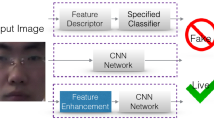
Abstract
Deep learning has seen successful implementation in various domains, such as natural language processing, image classification, and object detection in recent times. In the field of biometrics, deep learning has also been used to develop effective anti-spoofing systems. Facial spoofing, the act of presenting fake facial information to deceive a biometric system, poses a significant threat to the security of face recognition systems. To address this challenge, we propose, in this paper, an effective and robust facial spoofing detection approach based on weighted deep ensemble learning. Our method combines the strengths of two powerful deep learning architectures, DenseNet201 and MiniVGG. The choice of these two architectures is based on a comparative study between DenseNet201, DenseNet169, VGG16, MiniVGG, and ResNet50, where DenseNet201 and MiniVGG obtained the best recall and precision scores, respectively. Our proposed weighted voting ensemble leverages each architecture-specific capabilities to make the final prediction. We assign weights to each classification model based on its performance, which are determined by a mathematical formulation considering the trade-off between recall and precision. To validate the effectiveness of our proposed approach, we evaluate it on the challenging ROSE-Youtu face liveness detection dataset. Our experimental results demonstrate that our proposed method achieves an impressive accuracy rate of 99% in accurately detecting facial spoofing attacks.


Similar content being viewed by others
Availability of data and materials
The research in this project utilized the ROSE-Youtu Face Liveness Detection Dataset, which is a publicly available dataset accessible at the following URL: https://rose1.ntu.edu.sg/dataset/faceLivenessDetection/.
References
Velásquez, I., Caro, A., Rodríguez, A.: Authentication schemes and methods: a systematic literature review. Inf. Softw. Technol. 94, 30–37 (2018)
Oloyede, M.O., Hancke, G.P., Myburgh, H.C.: A review on face recognition systems: recent approaches and challenges. Multimed. Tools Appl. 79(37–38), 27891–27922 (2020)
B. Peixoto, C. Michelassi, and A. Rocha.: Face liveness detection under bad illumination conditions. In IEEE ICIP, (2011)
**, X., Ye, D., Chen, C.: Countering spoof: towards detecting deepfake with multidimensional biological signals. Secur Commun Netw 2021, 1–8 (2021)
Lina, S., Latha, R.: Detecting masquerade in face recognition system—a literature survey. IOSR J. Comput. Eng. 16, 01–05 (2014)
Duc, N.M., Minh, B.Q.: Your face is not your password. In: Black Hat Conference (2009)
Frischholz, R.W., Dieckmann, U.: Bioid: a multimodal biometric identification system. Computer 33(2), 64–68 (2000)
Sun, L., Huang, W., Wu, M.: Tir/vis correlation for liveness detection in face recognition. In: Proceedings of the 14th International Conference on Computer Analysis of Images and Patterns- Volume Part II, CAIP’11, pp. 114–121. Springer-Verlag, Berlin, Heidelberg (2011).
hang, Z., Yi, D., Lei, Z., Li, S.Z.: Face liveness detection by learning multispectral reflectance distributions. In: International Conference on Face and Gesture, pp. 436–441 (2011)
M. M. Chakka et al.: Competition on counter measures to 2-D facial spoofing attacks. In: 2011 International Joint Conference on Biometrics (IJCB), Washington, DC, USA, 2011, pp. 1–6, https://doi.org/10.1109/IJCB.2011.6117509.
