Search
Search Results
-
PointDMIG: a dynamic motion-informed graph neural network for 3D action recognition
Point cloud contains rich spatial information, providing effective supplementary clues for action recognition. Existing action recognition algorithms...
-
Security analysis of the ISO standard \(\textsf{OFB}\)-\(\textsf{DRBG}\)
Deterministic random bit generators (DRBGs) are essential tools in modern cryptography for generating secure and unpredictable random numbers. The...

-
A survey of compositional inverses of permutation polynomials over finite fields
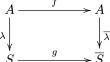
In this paper, we survey on the recent results and methods in the study of compositional inverses of permutation polynomials over finite fields. In...
-
Constructions for t-designs and s-resolvable t-designs
The purpose of the present paper is to introduce recursive methods for constructing simple t -designs, s -resolvable t -designs, and large sets of t -desi...
-
Finding orientations of supersingular elliptic curves and quaternion orders
An oriented supersingular elliptic curve is a curve which is enhanced with the information of an endomorphism. Computing the full endomorphism ring...

-
DMFNet: deep matrix factorization network for image compressed sensing
Due to its outstanding performance in image processing, deep learning (DL) is successfully utilized in compressed sensing (CS) reconstruction....

-
Acnn: arbitrary trace attacks based on leakage area detection
Deep Learning-based Side-Channel Analysis (DL-SCA) has emerged as a powerful method in the field of side-channel analysis. Current works on DL-SCA...

-
Multi-branch feature fusion and refinement network for salient object detection
With the development of convolutional neural networks (CNNs), salient object detection methods have made great progress in performance. Most methods...

-
Impact Assessment as a Legal Design Pattern—A “Timeless Way” of Managing Future Risks?
Impact assessments are increasingly employed and debated as instruments for mitigating the fundamental rights risks associated with artificial...

