Abstract
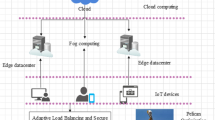
In this paper, to develop an efficient secure authentication scheme and load balancing technique in fog computing. To achieve an efficient secure authentical scheme in addition load balancing method in fog computing, Hybrid Edge DataCenters (HEDC) is developed in this paper. Normally, the EDC can be utilized to set up as a distributed system in addition it is located among the data source and cloud datacentre. This EDC network is also placed in the intermediate layer in the fog hierarchy among cloud datacentres in addition Internet of Things (IoT). This EDC is operated as an intermediate layer in fog computing which is responsible for load balancers and secure authentication in distributing the workload. This EDC fails to achieve efficient secure authentication and manage the workload in fog computing. So, the proposed HEDC is utilized to enable efficient authentication and workload management (load balancing). The proposed method is a combination of EDC and Archimedes Optimization Algorithm (AOA). Based on resource utilization and response time, efficient load balancing is achieved. Additionally, the secure authentication scheme is also attained with the assistance of the HEDC.









Similar content being viewed by others
Availability of data and material
Data sharing not applicable to this article as no datasets were generated or analysed during the current study.
References
Nayeri ZM, Ghafarian T, Javadi B (2021) Application placement in fog computing with AI approach: taxonomy and a state of the art survey. J Netw Comput Appl 185:103078
Murugesan A, Saminathan B, Al-Turjman F, Lakshmana Kumar R (2021) Analysis on homomorphic technique for data security in fog computing. Trans Emerg Telecommun Technol 32(9):e3990
Garg D, Bhatia KK, Gupta S (2020) A research perspective on security in fog computing through blockchain technology. In: International conference on artificial intelligence and sustainable computing. Springer, Cham, pp 91–104
Elaziz A, Mohamed LA, Attiya I (2021) Advanced optimization technique for scheduling IoT tasks in cloud-fog computing environments. Future Gener Comput Syst 124:142–154
Alzoubi YI, Osmanaj VH, Jaradat A, Al-Ahmad A (2021) Fog computing security and privacy for the internet of thing applications: state-of-the-art. Secur Priv 4(2):e145
Al-Hashimi MA, Adnan AR, Rahiman AM, Hamid NAW (2023) Fog-cloud scheduling simulator for reinforcement learning algorithms. Int J Inf Technol. https://doi.org/10.1007/s41870-023-01479-1
Jyotsna, Nand P (2022) Novel DLSNNC and SBS based framework for improving QoS in healthcare-IoT applications. Int J Inf Technol 14(4):2093–2103
Godhrawala H, Sridaran R (2023) A dynamic Stackelberg game based multi-objective approach for effective resource allocation in cloud computing. Int J Inf Technol 15(2):803–818
Neelakantan P, Sudhakar Yadav N (2023) Proficient job scheduling in cloud computation using an optimized machine learning strategy. Int J Inf Technol 15:2409–2421
Md Saquib J, Sajid M (2023) Enhancing the cryptographic key using sample entropy and whale optimization algorithm. Int J Inf Technol 16:1733–1741
Mazumdar N, Nag A, Singh JP (2021) Trust-based load-offloading protocol to reduce service delays in fog-computing-empowered IoT. Comput Electr Eng 93:107223
Kishor A, Chakarbarty C (2021) Task offloading in fog computing for using smart ant colony optimization. Wirel Pers Commun 27:1683–1704
Kaur M, Aron R (2021) FOCALB: fog computing architecture of load balancing for scientific workflow applications. J Grid Comput 19(4):1–22
Puthal D, Obaidat MS, Nanda P, Prasad M, Mohanty SP, Zomaya AY (2018) Secure and sustainable load balancing of edge data centers in fog computing. IEEE Commun Mag 56(5):60–65
Baburao D, Pavankumar T, Prabhu CSR (2021) Load balancing in the fog nodes using particle swarm optimization-based enhanced dynamic resource allocation method. Appl Nanosci 13:1045–1054
Puthal D, Ranjan R, Nanda A, Nanda P, Jayaraman PP, Zomaya AY (2019) Secure authentication and load balancing of distributed edge datacenters. J Parallel Distrib Comput 124:60–69
Hashim FA, Hussain K, Houssein EH, Mabrouk MS, Al-Atabany W (2021) Archimedes optimization algorithm: a new metaheuristic algorithm for solving optimization problems. Appl Intell 51(3):1531–1551
Fathy A, Alharbi AG, Alshammari S, Hasanien HM (2022) Archimedes optimization algorithm based maximum power point tracker for wind energy generation system. Ain Shams Eng J 13(2):101548
Ur Rehman A, Ahmad Z, Jehangiri AI, Ala’Anzy MA, Othman M, Umar AI, Ahmad J (2020) Dynamic energy efficient resource allocation strategy for load balancing in fog environment. IEEE Access 8:199829–199839
https://www.kaggle.com/datasets/uciml/sms-spam-collection-dataset
Funding
The authors declare that they do not have competing interests and funding.
Author information
Authors and Affiliations
Contributions
The author read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The corresponding author states that there is no conflict of interest.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Premkumar, N., Santhosh, R. Secure authentication scheme with Archimedes optimization algorithm for load balancing technique in fog computing. Int. j. inf. tecnol. (2024). https://doi.org/10.1007/s41870-024-01861-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s41870-024-01861-7