Abstract
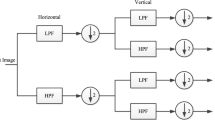
Although wavelet-based steganography techniques are widely used due to their advantages, complete embedding data extraction remains one of the most significant challenges in this field. The Integer Wavelet Transform (IWT) can reduce extraction errors by map** the image to integers, but it does not fully eliminate them. The proposed method resolves these errors entirely by using an iterative embedding procedure. After determining the image blocks and performing the IWT, this method embeds data in high-frequency sub-bands coefficient pairs. Additionally, it modifies the coefficient pair values such that the XOR of two coefficient LSBs equals two bits of data. The genetic algorithm is used to generate new coefficient values in order to minimize the differences between the stego and cover images. The sender repeats the embedding operation on each block until all extraction errors have been eliminated. If this procedure is unsuccessful in a block, the sender signs it as empty block. The results of the implementation suggest that with each iteration, the errors typically diminish to zero in most of the blocks. Further examination of the test results shows an enhancement in the PSNR and SSIM metrics when contrasted with existing methods. Moreover, the test results also expose the inability of attacks to uncover this method. Key merits of the proposed method include its superior stego image quality, substantial security against attacks, no requirement for lengthy keys, and a zero extraction error rate. These features render this method highly viable for practical applications.















Similar content being viewed by others
Data availability
Not applicable.
Code availability
Not applicable.
References
Al-Dmour H, Al-Ani A (2016) A steganography embedding method based on edge identification and XOR coding. Expert Syst Appl 46:293–306. https://doi.org/10.1016/j.eswa.2015.10.024
Atawneh S, Almomani S, Al Bazar A, Sumari H, Gupta P (2017) Secure and imperceptible digital image steganographic algorithm based on diamond encoding in DWT domain. Multimed Tools Appl 76(18):18451–18472. https://doi.org/10.1007/s11042-016-3930-0
Atee HA, Ahmad R, Mohd Noor N, Monem Rahma AS, Aljeroudi Y (2017) Extreme learning machine based optimal embedding location finder for image steganography. PLoS ONE 12(2):e0170329. https://doi.org/10.1371/journal.pone.0170329
Atta R, Ghanbari M (2018) A high payload steganography mechanism based on wavelet packet transformation and neutrosophic set. J Vis Commun Image Represent 53:42–54. https://doi.org/10.1016/j.jvcir.2018.03.009
Calderbank AR, Daubechies I, Sweldens W, Yeo BL (1998) Wavelet transforms that map Integers to Integers. Appl Comput Harmon Anal 5(3):332–369. https://doi.org/10.1006/ACHA.1997.0238
Denemark T, Sedighi V, Holub V, Cogranne R, Fridrich J (2014) Selection-channel-aware rich model for steganalysis of digital images. 2014 IEEE Int Work Inf Forensics Secur 48–53. https://doi.org/10.1109/WIFS.2014.7084302
El-Emam NN (2015) New data-hiding algorithm based on adaptive neural networks with modified particle swarm optimization. Comput Secur 55:21–45. https://doi.org/10.1016/J.COSE.2015.06.012
El Safy RO, Zayed HH, El Dessouki A (2009) An adaptive steganographic technique based on integer wavelet transform. In 2009 International Conference on Networking and Media Convergence: 111–117. https://doi.org/10.1109/ICNM.2009.4907200
Evsutin O, Kokurina A, Meshcheryakov R, Shumskaya O (2018) The adaptive algorithm of information unmistakable embedding into digital images based on the discrete Fourier transformation. Multimed Tools Appl 77(21):28567–28599. https://doi.org/10.1007/S11042-018-6055-9
Evsutin O, Melman A, Meshcheryakov R (2021) Algorithm of error-free information embedding into the DCT domain of digital images based on the QIM method using adaptive masking of distortions. Signal Process 179:107811. https://doi.org/10.1016/J.SIGPRO.2020.107811
Fakhredanesh M, Rahmati M, Safabakhsh R (2019) Steganography in discrete wavelet transform based on human visual system and cover model. Multimed Tools Appl 78(13):18475–18502. https://doi.org/10.1007/S11042-019-7238-8/METRICS
Fridrich J, Goljan M, Hogea D (2003) New methodology for breaking steganographic techniques for JPEGs. Proc SPIE 5020:143–155. https://doi.org/10.1117/12.473142
Gaurav K, Ghanekar U (2018) Image steganography based on Canny edge detection, dilation operator and hybrid coding. J Inf Secur Appl 41:41–51. https://doi.org/10.1016/J.JISA.2018.05.001
Gulve AK, Joshi M (2015) An image steganography method hiding secret data into coefficients of integer wavelet transform using pixel value differencing approach. Math Probl Eng 2015:684824. https://doi.org/10.1155/2015/684824
Kadhim IJ, Premaratne P, Vial PJ (2018) Adaptive image steganography based on edge detection over dual-tree complex wavelet transform. In: International Conference on Intelligent Computing Methodologies: 544–550. https://doi.org/10.1007/978-3-319-95957-3_57
Kadhim IJ, Premaratne P, Vial PJ, Halloran B (2019) Comprehensive survey of image steganography: techniques, evaluations, and trends in future research. Neurocomputing 335:299–326. https://doi.org/10.1016/j.neucom.2018.06.075
