Search
Search Results
-

-
Online Geometric Covering and Piercing
We consider the online version of the piercing set problem, where geometric objects arrive one by one, and the online algorithm must maintain a valid...

-
Slim Tree-Cut Width
Tree-cut width is a parameter that has been introduced as an attempt to obtain an analogue of treewidth for edge cuts. Unfortunately, in spite of its...

-
ZLR: a fast online authenticated encryption scheme achieving full security
Online authenticated encryption has been considered of practical relevance in light-weight environments due to low latency and constant memory usage....

-
Approximating Long Cycle Above Dirac’s Guarantee
Parameterization above (or below) a guarantee is a successful concept in parameterized algorithms. The idea is that many computational problems admit...

-
New Algorithms for Steiner Tree Reoptimization
Reoptimization is a setting in which we are given a good approximate solution of an optimization problem instance and a local modification that...

-
Algebraic Global Gadgetry for Surjective Constraint Satisfaction
The constraint satisfaction problem (CSP) on a finite relational structure B is to decide, given a set of constraints on variables where the...
-
Approximation Algorithms for Covering Vertices by Long Paths
Given a graph, the general problem to cover the maximum number of vertices by a collection of vertex-disjoint long paths seems to escape from the...

-
Constructions of t-strongly multimedia IPP codes with length \(t+1\)
Strongly multimedia identifiable parent property code ( t -SMIPPC) was introduced for protecting multimedia contents from illegally redistributing...
-
Some new constructions of optimal linear codes and alphabet-optimal \((r,\delta )\)-locally repairable codes
In distributed storage systems, an r -Locally Repairable Code ( r -LRC) ensures that a failed symbol can be recovered by accessing at most r other...
-
Structure of CSS and CSS-T quantum codes
We investigate CSS and CSS-T quantum error-correcting codes from the point of view of their existence, rarity, and performance. We give a lower bound...
-
Bounds on data limits for all-to-all comparison from combinatorial designs
In situations where every item in a data set must be compared with every other item in the set, it may be desirable to store the data across a number...
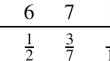
-

-
Efficient quantum algorithms for some instances of the semidirect discrete logarithm problem
The semidirect discrete logarithm problem (SDLP) is the following analogue of the standard discrete logarithm problem in the semidirect product...
-
On duplication-free codes for disjoint or equal-length errors
Motivated by applications in DNA storage, we study a setting in which strings are affected by tandem-duplication errors. In particular, we look at...

-
Improved Approximation Algorithms by Generalizing the Primal-Dual Method Beyond Uncrossable Functions
We address long-standing open questions raised by Williamson, Goemans, Vazirani and Mihail pertaining to the design of approximation algorithms for...

