Search
Search Results
-
Authentication
Authentication is the process of validating the identity of someone or something. It uses information provided to the authenticatorAuthenticator to...
-
REACH: Robust Efficient Authentication for Crowdsensing-based Healthcare
Crowdsensing systems use a group of people to collect and share sensor data for various tasks. One example is the crowdsensing-based healthcare...

-
Lightweight group authentication protocol for secure RFID system
Nowadays, wireless technology has been widely used in healthcare and communication systems. It makes our life easier in all respects. A...

-
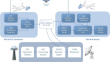
Lightweight secure authentication protocol for automatic dependent surveillance broadcast system
This article highlights the importance of Air Traffic Control in ensuring the security and efficiency of international aviation operations....
-
Fuzzy miner selection toward Blockchain-based secure communication using multifactor authentication
The medical cyber-physical system utilizes various Internet of Medical Things (IoMT) devices that are connected to the network for real-time...

-
An anonymous authentication and secure data transmission scheme for the Internet of Things based on blockchain
With the widespread use of network infrastructures such as 5G and low-power wide-area networks, a large number of the Internet of Things (IoT) device...
-
Chaotic map based multi-factor authentication protocol for underwater environment monitoring
The underwater environment holds significant potential for advancing ecosystem understanding, industrial operations, and early natural disaster...

-
A novel Blockchain-based authentication scheme for telecare medical information system
Data interoperability in health-care is a problem that has yet to be solved. The key question is how to accomplish data confidentiality, data...

-
Enhancing data authentication in software-defined networking (SDN) using multiparty computation
In software-defined networking (SDN), where software assumes a progressively prominent position in the network administration, it becomes imperative...

-
A Lightweight Authentication Protocol for a Blockchain-Based Off-Chain Medical Data Access in Multi-server Environment
Presently, blockchain technology is used to secure electronic medical records (EMR) and an arrangement of multiple servers as off-chain storage is...

-
Secure privacy-enhanced fast authentication and key management for IoMT-enabled smart healthcare systems
The smart healthcare system advancements have introduced the Internet of Things, enabling technologies to improve the quality of medical services....

-
UPSRVNet: Ultralightweight, Privacy preserved, and Secure RFID-based authentication protocol for VIoT Networks
Vehicular Internet of Things (VIoT) refers to integrating Internet of Things (IoT) technology into the transportation sector, specifically vehicles....

-
A lightweight certificate-based authentication scheme for 6LoWPAN-based internet of things
As the 6LoWPAN devices in the Internet of Things (IoT) applications communicate sensitive information over the unattended and insecure channel, it is...

-
Lattice-based device-to-device authentication and key exchange protocol for IoT system
Protecting IoT environments from the increasing number of cyber threats has grown more important as the number of Internet of Things (IoT) devices...

-
Public key versus symmetric key cryptography in client–server authentication protocols
Every month, several new protocols are pop** up, comparing themselves with a few others and claiming to outperform the whole state of the art. The...
-
Traditional Authentication
The paradigm for user authentication has not greatly changed since computers came to market; many systems still rely on passwords. This chapter...
-
Role of authentication factors in Fin-tech mobile transaction security
Fin-Tech is the merging of finance and technology, to be considered a key term for technology-based financial operations and money transactions as...

-
A blockchain-based security system with light cryptography for user authentication security
Nowadays, the Internet of Things (IoT) enables the creation of a wide range of new services, including smart cities, agriculture, energy, technology,...

-
Unboxing fog security: a review of fog security and authentication mechanisms
Due to the massive advancement of the Internet of Things in our day-to-day lives, there is a strong need to bring connectivity to a very accessible...

-
L3AM: Linear Adaptive Additive Angular Margin Loss for Video-Based Hand Gesture Authentication
Feature extractors significantly impact the performance of biometric systems. In the field of hand gesture authentication, existing studies focus on...

