Abstract
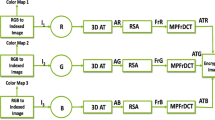
A multi-image encryption method based on singular value decomposition ghost imaging and RSA public-key cryptography (RSVDGI) is proposed. Radon transform (RT) is first carried out on the target images to obtain Radon spectrums, and then, QR encoding is performed on it. The QR-coded image is used as a plaintext image for singular value decomposition ghost imaging (SVDGI) encryption to obtain the corresponding ciphertext. The public key generated by the RSA algorithm is used to encrypt the keys of the above process. Only the receiver with the private key of the RSA algorithm can successfully extract the keys, decrypt the ciphertext encrypted by SVDGI, and finally reconstruct the required target images. QR code has good error correction performance. Thus, it can restore the target images in high quality within the range of its error correction ability. RSA public-key cryptosystem solves the problem of key management in ghost imaging system and improves the security of encryption system. The feasibility, security, and robustness of this method are verified by computer simulations and optical experiments.

















Similar content being viewed by others
References
P. Refregier, B. Javidi, Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 20(7), 767 (1995)
F. Ferri, D. Magatti, L.A. Lugiato et al., Differential ghost imaging. Phys. Rev. Lett. 104(25), 253603 (2010)
Z. Huang, S. Cheng, L. Gong et al., Nonlinear optical multi-image encryption scheme with two-dimensional linear canonical transform. Opt. Lasers Eng. 124, 105821 (2020)
S. Jiao, J. Feng, Y. Gao et al., Visual cryptography in single-pixel imaging. Opt. Express 28(5), 7301 (2020)
C. Duan, J. Zhou, L. Gong et al., New color image encryption scheme based on multi-parameter fractional discrete Tchebyshev moments and nonlinear fractal permutation method. Opt. Lasers Eng. 150, 106881 (2022)
T.B. Pittman, Y.H. Shih, D.V. Strekalov et al., Optical imaging by means of two-photon quantum entanglement. Phys. Rev. A 52(5), 3429 (1995)
R.S. Bennink, S.J. Bentley, R.W. Boyd, Two-Photon coincidence imaging with a classical source. Phys. Rev. Lett. 89(11), 113601 (2002)
A. Gatti, E. Brambilla, M. Bache et al., Ghost imaging with thermal light: comparing entanglement and classical correlation. Phys. Rev. Lett. 93(9), 093602 (2004)
D. Zhang, Y. Zhai, L. Wu et al., Correlated two-photon imaging with true thermal light. Opt. Lett. 30(18), 2354 (2005)
P. Zerom, Z. Shi, M.N. O’Sullivan et al., Thermal ghost imaging with averaged speckle patterns. Phys. Rev. A 86(6), 063817 (2012)
J.H. Shapiro, Computational ghost imaging. Phys. Rev. A 78, 061802 (2008)
P. Clemente, V. Durán, V. Torres-Company et al., Optical encryption based on computational ghost imaging. Opt. Lett. 35(14), 2391 (2010)
O. Katz, Y. Bromberg, Y. Silberberg, Compressive ghost imaging. Appl. Phys. Lett. 95(13), 131110 (2009)
X. Li, X. Meng, X. Yang et al., Multiple-image encryption based on compressive ghost imaging and coordinate sampling. IEEE. Photonics. J. 8(4), 1 (2016)
X. Li, X. Meng, Y. Wang et al., Secret shared multiple-image encryption based on row scanning compressive ghost imaging and phase retrieval in the Fresnel domain. Opt. Lasers Eng. 96, 7 (2017)
Y. Kang, L. Zhang, H. Ye et al., Camouflaged optical encryption based on compressive ghost imaging. Opt. Lasers Eng. 134, 106154 (2020)
S. Zhao, X. Yu, L. Wang et al., Secure optical encryption based on ghost imaging with fractional Fourier transform. Opt. Commun. 474, 126086 (2020)
A. Hazer, R. Yildirim, A review of single and multiple optical image encryption techniques. J. Opt. 23(11), 113501 (2021)
L. Wang, S. Zhao, Fast reconstructed and high-quality ghost imaging with fast Walsh-Hadamard transform. Photonics. Res. 4(6), 240 (2016)
