Search
Search Results
-
Similarity-based face image retrieval using sparsely embedded deep features and binary code learning
Human face retrieval has long been established as one of the most interesting research topics in computer vision. With the recent development of deep...

-
Optimizing pre-copy live virtual machine migration in cloud computing using machine learning-based prediction model
One of the preconditions for efficient cloud computing services is the continuous availability of services to clients. However, there are various...

-
Real-time water surface target detection based on improved YOLOv7 for Chengdu Sand River
It has been a challenge to obtain accurate detection results in a timely manner when faced with complex and changing surface target detection....

-
A QoS-aware routing approach for Internet of Things-enabled wireless sensor networks in smart cities
In the Internet of Things (IoT), optimizing machine performance through data analysis and improved connectivity is pivotal. Addressing the growing...

-
Real-time scheduling of power grid digital twin tasks in cloud via deep reinforcement learning
As energy demand continues to grow, it is crucial to integrate advanced technologies into power grids for better reliability and efficiency. Digital...

-
Unleashing the power of deep neural networks: An interactive exploration of static and dynamic architectures
Static networks, known for their fixed architectures and weights, have been widely employed in diverse applications. However, the emergence of...
-
Deep learning-based classification and application test of multiple crop leaf diseases using transfer learning and the attention mechanism
Crop diseases are among the major natural disasters in agricultural production that seriously restrict the growth and development of crops,...

-
Ensemble methods-based comparative study of Landsat 8 operational land imager (OLI) and sentinel 2 multi-spectral images (MSI) for smart farming crop classification
Agriculture has a significant worldwide impact in terms of generating employment opportunities and stimulating economic growth. In India, agriculture...

-
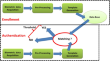
Proposed cancelable biometrics system based on hybrid optical crypto-steganography audio framework for cyber security applications
Biometric authentication systems have gained significant popularity in recent years due to their high level of security and convenience. Cancelable...
-
Adaptive context-aware access control for IoT environments leveraging fog computing
The increasing use of the Internet of Things (IoT) has driven the demand for enhanced and robust access control methods to protect resources from...

-
Using the ACE framework to enforce access and usage control with notifications of revoked access rights
The standard ACE framework provides authentication and authorization mechanisms similar to those of the standard OAuth 2.0 framework, but it is...

-
Visual saliency based maritime target detection
We present an unsupervised maritime target detection method based on visual saliency. From the perspective of maritime target detection as a salient...

-
Enhancing visual clarity in hazy media: a comprehensive approach through preprocessing and feature fusion attention-based dehazing
Particles in the atmosphere, such as dust and smoke, can cause visual clarity problems in both images and videos. Haze is the result of the...

-
DTS: dynamic training slimming with feature sparsity for efficient convolutional neural network
Deep convolutional neural networks have achieved remarkable progress on computer vision tasks over last years. In this paper, we proposed a dynamic...

-
A three-stage quality evaluation method for experience products: taking animation as an example
The diversity and dynamics of quality index information bring challenges to quality assessment of experience products. This paper proposes a...

-
Distributed source DOA estimation based on deep learning networks
With space electromagnetic environments becoming increasingly complex, the direction of arrival (DOA) estimation based on the point source model can...

-
End-to-End No-wait Scheduling for Time-Triggered Streams in Mixed Wired-Wireless Networks
Proprietary communication technologies for time-critical communication in industrial environments are being gradually replaced by Time-sensitive...

-
An efficient quantum oblivious transfer protocol
Oblivious transfer (OT) is a significant two party privacy preserving cryptographic primitive. OT involves a sender having several pieces of...

-
Automating shareable cyber threat intelligence production for closed source software vulnerabilities: a deep learning based detection system
Software can be vulnerable to various types of interference. The production of cyber threat intelligence for closed source software requires...

-
Multi-strategy improved sparrow search algorithm based on first definition of ellipse and group co-evolutionary mechanism for engineering optimization problems
The Sparrow Search Algorithm (SSA) is recognized for its rapid convergence and precision in engineering optimization, yet it faces the challenge of...

