Search
Search Results
-
Low-light image enhancement using the illumination boost algorithm along with the SKWGIF method
Low-light image enhancement is highly desirable for outdoor image processing and computer vision applications. Research conducted in recent years has...

-
A side match oriented data hiding based on absolute moment block truncation encoding mechanism with reversibility
Owing to life style changes during COVID, communication channels were forced to change. Online services ramped up to replace traditional services. It...

-
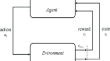
Active reinforcement learning based approach for localization of target ROI (region of interest) in cervical cell images
The localization of tumour is an important factor towards the detection of malignant cervical cells. A Deep Q-Network (DQN) algorithm was implemented...
-
Designing preschool children's educational games for enlightenment through decision analysis methods
As an innovative form of digital online education, educational games have potentially significant impacts on preschool children's enlightenment...

-
Robust stochastic gradient descent with momentum based framework for enhanced chest X-ray image diagnosis
Our study focuses on the difficulties that radiologists encounter while interpreting Chest X-Ray images, which arise from the inherent ambiguity. We...
-
Mcti: mixed-criticality task-based isolation
The ever-increasing demand for high performance in the time-critical, low-power embedded domain drives the adoption of powerful but unpredictable,...

-
Machine learning-based opinion extraction approach from movie reviews for sentiment analysis
The field of sentiment mining, also known as sentiment analysis and sentiment extraction, has shown a surge with diverse applications. Various...

-
A new weighted ensemble model-based method for text implication recognition
In the context of text entailment recognition, there exists a risk of getting stuck in local optima when using a single pretrained model. To address...

-
Big data analysis of mental health intervention effects in student-athletes: based on data mining techniques and affective computing algorithms
Student-athletes suffer specific pressures and obstacles in regard to their studies and sports performance, making mental health concerns a major...

-
RALFusion: a residual attention guided lightweight deep-learning framework for infrared and visible image fusion
Infrared and visible image fusion plays an important role in subsequent advanced visual tasks, especially for complex marine environments. To improve...

-
Towards enhancing shadow removal from images
Addressing challenges posed by shadows in computer vision tasks, this study employs advanced deep learning techniques for shadow removal in RGB...

-
BangleFIR: bridging the gap in fashion image retrieval with a novel dataset of bangles
In this paper, we introduce Bangle Fashion Image Retrieval (BangleFIR), a novel dataset focusing on bangles within the fashion domain. While garment...

-
A review of video-based human activity recognition: theory, methods and applications
Video-based human activity recognition (HAR) is an important task in many fields, such as healthcare monitoring, video surveillance, and sports...

-
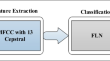
Fast Learning Network Algorithm for Voice Pathology Detection and Classification
The utilisation of ML (Machine Learning) techniques in the detection of the VP (Voice Pathology) has recently gained a lot of consideration. However,...
-
Enhancement of patient's health prediction system in a graphical representation using digital twin technology
The patient health prediction system is the most critical study in medical research. Several prediction models exist to predict the patient's health...

-
Real-time and secure identity authentication transmission mechanism for artificial intelligence generated image content
The rapid development of generative artificial intelligence technology and large-scale pre-training models has led to the emergence of artificial...

-
Smart contract vulnerabilities detection with bidirectional encoder representations from transformers and control flow graph
Up to now, the smart contract vulnerabilities detection methods based on sequence modal data and sequence models have been the most commonly used....

-
A novel single kernel parallel image encryption scheme based on a chaotic map
The development of communication technologies has increased concerns about data security, increasing the prominence of cryptography. Images are one...

-
TSDAnet: texture strip dual attention network for intraclass texture classification
Intraclass texture classification is a challenging task due to the high similarity between subtypes within the same texture. The presence of...

-
An optimized deep network-based intermediate code generation for the mathematical expression
In recent times, the system's mathematical expression and operation have gained greater reach in engineering and mathematics. It is vital to solving...

