Search
Search Results
-
Parallel implementation of discrete cosine transform and its inverse for image compression applications
This paper presents the graphics processing unit (GPU) implementation of two-dimensional discrete cosine transform (2D DCT) and inverse discrete...

-
Secure query processing for smart grid data using searchable symmetric encryption
In the last decade, the smart grid has utilized many modern technologies and applications compared with the conventional grid. Cloud computing offers...

-
Conscious points and patterns extraction: a high-performance computing model for knowledge discovery in cognitive IoT
Incorporating cognition into the design and architecture of the Internet of Things (IoT) has recently been the subject of much research, giving rise...

-
An empirical study on cross-component dependent changes: A case study on the components of OpenStack
Modern software systems are composed of several loosely coupled components. Typical examples of such systems are plugin-based systems, microservices,...

-
A network intrusion detection system based on deep learning in the IoT
As industrial and everyday devices become increasingly interconnected, the data volume within the Internet of Things (IoT) has experienced a...

-
A fuzzy ontology-based context-aware encryption approach in IoT through device and information classification
IoT devices produce a vast amount of data ranging from personal to sensitive information. Usually, these devices remain connected to the internet so...

-
Research on satellite link allocation algorithm for Earth-Moon space information network
With ongoing advancements in space exploration and communication technology, the realization of an Earth-Moon space information network is gradually...

-
An exploratory evaluation of code smell agglomerations
Code smell is a symptom of decisions about the system design or code that may degrade its modularity. For example, they may indicate inheritance...

-
Systematizing modeler experience (MX) in model-driven engineering success stories
Modeling is often associated with complex and heavy tooling, leading to a negative perception among practitioners. However, alternative paradigms,...

-
Machine learning-driven performance assessment of network-on-chip architectures
System-on-chip designs for high-performance computing systems widely use network-on-chip (NoC) technology. The critical metrics such as latency,...

-
A new integrated steganography scheme for quantum color images
In this paper, we propose a quantum steganography scheme with a color image as the cover image. In order to enhance the security of the embedded...

-
Exploring recent advances in random grid visual cryptography algorithms
Visual cryptography scheme is initiated to securely encode a secret image into multiple shares. The secret can be reconstructed by overlaying the...

-
Cost-aware workflow offloading in edge-cloud computing using a genetic algorithm
The edge-cloud computing continuum effectively uses fog and cloud servers to meet the quality of service (QoS) requirements of tasks when edge...
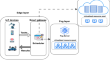
-
An adaptive service deployment algorithm for cloud-edge collaborative system based on speedup weights
In the contemporary landscape of edge computing, the deployment of services with stringent real-time requirements on edge devices is increasingly...

-
iDOCEM
In the business process lifecycle, models can be approached from two perspectives: on the one hand, models are used to create systems in the design...

-
Exploring the potential of Wav2vec 2.0 for speech emotion recognition using classifier combination and attention-based feature fusion
AbstractSelf-supervised learning models, such as Wav2vec 2.0, extract efficient features for speech processing applications including speech emotion...

-
Cost-effective clonal selection and AIS-based load balancing in cloud computing environment
Cloud computing faces challenges in increasing efficiency through task scheduling and load balancing. Various load-balancing methods, including the...

-
Requirements for modelling tools for teaching
Modelling is an important activity in software development and it is essential that students learn the relevant skills. Modelling relies on dedicated...

-
Real-time scheduling of power grid digital twin tasks in cloud via deep reinforcement learning
As energy demand continues to grow, it is crucial to integrate advanced technologies into power grids for better reliability and efficiency. Digital...

-
ASDMG: business topic clustering-based architecture smell detection for microservice granularity
Microservices architecture smells can significantly affect the quality of microservices due to poor design decisions, especially the granularity...