Kadhim IJ, Premaratne P, Vial PJ (2020) Improved image steganography based on super-pixel and coefficient-plane-selection. Sig Process 171:107481. https://doi.org/10.1016/j.sigpro.2020
Kalita M, Tuithung T, Majumder S (2019) A new steganography method using integer wavelet transform and least significant bit substitution. Comput J 62(11):1639–1655. https://doi.org/10.1093/comjnl/bxz014
Kumar V, Kumar D (2018) A modified DWT-based image steganography technique. Multimed Tools Appl 77(11):13279–13308. https://doi.org/10.1007/S11042-017-4947-8
Kumar S, Singh A, Kumar M (2019) Information hiding with adaptive steganography based on novel fuzzy edge identification. Def Technol 15(2):162–169. https://doi.org/10.1016/J.DT.2018.08.003
Laishram D, Tuithung T (2021) A novel minimal distortion-based edge adaptive image steganography scheme using local complexity. Multimed Tools Appl 80(1):831–854. https://doi.org/10.1007/s11042-020-09519-9
Mandal PC, Mukherjee I (2021) Integer wavelet transform based secured image steganography using LSB and coefficient value differencing. Int Conf Secur Cyber Comput Commun :332–337. https://doi.org/10.1109/ICSCCC51823.2021.9478095
Mandal PC, Mukherjee I, Chatterji BN (2021) High capacity steganography based on IWT using eight-way CVD and n-LSB ensuring secure communication. Optik 247:167804. https://doi.org/10.1016/J.IJLEO.2021.167804
Mandal PC, Mukherjee I, Paul G, Chatterji BN (2022) Digital image steganography: a literature survey. Inf Sci 609:1451–1488. https://doi.org/10.1016/J.INS.2022.07.120
Miri A, Faez K (2017) Adaptive image steganography based on transform domain via genetic algorithm. Optik 145:158–168. https://doi.org/10.1016/j.ijleo.2017.07.043
Miri A, Faez K (2018) An image steganography method based on integer wavelet transform. Multimed Tools Appl 77(11):13133–13144. https://doi.org/10.1007/s11042-017-4935-z
Muhuri PK, Ashraf Z, Goel S (2020) A novel image steganographic method based on integer wavelet transformation and particle swarm optimization. Appl Soft Comput J 92:106257. https://doi.org/10.1016/j.asoc.2020.106257
Pramanik S, Singh RP, Ghosh R (2020) Application of bi-orthogonal wavelet transform and genetic algorithm in image steganography. Multimed Tools Appl 79(25):17463–17482. https://doi.org/10.1007/s11042-020-08676-1
Ray B, Mukhopadhyay S, Hossain S, Ghosal SK, Sarkar R (2021) Image steganography using deep learning based edge detection. Multimed Tools Appl 80(24):33475–33503. https://doi.org/10.1007/S11042-021-11177-4
Sabeti V, Amerehei M (2021) Secure and imperceptible image steganography in discrete wavelet transform using the xor logical function and genetic algorithm. ISC Int J Inf Secur 14(2):167–179. https://doi.org/10.22042/isecure.2022.274305.641
Sabeti V, Samavi S, Shirani S (2013) An adaptive LSB matching steganography based on octonary complexity measure. Multimed Tools Appl 64(3):777–793. https://doi.org/10.1007/s11042-011-0975-y
Sabeti V, Aghabagheri A (2022) Develo** an adaptive DCT-based steganography method using a genetic algorithm. Multimed Tools Appl 82(13):19323–19346. https://doi.org/10.1007/S11042-022-14166-3/METRICS
Sabeti V, Sobhani M, Hasheminejad SMH (2022) An adaptive image steganography method based on integer wavelet transform using genetic algorithm. Comput Electr Eng 99:107809. https://doi.org/10.1016/J.COMPELECENG.2022.107809
Shafi I et al (2018) An adaptive hybrid fuzzy-wavelet approach for image steganography using bit reduction and pixel adjustment. Soft Comput 22(5):1555–1567. https://doi.org/10.1007/S00500-017-2944-5/METRICS
Shah PD, Bichkar RS (2021) Secret data modification based image steganography technique using genetic algorithm having a flexible chromosome structure. Eng Sci Technol Int J 24(3):782–794. https://doi.org/10.1016/J.JESTCH.2020.11.008
Subhedar MS, Mankar VH (2014) Current status and key issues in image steganography: a survey. Comput Sci Rev 13:95–113. https://doi.org/10.1016/j.cosrev.2014.09.001
Tang L, Wu D, Wang H, Chen M, **e J (2021) An adaptive fuzzy inference approach for color image steganography. Soft Comput 25(16):10987–11004. https://doi.org/10.1007/S00500-021-05825-Y
Valandar MY, Barani MJ, Ayubi P, Aghazadeh M (2019) An integer wavelet transform image steganography method based on 3D sine chaotic map. Multimed Tools Appl 78(8):9971–9989. https://doi.org/10.1007/s11042-018-6584-2
Wang w, Li Q (2022) An image steganography algorithm based on PSO and IWT for underwater acoustic communication. IEEE Access 10:107376–107385. https://doi.org/10.1109/ACCESS.2022.3212691
Zhang H, Hu L (2019) A data hiding scheme based on multidirectional line encoding and integer wavelet transform. Signal Process Image Commun 78:331–344. https://doi.org/10.1016/j.image.2019.07.019
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no financial or proprietary interests in any material discussed in this article.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Sabeti, V. Unmistakable information embedding into the integer wavelet transform domain of an image using an XOR function and a genetic algorithm. Multimed Tools Appl 83, 23655–23688 (2024). https://doi.org/10.1007/s11042-023-16466-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-16466-8