Search
Search Results
-
Many-objective emergency aided decision making based on knowledge graph
After emergencies occur, decision-makers can reference historical cases with similar causes to take similar emergency response measures. However,...

-
Multiscale dilated convolution and swin-transformer for small sample gearbox fault diagnosis
Mechanical equipment usually operates in noisy and variable load environments, which presents serious challenges for existing intelligent diagnostic...

-
The variable precision fuzzy rough set based on overlap and grou** functions with double weight method to MADM
Variable precision fuzzy rough set (VPFRS) is widely utilized for handling various forms of uncertain information due to its fault-tolerant...
-
ELM: a novel ensemble learning method for multi-target regression and multi-label classification problems
In this paper, a new Ensemble Learning Method (ELM) is proposed to deal with multi-target regression and multi-label classification problems. In ELM,...

-
Multivariate time series anomaly detection via dynamic graph attention network and Informer
In the industrial Internet, industrial software plays a central role in enhancing the level of intelligent manufacturing. It enables the promotion of...

-
Development of an expert-informed rig state classifier using naive bayes algorithm for invisible loss time measurement
The rig state plays a crucial role in recognizing the operations carried out by the drilling crew and quantifying Invisible Lost Time (ILT). This...

-
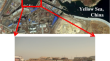
A transfer-learning-based windspeed estimation on the ocean surface: implication for the requirements on the spatial-spectral resolution of remote sensors
The windspeed on the sea surface is an important factor affecting the process of detecting sea surface targets, as it affects the reflection and...
-
Priori separation graph convolution with long-short term temporal modeling for skeleton-based action recognition
Human action recognition from skeleton motion sequences is widely applied in various fields such as virtual reality, human-computer interaction and...

-
Deep learning for higher-order nonparametric spatial autoregressive model
Deep learning technology has been successfully applied in more and more fields. In this paper, the application of deep neural networks in...

-
Semantic-alignment transformer and adversary hashing for cross-modal retrieval
Deep Cross-Modal Hashing (DCMH) has garnered significant attention in the field of cross-modal retrieval due to its advantages such as high...

-
TAENet: transencoder-based all-in-one image enhancement with depth awareness
Recently, CNN-based all-in-one image enhancement methods have been proposed to solve multiple image degradation tasks. However, these CNN-based...

-
A belief interval euclidean distance entropy of the mass function and its application in multi-sensor data fusion
Dempster-Shafer (D-S) evidence theory has extensive applications in the field of data fusion. It uses the mass function to replace the probability...

-
Two guidance joint network based on coarse map and edge map for camouflaged object detection
Camouflaged object detection (COD) entails identifying objects in an image that blend with the background. However, most traditional COD methods have...

-
A new uncertainty processing method for trajectory prediction
In many domains, trajectory prediction a crucial task. Uncertain information, such as complementary and correlated information between multiple...

-
Probabilistic load forecasting based on quantile regression parallel CNN and BiGRU networks
In the dynamic smart grid landscape, accurate probabilistic forecasting of electric load is critical. This paper presents a novel 24-hour-ahead...

-
Progressive image compression for Gaussian mixture model quartile intervals
In this paper, we proposed a novel deep image coding and decoding model for GMMQI (Gaussian mixture model quartile intervals, GMMQI) and a variable...

-
Multistep traffic speed prediction from multiple time-scale spatiotemporal features using graph attention network
Traffic forecasting using deep learning represents a crucial aspect of intelligent transportation systems, carrying substantial implications for...

-
SMoTeF: Smurf money laundering detection using temporal order and flow analysis
Smurfing in financial networks is a popular fraud technique in which fraudsters inject their illegal money into the legitimate financial system. This...

-
CMEFS: chaotic map**-based mayfly optimization with fuzzy entropy for feature selection
Swarm intelligence algorithms availably settle the issue of feature selection for classification, whereas the Mayfly Optimization Algorithm (MOA)...

-
Improvement of robust tensor principal component analysis based on generalized nonconvex approach
The problem of nonconvex robust tensor principal component analysis consists of recovering the low-rank and sparse part from a tensor corrupted by...

