Search
Search Results
-
AI Ethics, the Neuralink Enigma, and Statistical Inference as the Anticlimax of Machiavelli’s Prince
Elon Musk’s Neuralink, one more company hopes to dominate the brain-computer interface (BCI) market, has implanted a brain-reading device into a...

-
Trust management in the internet of vehicles: a systematic literature review of blockchain integration
The Internet of Vehicles (IoV) promises to revolutionize transportation in smart cities, but its interconnectedness raises critical security and...

-
Vectorial negabent concepts: similarities, differences, and generalizations
In Pasalic et al. (IEEE Trans Inf Theory 69:2702–2712, 2023), and in Anbar and Meidl (Cryptogr Commun 10:235–249, 2018), two different vectorial...
-
Blind quality evaluator for multi-exposure fusion image via joint sparse features and complex-wavelet statistical characteristics
Multi-Exposure Fusion (MEF) technique aims to fuse multiple images taken from the same scene at different exposure levels into an image with more...

-
Context-aware adaptive network for UDA semantic segmentation
Unsupervised Domain Adaptation (UDA) plays a pivotal role in enhancing the segmentation performance of models in the target domain by mitigating the...

-
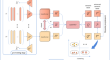
Deep contrastive multi-view clustering with doubly enhanced commonality
Recently, deep multi-view clustering leveraging autoencoders has garnered significant attention due to its ability to simultaneously enhance feature...
-
Quality evaluation methods of handwritten Chinese characters: a comprehensive survey
Quality evaluation of handwritten Chinese characters aims to automatically quantify and assess handwritten Chinese characters through computer vision...

-
Expediting the design and development of secure cloud-based mobile apps
The adoption and popularity of mobile devices by end-users is partially driven by the increasing development and availability of mobile applications...

-
Some self-dual codes and isodual codes constructed by matrix product codes
In 2020, Cao et al. proved that any repeated-root constacyclic code is monomially equivalent to a matrix product code of simple-root constacyclic...
-
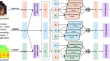
FEF-Net: feature enhanced fusion network with crossmodal attention for multimodal humor prediction
Humor segment prediction in video involves the comprehension and analysis of humor. Traditional humor prediction has been text-based; however, with...
-
Digital Health Empowerment, Autonomy, and the Capability Approach: Reply to de Proost and Grey
De Proost & Grey criticize Nickel et al.’s article “Justice and empowerment through digital health: ethical challenges and opportunities,” arguing...
-
Safety and Privacy in Immersive Extended Reality: An Analysis and Policy Recommendations
Extended reality (XR) technologies have experienced cycles of development—“summers” and “winters”—for decades, but their overall trajectory is one of...
-
A channel-gained single-model network with variable rate for multispectral image compression in UAV air-to-ground remote sensing
Unmanned aerial vehicle (UAV) air-to-ground remote sensing technology, has the advantages of long flight duration, real-time image transmission, wide...

-
Some constacyclic BCH codes with good parameters
BCH codes as a subclass of constacyclic BCH codes have been widely studied, while the results on the parameters of BCH codes over finite fields are...
-
Multi-party codebook distribution strategy based on secret sharing
The paper addresses the issue of secure distribution of codebooks in the field of information security, particularly in the domain of covert...

-
In Search of Living Law: How Should We Design for (Digital) Legal Interaction?
In his work on human-centric design, urban theorist Christopher Alexander elaborated design patterns as a way to conceptualise and practice urban...

-
Establishing the connection between speech-language pathologists and technology developers in designing novel textile-based AAC (TAAC) technologies
Augmentative and alternative communication (AAC) methods aim to enable a variety of interactions and participation for those with complex...
-
Gaming the system: tetromino-based covert channel and its impact on mobile security
Trojan droppers consistently emerge as challenging malware threats, particularly within the Android ecosystem. Traditional malware detection...

