Search
Search Results
-
A two-stage-UNet network based on group normalization for single image deraining
Rain streaks can seriously damage the optical quality of image and affect image processing in many scenes. Deep learning methods achieve...

-
Swarm-intelligence for the modern ICT ecosystems
Digitalization is continuing facilitating our daily lives. The world is interconnected as never before, bringing close people, businesses, or other...

-
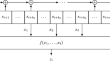
Multivariate correlation attacks and the cryptanalysis of LFSR-based stream ciphers
Cryptanalysis of modern symmetric ciphers may be done by using linear equation systems with multiple right hand sides, which describe the encryption...
-
Graph-Enhanced Prompt Learning for Personalized Review Generation
Personalized review generation is significant for e-commerce applications, such as providing explainable recommendation and assisting the composition...

-
A dynamic C-V2X anonymous authentication and group key agreement protocol
At present, in addressing security challenges within 5 G-era Vehicular Ad-Hoc Networks (VANET), a new protocol has been designed in this paper, named...

-
SenseMLP: a parallel MLP architecture for sensor-based human activity recognition
Human activity recognition (HAR) with wearable inertial sensors is a burgeoning field, propelled by advances in sensor technology. Deep learning...

-
Low-parameter GAN inversion framework based on hypernetwork
In response to the significant parameter overhead in current Generative Adversarial Networks (GAN) inversion methods when balancing high fidelity and...

-
More accurate heatmap generation method for human pose estimation
Human pose estimation plays a crucial role in computer vision, such as understanding body language and tracking behavior. We observed that neural...

-
Bases for Riemann–Roch spaces of linearized function fields with applications to generalized algebraic geometry codes
Several applications of function fields over finite fields, or equivalently, algebraic curves over finite fields, require computing bases for...
-
BCRA: bidirectional cross-modal implicit relation reasoning and aligning for text-to-image person retrieval
Text-to-image person retrieval aims to retrieve relevant target individuals based on given textual descriptions. The main challenge faced by this...

-
Multi-view and region reasoning semantic enhancement for image-text retrieval
Image and text retrieval is a crucial topic in the fields of language and vision. The key to successful Image-Text retrieval is achieving accurate...

-
Channel-Enhanced Contrastive Cross-Domain Sequential Recommendation
Sequential recommendation help users find interesting items by modeling the dynamic user-item interaction sequences. Due to the data sparseness...

-
The usability and user experience of an interactive e-learning platform to empower older adults when using electronic personal health records: an online intervention study
Since the introduction of the electronic Personal Health Record (ePHR) in Germany in 2021, usage rates among those with statutory health insurance...

-
ASFESRN: bridging the gap in real-time corn leaf disease detection with image super-resolution
Plant diseases pose a significant threat to agricultural productivity, emphasizing the essential need for early detection and diagnosis. While recent...

-
LMFE-RDD: a road damage detector with a lightweight multi-feature extraction network
Road damage detection using computer vision and deep learning to automatically identify all kinds of road damage is an efficient application in...
-
Conversational versus graphical user interfaces: the influence of rational decision style when individuals perform decision-making tasks repeatedly
When performing decision-making tasks, individuals commonly use the user interface (UI) of a decision aid repeatedly. Conversational user interfaces...

-
Class imbalance in multi-resident activity recognition: an evaluative study on explainability of deep learning approaches
Recognizing multiple residents’ activities is a pivotal domain within active and assisted living technologies, where the diversity of actions in a...

-
ConIS: controllable text-driven image stylization with semantic intensity
Text-driven image stylization aims to synthesize content images with learned textual styles. Recent studies have shown the potential of the diffusion...