Chetty, G., Wagner, M.: Liveness verification in audio-video speaker authentication. In: Procedings of 10th ASSTA Conference, pp. 358–363. Macquarie University Press (2004)
Haudhry, R., Ravich, A., Hager, G., Vidal, R.: Histograms of oriented optical flow and binet- cauchy kernels on nonlinear dynamical systems for the recognition of human actions. In: IEEE Conference on Computer Vision and Pattern Recognition (CVPR) (2009)
Dalal, N., Triggs, B.: Histograms of oriented gradients for human detection. In: International Conference on Computer Vision and Pattern Recognition, vol. 2, pp. 886–893 (2005)
J. Stehouwer, A. Jourabloo, Y. Liu, X. Liu: Noise modelling, synthesis and classification for generic object anti-spoofing. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, pp.7292–7301 (2020)
Kollreider, K., Fronthaler, H., Faraj, M.I., Bigun, J.: Real-time face detection and motion analysis with application in liveness assessment. Trans. Info. For. Sec. 2(3), 548–558 (2007)
Yang, J., Zhen L., and Stan Z. L.: Learn convolutional neural network for face anti-spoofing (2014). https://arxiv.org/abs/1408.5601
Zhang, K., Zhang, Z., Li, Z., Qiao, Y.: Joint face detection and alignment using multitask cascaded convolutional networks. IEEE Signal Process. Lett. 23(10), 1499–1503 (2016). https://doi.org/10.1109/LSP.2016.2603342
Lucena, O., Junior, A., Moia, V., Souza, R., Valle, E., Lotufo, R.: Transfer learning using convolutional neural networks for face anti-spoofing. In: Karray, F., Campilho, A., Cheriet, F. (eds) Image Analysis and Recognition. ICIAR 2017. Lecture Notes in Computer Science, vol. 10317. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-59876-5_4
Zhang, G., Meng, W., Ma, X., Shi, Y.: LSTM Network based spoofing detection and recognition in a GNSS receiver. In: Sun, J., Yang, C., **e, J. (eds) China Satellite Navigation Conference (CSNC) 2020 Proceedings: Volume III. CSNC 2020. Lecture Notes in Electrical Engineering, vol. 652. Springer, Singapore (2020) https://doi.org/10.1007/978-981-15-3715-8_55
Muhammad, U., Holmberg, T., Melo, W.C., & Hadid, A.: Face anti-spoofing via sample learning based recurrent neural network (RNN). In: British Machine Vision Conference (2019)
Gomez-Alanis, A., Gonzalez-Lopez, J.A., Peinado, A.M.: GANBA: generative adversarial network for biometric anti-spoofing. Appl. Sci. 12(3), 1454 (2022). https://doi.org/10.3390/app12031454
Yi S., Kemal D., and Yalin E. S.: Generative adversarial network for wireless signal spoofing. In: Proceedings of the ACM Workshop on Wireless Security and Machine Learning (WiseML 2019), pp. 55–60. Association for Computing Machinery, New York, NY, USA (2019) https://doi.org/10.1145/3324921.3329695
Kong, Y., **nyuan, L., Guangye, H., Chu, L.: Face anti-spoofing method based on residual network with channel attention mechanism. Electronics 11(19), 3056 (2022). https://doi.org/10.3390/electronics11193056
Bazarevsky, V., Kartynnik, Y., Vakunov, A., Raveendran, K., & Grundmann, M.: Blazeface: sub-millisecond neural face detection on mobile gpus (2019). https://arxiv.org/abs/1907.05047
Abdelouahed, S. M., Assia, E., & Abdellah, A.: A comparative study of anti-spoofing detection based on deep learning. In: 2023 3rd International Conference on Innovative Research in Applied Science, Engineering and Technology (IRASET), Mohammedia, Morocco, pp. 1–6 (2023) https://doi.org/10.1109/IRASET57153.2023.10152955.
Li, H., Li, W., Cao, H., Wang, S., Huang, F., Kot, A.C.: Unsupervised domain adaptation for face anti-spoofing. IEEE Trans. Inf. Forensics Secur. 13(7), 1794–1809 (2018)
Hasan, M. M., Yusuf, M. S. U., Rohan, T. I., & Roy, S.: Efficient two stage approach to detect face liveness: motion based and deep learning based. In: 2019 4th International Conference on Electrical Information and Communication Technology (EICT), Khulna, Bangladesh, pp. 1–6 (2019) https://doi.org/10.1109/EICT48899.2019.9068813.
Alassafi, M. O., Ibrahim, M. S., Naseem, I., AlGhamdi, R., Alotaibi, R., Kateb, F. A., Yusuf, S. A.: A novel deep learning architecture with image diffusion for robust face presentation attack detection. IEEE Access. (2023). https://doi.org/10.1109/ACCESS.2023.3285826.
Funding
This research received no specific grant from any funding agency in the public, commercial, or not-for-profit sectors.
Author information
Authors and Affiliations
Contributions
All authors made substantial contributions to the concept, design, and revision of the paper. AS, AE and AA revise and conceptualized the research idea, formulated the research objectives, and designed the experimental methodology. AS and AE wrote the main manuscript text. AS and AA contributed to the development and implementation.
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that they have no conflicts of interest.
Ethical approval
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Sabri, M.A., Ennouni, A. & Aarab, A. An effective facial spoofing detection approach based on weighted deep ensemble learning. SIViP 18, 935–942 (2024). https://doi.org/10.1007/s11760-023-02818-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11760-023-02818-2