L. Zhang, X. Yuan, K. Wang et al., Multiple-image encryption mechanism based on ghost imaging and public key cryptography. IEEE. Photonics. J. 11(4), 1 (2019)
X. Yuan, L. Zhang, J. Chen et al., Multiple-image encryption scheme based on ghost imaging of Hadamard matrix and spatial multiplexing. Appl. Phys. B 125(9), 174 (2019)
X. Zhang, X. Meng, X. Yang et al., Singular value decomposition ghost imaging. Opt. Express 26(10), 12948 (2018)
S. Wang, X. Meng, Y. Yin et al., Optical image watermarking based on singular value decomposition ghost imaging and lifting wavelet transform. Opt. Lasers Eng. 114, 76 (2019)
X. Liu, X. Meng, Y. Wang et al., Optical multilevel authentication based on singular value decomposition ghost imaging and secret sharing cryptography. Opt. Lasers Eng. 137, 106370 (2021)
S. Zhao, L. Wang, W. Liang et al., High performance optical encryption based on computational ghost imaging with QR code and compressive sensing technique. Opt. Commun. 353, 90 (2015)
P. Kumar, A. Fatima, N.K. Nishchal, Image encryption using phase-encoded exclusive-OR operations with incoherent illumination. J. Opt. 21(6), 065701 (2019)
P. Kumar, N.K. Nishchal, Enhanced exclusive-OR and quick response code-based image encryption through incoherent illumination. Appl. Opt. 58(6), 1408 (2019)
P.A. Cheremkhin, N.N. Evtikhiev, V.V. Krasnov et al., New customizable digital data container for optical cryptosystems. J. Opt. 23(11), 115701 (2021)
Z. Liu, Q. Guo, L. Xu et al., Double image encryption by using iterative random binary encoding in gyrator domains. Opt. Express 18(11), 12033 (2010)
Z. Liu, H. Chen, T. Liu et al., Double-image encryption based on the affine transform and the gyrator transform. J. Opt. 12(3), 035407 (2010)
L. Zhang, Y. Wang, H. Ye et al., Camouflaged encryption mechanism based on sparse decomposition of principal component orthogonal basis and ghost imaging. Opt. Eng. 60(1), 013110 (2021)
Y. Kang, L. Zhang, D. Zhang, Optical encryption based on ghost imaging and public key cryptography. Opt. Lasers Eng. 111, 58 (2018)
Y. Tao, X. Yang, X. Meng et al., Hybrid cryptosystem based on plaintext related computational ghost imaging encryption and elliptic curve algorithm. J. Opt. 22(6), 065701 (2020)
D. Shi, J. Huang, W. Meng et al., Radon single-pixel imaging with projective sampling. Opt. Express 27(10), 14594 (2019)
Y. Kashter, O. Levi, A. Stern, Optical compressive change and motion detection. Appl. Opt. 51(13), 2491 (2012)
H. Hovland, Tomographic scanning imager. Opt. Express 17(14), 11371 (2009)
L. Zhang, Y. Wang, D. Zhang, Research on multiple-image encryption mechanism based on Radon transform and ghost imaging. Opt. Commun. 504, 127494 (2022)
S. Yuan, X. Zhou, M.S. Alam et al., Information hiding based on double random-phase encoding and public-key cryptography. Opt. Express 17(5), 3270 (2009)
N.K. Nishchal, Optical Cryptosystems (Bristol IOP Press, UK, 2019)
T. Zhao, Q. Ran, Y. Chi, Image encryption based on nonlinear encryption system and public-key cryptography. Opt. Commun. 338, 64 (2015)
L. Gong, K. Qiu, C. Deng et al., An optical image compression and encryption scheme based on compressive sensing and RSA algorithm. Opt. Lasers Eng. 121, 169 (2019)
Acknowledgements
This work was supported by the Fundamental Research Funds of Shandong University [grant number 2015GN031], the Bei**g Natural Science Foundation [grant number 4222081], and the National Natural Science Foundation of China under Grant [grant numbers 11574311, 61775121].
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Wang, M., Yang, X., Meng, X. et al. Multi-image encryption based on singular value decomposition ghost imaging and RSA public-key cryptography. J Opt 52, 527–538 (2023). https://doi.org/10.1007/s12596-022-01011-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12596-022-01011-x