featuring websites that cannot be indexed by traditional search engines. Many open...
-
A Quantitative Model for Analysis and Evaluation of Tor Hidden Service Discovery
Tor is one of the most popular anonymous communication systems, and its ability of providing receiver anonymity makes hidden services more and more...
-
Cybersecurity of Smart Home Systems: Sensor Identity Protection
Smart home systems are designed as platforms for connecting sensors, home appliances, and devices to exchange data and, ultimately, to provide useful...

-
MuChat against active attacks, passive attacks, and traffic analysis methods: a free convert chat application for instant communication on mobile
In recent years, Censorship and anti-censorship technology is develo** rapidly. The censorship and surveillance systems track traffic on the...

-
Why Do People Pay for Privacy-Enhancing Technologies? The Case of Tor and JonDonym
Today’s environment of data-driven business models relies heavily on collecting as much personal data as possible. One way to prevent this extensive...
-
An Analysis of the Dark Web Challenges to Digital Policing
The Dark Web is the hidden group of Internet sites that can only be accessed through specific software. The Dark Web enables private computer...
